| Note |
|---|
|
Before using this information and the product it supports, read the general information under Appendix F, Notices. |
First Edition (November 2002)
This edition applies to version 5, release 1, of the IBM(R) Directory Server and to all subsequent releases and modifications until otherwise indicated in new editions.
(C) Copyright International Business Machines Corporation 2002. All rights reserved.
U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp.
This document contains the information that you need to administer the IBM Directory Server.
A directory is a collection of information about objects arranged in a hierarchical structure. It is a specialized database, that enables users or applications to find resources that have the characteristics needed for a particular task.
If the name of an object is known, its characteristics can be retrieved. If the name of a particular individual object is not known, the directory can be searched for a list of objects that meet a certain requirement. Directories can usually be searched by specific criteria, not just by a predefined set of categories.
A directory is a specialized database that has characteristics that set it apart from general purpose relational databases. A characteristic of a directory is that it is accessed (read or searched) much more often than it is updated (written). Because directories must be able to support high volumes of read requests, they are typically optimized for read access. Because directories are not intended to provide as many functions as general-purpose databases, they can be optimized to economically provide more applications with rapid access to directory data in large distributed environments.
A directory can be centralized or distributed. If a directory is centralized, there is one directory server (or a server cluster) at one location that provides access to the directory. If the directory is distributed, there are more than one server, usually geographically dispersed, that provide access to the directory.
When a directory is distributed, the information stored in the directory can be partitioned or replicated. When information is partitioned, each directory server stores a unique and non-overlapping subset of the information. That is, each directory entry is stored by one and only one server. The technique to partition the directory is to use LDAP referrals. LDAP referrals allow the users to refer Lightweight Directory Access Protocol (LDAP) requests to either the same or different name spaces stored in a different (or same) server. When information is replicated, the same directory entry is stored by more than one server. In a distributed directory, some information may be partitioned, and some information may be replicated.
Directories are usually accessed using the client-server model of communication. The client and server processes might or might not be on the same machine. A server is capable of serving many clients. An application that wants to read or write information in a directory does not access the directory directly. Instead, it calls a function or application programming interface (API) that causes a message to be sent to another process. This second process accesses the information in the directory on behalf of the requesting application. The results of the read or write are then returned to the requesting application.
An API defines the programming interface a particular programming language uses to access a service. The format and contents of the messages exchanged between client and server must adhere to an agreed upon protocol. LDAP defines a message protocol used by directory clients and directory servers. There is also an associated LDAP API for the C language and ways to access the directory from a Java(TM) application using the Java Naming and Directory Interface (JNDI).
A directory should support the basic capabilities needed to implement a security policy. The directory might not directly provide the underlying security capabilities, but it might be integrated with a trusted network security service that provides the basic security services. First, a method is needed to authenticate users. Authentication verifies that users are who they say they are. A user name and password is a basic authentication scheme. Once users are authenticated, it must be determined if they have the authorization or permission to perform the requested operation on the specific object.
Authorization is often based on access control lists (ACLs). An ACL is a list of authorizations that may be attached to objects and attributes in the directory. An ACL lists what type of access each user or a group of users is allowed or denied. In order to make ACLs shorter and more manageable, users with the same access rights are often put into groups.
The IBM Directory implements the Internet Engineering Task Force (IETF) LDAP V3 specifications. It also includes enhancements added by IBM in functional and performance areas. This version uses the IBM DB2(R) as the backing store to provide per LDAP operation transaction integrity, high performance operations, and on-line backup and restore capability. It interoperates with the IETF LDAP V3 based clients. Major features include:
The preferred method of administering the server is by using the Web Administration GUI.
The directory administration daemon enables remote management of the IBM Directory Server. It must be installed on the machine where the IBM Directory Server is installed and be running continuously. The directory administration daemon accepts requests by way of LDAP extended operations and supports starting, stopping, restarting and status monitoring of the IBM Directory Server. By default, the IBM Directory administration daemon listens on two ports, port 3538 for non-SSL connections and port 3539 for SSL connections, if SSL communication is enabled.
