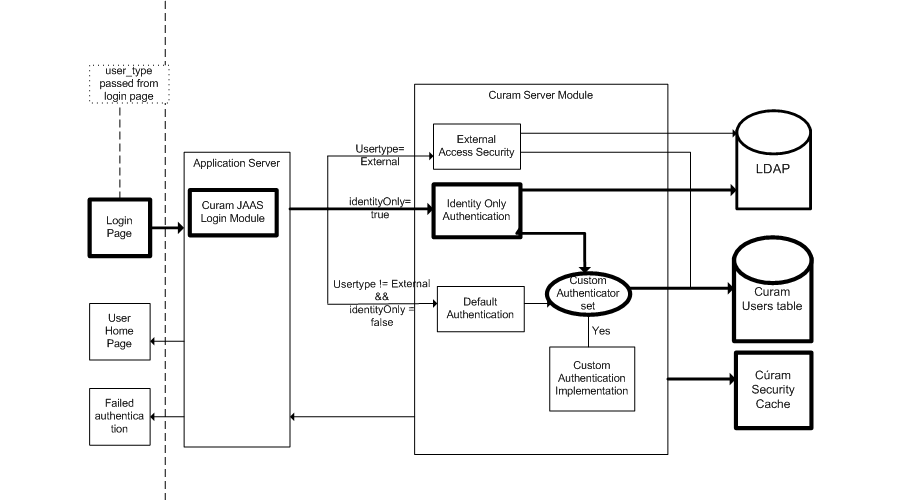
Authentication can be configured to perform identity-only verification, in place of the default verifications listed in Default Verification Process above.
Identity only verification means that the authentication mechanism only ensures that the username for the user logging in exists on the Cúram Users database table. Full authentication must be completed by an alternative mechanism, to be configured in the application server.
An example of an alternative mechanism is an LDAP directory server, which is supported as an authentication mechanism by both the WebSphere® and WebLogic Server application servers. Another alternative is to use a Single Sign-On Solution for authentication, or to implement a custom login module. For custom application server solutions the IBM or Oracle documentation should be consulted.
With identity-only authentication (as for default authentication), entries are added to the AuthenticationLog database table at the end of the authentication process.
For a successful login the following status is used:
- AUTHONLY
For a failure scenario, the following status is used:
- BADUSER
This is the only possible failure scenario where a user does not exist.
The loginFailures and lastLogin fields of the AuthenticationLog are not set. This is true even if customized verifications are implemented.
When the password expiry information for a user is set (on the Cúram Users database table), the password expiry warning will be displayed if it is about to expire. With identity-only authentication this warning is misleading. It is recommended that any fields relating to the authentication verifications, such as password expiry or account enabled, are not used if identity-only authentication is enabled.
When identity-only authentication is enabled, security is not used for authentication but is still used for authorization purposes. As a result of this, all users requiring access to the application must still exist in the Cúram Users database table, as well as in the alternative authentication mechanism, e.g., LDAP. It is important to note that there are two users that must exist in both locations, i.e. the SYSTEM user and the DBTOJMS user. Security for Alternative Clients should be consulted for further details on these users.
Configuring Identity Only Authentication should be consulted for details on how to configure identity only for an application server.