

Macro-based automation is for environments of varying host types that (1) are not using Kerberos for network authentication and (2) already have a network security application in place. As the name implies, it requires you to create a macro to perform logon automation.
Host On-Demand provides out-of-the-box support for the following three network security applications without requiring additional coding:
If you have a different network security application, you will need to create your own plug-in to work in your environment. For more information, refer to Customizing Web Express Logon (opens new browser).
Macro-based automation relies on the following four key components and the interactions that take place among them:
The CMS is supplied with Host On-Demand and must be deployed to a J2EE-compliant Web application server. At a high level, the CMS is responsible for the following tasks: (1) determine the client's identity (called a network ID (opens new browser)), (2) map the user's network ID to the host ID (opens new browser), and (3) return the host credentials to the client as an XML document.
The login macro automates the end-to-end process of the client sending the HTTPS request to the CMS, the CMS responding with the needed credentials, and the macro inserting the user's credentials in the proper fields to allow authenticated logon. You must record the login macro while you are in an active session. It initiates at the time the user attempts to access the host session, either automatically or manually (depending on your configuration).
Host On-Demand provides two Network Security plug-ins, one for Tivoli Access Manager and one for Netegrity Siteminder. The Network Security plug-in does not apply to Microsoft Active Directory since the Windows login ID is used as the network ID. The primary function of the Network Security plug-in is to acquire the user's network ID, which may be gleaned from the HTTP header of the incoming HTTP request object.
The HCM database is a back-end repository that maps users' network IDs to their host IDs. This repository can be a JDBC database such as IBM DB2. The Digital Certificate Access Server (DCAS) and Vault plug-ins provided with Web Express Logon are designed to work with such a database. Another possibility for a repository is an LDAP directory. However, using LDAP as your HCM database requires you to write your own plug-in. For more information, refer to Customizing Web Express Logon (opens new browser).
The following graphic shows you the key components discussed above and how they interact together to achieve logon automation. It illustrates the overall flow of macro-based automation beginning at the point when a user attempts to open a Host On-Demand session and initiates the login macro. If the macro is not configured to auto-start, the user will need to start it manually.
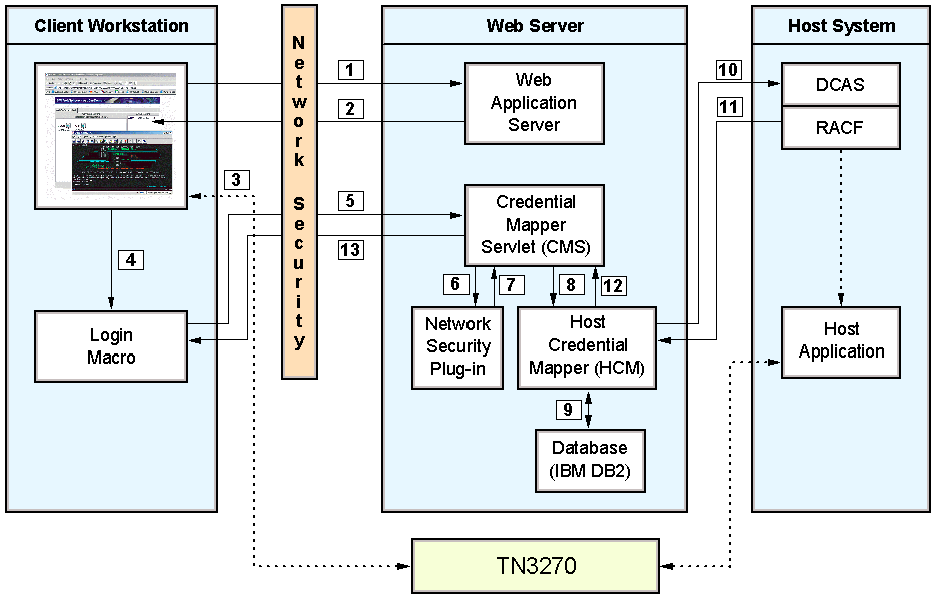
The login macro automatically inserts the user's credentials in the logon screen fields without user intervention. Now the user is fully authenticated and can proceed with the session.
Click Next for an overview of connection-based automation.