Unlike the previous releases in which the Server Administration GUI had to be installed on the same machine as the directory server, the IBM Directory Server Version 5.1 Web Administration tool is installed on an application server, such as the embedded version of IBM WebSphere(R) Application Server - Express included with the IBM Directory Server, and administered through a console. Servers that have been added to the console can utilize the Web Administration tool without having to have the tool installed.
Before you can start using the Web Administration Tool, ensure that you have the completed the following prerequisites during the configuration of your server:
See the IBM Directory Server Version 5.1 Installation and Configuration Guide for information on these tasks.
Notes:
If you have installed the Web Administration package start the application server. For the embedded version of IBM WebSphere Application Server - Express go to the directory where you installed the IBM Directory Server and issue the command:
<IDSinstalldir>/ldap/appsrv/bin/startServer.sh server1
<IDSinstalldir>\ldap\appsrv\bin\startServer.bat server1
Open a Web browser and type the following address: http://localhost:9080/IDSWebApp/IDSjsp/Login.jsp. The IBM Directory Server Web Administration login page panel is displayed.
The IBM Directory Server Web Administration Tool panel is displayed.
At the IBM Directory Server Web Administration Tool panel:
At the Logout successful panel that is displayed when you exit Console administrator, you see the message:
If you have been accidentally logged out then you will need to re-login by clicking here.
Click the word here to go to the IBM Directory Server Web Administration Login Page.
After the tool has been started, the application window has five parts:
Every entry in the directory has a distinguished name (DN). The DN is the name that uniquely identifies an entry in the directory. A DN is made up of attribute=value pairs, separated by commas, for example:
cn=Ben Gray,ou=editing,o=New York Times,c=US cn=Lucille White,ou=editing,o=New York Times,c=US cn=Tom Brown,ou=reporting,o=New York Times,c=US
Any of the attributes defined in the directory schema may be used to make up a DN. The order of the component attribute value pairs is important. The DN contains one component for each level of the directory hierarchy from the root down to the level where the entry resides. LDAP DNs begin with the most specific attribute (usually some sort of name), and continue with progressively broader attributes, often ending with a country attribute. The first component of the DN is referred to as the Relative Distinguished Name (RDN). It identifies an entry distinctly from any other entries that have the same parent. In the examples above, the RDN "cn=Ben Gray" separates the first entry from the second entry, (with RDN "cn=Lucille White"). These two example DNs are otherwise equivalent. The attribute:value pair making up the RDN for an entry must also be present in the entry. (This is not true of the other components of the DN.)
Follow this example to create a distinguished name in the ibmslapd.conf file:
DN: cn=Directory,cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration ibm-slapdDbName: <databasename> ibm-slapdUserID: <username> ibm-slapdDbUserPW: <password> ibm-slapdDbInstance: <username>
The Distinguished Name (DN) syntax supported by this server is based on RFC 2253. The Backus Naur Form (BNF) syntax is defined as follows:
<name> ::= <name-component> ( <spaced-separator> )
| <name-component> <spaced-separator> <name>
<spaced-separator> ::= <optional-space>
<separator>
<optional-space>
<separator> ::= "," | ";"
<optional-space> ::= ( <CR> ) *( " " )
<name-component> ::= <attribute>
| <attribute> <optional-space> "+"
<optional-space> <name-component>
<attribute> ::= <string>
| <key> <optional-space> "=" <optional-space> <string>
<key> ::= 1*( <keychar> ) | "OID." <oid> | "oid." <oid>
<keychar> ::= letters, numbers, and space
<oid> ::= <digitstring> | <digitstring> "." <oid>
<digitstring> ::= 1*<digit>
<digit> ::= digits 0-9
<string> ::= *( <stringchar> | <pair> )
| '"' *( <stringchar> | <special> | <pair> ) '"'
| "#" <hex>
<special> ::= "," | "=" | <CR> | "+" | "<" | ">"
| "#" | ";"
<pair> ::= "\" ( <special> | "\" | '"')
<stringchar> ::= any character except <special> or "\" or '"'
<hex> ::= 2*<hexchar>
<hexchar> ::= 0-9, a-f, A-F
A semicolon (;) character can be used to separate RDNs in a distinguished name, although the comma (,) character is the typical notation.
White-space characters (spaces) might be present on either side of the comma or semicolon. The white-space characters are ignored, and the semicolon is replaced with a comma.
In addition, space (' ' ASCII 32) characters may be present either before or after a '+' or '='. These space characters are ignored when parsing.
A value may be surrounded by double quotation ('"' ACSII 34) characters, which are not part of the value. Inside the quoted value, the following characters can occur without any escaping:
Alternatively, a single character to be escaped may be prefixed by a backslash ('\' ASCII 92). This method can be used to escape any of the characters listed previously and the double quotation marks ('"' ASCII 34) character.
This notation is designed to be convenient for common forms of names. The following example is a distinguished name written using this notation. First is a name containing three components. The first of the components is a multivalued RDN. A multivalued RDN contains more than one attribute:value pair and can be used to distinctly identify a specific entry in cases where a simple CN value might be ambiguous:
OU=Sales+CN=J. Smith,O=Widget Inc.,C=US
A DN can contain special characters. These characters are , (comma), = (equals), + (plus), < (less than), > (greater than), # (number sign), ; (semicolon), \ (backslash), and "" (quotation marks).
To escape these special characters or other characters in an attribute value in a DN string, use the following methods:
CN=L. Eagle,O=Sue\, Grabbit and Runn,C=GB
This is the preferred method.
CN=L. Eagle,O=Sue\2C Grabbit and Runn,C=GB
"you need to escape a single backslash this way \\"
Another example, "\Zoo" is illegal, because 'Z' cannot be escaped in this context.
On the server end, when a DN is received in this form, the server reformats the DN using escape mechanisms number 1 and 2 for internal processing.
Pseudo DNs are used in access control definition and evaluation. The LDAP/DB2 directory contains several pseudo DNs (for example, "group:cn=this" and "access-id:cn=Anybody"), which are used to refer to large numbers of DNs that share a common characteristic, in relation to either the operation being performed or the object on which the operation is being performed.
Three pseudo DNs are supported by LDAP version 3:
When specified as part of an ACL, this DN refers to the bindDN, which matches the DN on which the operation is performed. For example, if an operation is performed on the object "cn=personA, ou=IBM, c=US" and the bindDn is "cn=personA, ou=IBM, c=US", the permissions granted are a combination of those given to "cn=this" and those given to "cn=personA, ou=IBM, c=US".
When specified as part of an ACL, this DN refers to all users, even those that are unauthenticated. Users cannot be removed from this group, and this group cannot be removed from the database.
This DN refers to any DN that has been authenticated by the directory. The method of authentication is not considered.
Some examples of pseudo DNs:
access-id: cn = this:critical:rwsc AclEntry: group: cn=Anybody: normal:rsc AclEntry: group: cn=Authenticated: sensitive:rcs
| User Binding as | Would receive |
|---|---|
| cn=personA, c=US | normal:rsc:sensitive:rcs:critical:rwsc |
| cn=personB, c=US | normal:rsc:sensitive:rsc |
| NULL (unauth.) | normal:rsc |
In this example, personA receives permissions granted to the "cn=this" ID, and permissions given to both the "cn=Anybody" and "cn=Authenticated" pseudo DN groups.
AclEntry: access-id: cn = this:critical:rwsc AclEntry: group: cn=Anybody: normal:rsc AclEntry: group: cn=Authenticated: sensitive:rcs
For an operation performed on cn=personA, c=US:
| User Binding as | Would receive |
|---|---|
| cn=personA, c=US | object:ad:critical:rwsc |
| cn=personB, c=US | normal:rsc:sensitive:rsc |
| NULL (unauth.) | normal:rsc |
In this example, personA receives permissions granted to the "cn=this" ID, and those given to the DN itself "cn=personA, c=US". Note that the group permissions are not given because there is a more specific aclentry ("access-id:cn=personA, c=US") for the bind DN ("cn=personA, c=US").
A composite RDN of a DN may consist of multiple components connected by the '+' operators. The server enhances the support for searches on entries that have such a DN. A composite RDN can be specified in any order as the base for a search operation.
ldapsearch cn=mike+ou=austin,o=ibm,c=us
The server accepts DN normalization extended operations. DN normalization extended operations normalize DNs using the server schema. This extended operation might be useful for applications that use DNs. See the IBM Directory Server Version 5.1 C-client Programming Reference for more information.
The following tasks can be performed by the directory administrator:
The administrator name and password is usually set during the server installation and configuration process. However, you can change an administrator name and an administrator password by using either the Web Administration Tool or the command line.
Click User properties in the navigation area of the Web Administration Tool. Two selections are displayed:
You can use either the ldapcfg command or the ldapxcfg utility from the command line.
Using the ldapcfg command:
ldapcfg -u <admindn> -p <adminpassword>
To use the ldapxcfg utility type ldapxcfg on a command line. When the IBM Directory Server Configuration Tool panel is displayed select Administrator DN/password and follow the directions. See the IBM Directory Server Version 5.1 Installation and Configuration Guide for additional information on using the ldapxcfg utility.
See Distinguished names (DNs) for more information about distinguished names.
You can check the status of the server by searching for the object classes under cn=monitor. To do this, use one of the following methods:
Expand the Server administration category in the navigation area. Click View server status. If the directory server is running, the following information is displayed:
year-month-day hour:minutes:seconds GMT
day-month-date hour:minutes:seconds timezone year
year month day hour:minutes:seconds GMT
day month date hour:minutes:seconds timezone year
ldapsearch -h <servername> -p <portnumber> -b cn=monitor -s base objectclass=*
This command returns the following information:
year month day hour:minutes:seconds GMT
day month date hour:minutes:seconds timezone year
year month day hour:minutes:seconds GMT
day month date hour:minutes:seconds timezone year
Perform the following to check the connection status of the server.
Click View server connections in the navigation area. A table containing the following information is displayed:
Notes:
ldapsearch -D<adminDN> -w <adminPW> -h <servername> -p <portnumber>
-b cn=connections,cn=monitor -s base objectclass=*
This command returns information in the following format:
cn=connections,cn=monitor connection=1632 : 2002-10-05 19:18:21 GMT : 1 : 1 : CN=ADMIN : connection=1487 : 2002-10-05 19:17:01 GMT : 1 : 1 : CN=ADMIN :
You can use either of the following methods to start or stop the server.
The current status of the server, either started, stopped or started in configuration mode, is indicated by the icons in the upper left-hand corner of the server status area. The current status is also described in the first sentence of the work area, for example
The Directory Server is currently running
| Server status | Buttons available |
|---|---|
| Stopped | Start, Close |
| Running | Stop, Restart, Close |
| Running in configuration only mode | Stop, Restart, Close |
If you need to perform server configuration maintenance, select the Start / Restart in configuration only mode check box. In this mode only the system administrator can bind to the server. All other connections are refused until the server is restarted with DB2 backends enabled (the Start / Restart in configuration only mode check box deselected). See Configuration only mode for additional information.
Use the following command to start and stop the server:
ibmdirctl [-h <hostname>] [-D <adminDN>] [-w <password>] [-p <portnumber>] start|stop|restart|status -- [ibmslapd options]
See ibmdirctl for additional information.
For Windows(R) systems use the previous command or:
The IBM Directory Server supports LDAP access to the server's configuration settings. An administrator can use LDAP protocol to query and update the configuration for the server. This feature enables remote administration. In order for this access to be more robust and reliable, the server does not depend on successful initialization of the database backends. It is possible to start the server in configuration only mode with only the cn=configuration suffix active. In other words, as long as the configuration backend is available, the server starts and accepts LDAP requests. Configuration only mode gives an administrator remote access to the server even when errors are encountered during startup.
The following features are supported in configuration only mode:
The following features are not supported in configuration only mode:
ibmslapd -aor
ibmdirctl -h <hostname> -D <adminDN> -w <password>-p <portnumber> start -- -a
ldapsearch -s base -b " " objectclass=* ibm-slapdisconfigurationmode
This section discusses how to set up the various properties for your server.
Examples that are provided use the ldapmodify command line utility.
ldapmodify can be run either in interactive mode or with inputs specified in a file. For most examples in this guide, the file contents to be used with the ldapmodify command are supplied. The general form of the command to use with these files is:
ldapmodify -D <adminDN> --w <password> --i <filename>
To update the server configuration settings dynamically, you need to issue the following ldapexop commands. This command updates all configuration settings that are dynamic:
ldapexop -D cn=root -w root -op readconfig -scope entire
This command updates a single setting.
ldapexop -D cn=root -w root -op readconfig -scope single <entry DN>
<attribute>
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically. See Command line utilities for more information about the ldapmodify and ldapexop commands.
This panel also has two modifiable required fields, Unsecure port (default value is 389) and Secure port (default value 636) that display the respective current port numbers. If you want to change the port settings, enter a number ranging from 1 through 65535.
You must restart the server for changes to take effect.
Notes:
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Performance tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Directory,cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration changetype: modify replace: ibm-slapdDbConnections ibm-slapdDbConnections: 15 dn: cn=Front End, cn=Configuration changetype: modify replace: ibm-slapdACLCache ibm-slapdACLCache: TRUE - replace: ibm-slapdACLCacheSize ibm-slapdACLCacheSize: 25000 - replace: ibm-slapdEntryCacheSize ibm-slapdEntryCacheSize: 25000 - replace: ibm-slapdFilterCacheSize ibm-slapdFilterCacheSize: 25000 - replace: ibm-slapdFilterCacheBypassLimit ibm-slapdFilterCacheBypassLimit: 100
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope entire
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically.
You can set search parameters to control users' search capabilities, such as paged and sorted searching.
Paged results allow you to manage the amount of data returned from a search request. You can request a subset of entries (a page) instead of receiving all the results at once. Subsequent search requests display the next page of results until the operation is canceled or the last result is returned. Sorted search allows a client to receive search results sorted by a list of criteria, where each criteria represents a sort key. This moves the responsibility of sorting from the client application to the server, where it might be done more efficiently.
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Search settings tab.
See Extended controls for search for additional information about searches.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Configuration changetype: modify replace: ibm-slapdTimeLimit ibm-slapdTimeLimit: 900 - replace: ibm-slapdSizeLimit ibm-slapdSizeLimit: 500 dn: cn=Directory,cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration changetype: modify replace: ibm-slapdPagedResAllowNonAdmin ibm-slapdPagedResAllowNonAdmin: TRUE - replace: ibm-slapdPagedResLmt ibm-slapdPagedResLmt: 3 - replace: ibm-slapdPageSizeLmt ibm-slapdPageSizeLmt: 201 - replace: ibm-slapdSortKeyLimit ibm-slapdSortKeyLimit: 3 - replace: ibm-slapdSortSrchAllowNonAdmin: TRUE dn: cn=Front End, cn=Configuration changetype: modify replace: ibm-slapdIdleTimeOut ibm-slapdIdleTimeOut: 300
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope entire
See ldapsearch for information on how to perform searches using the command line.
The search function searches for a filter match on only the first 240 bytes of an attribute if indexing is enabled for that attribute. Additionally, if sort is specified on a search request, the server sorts the entries found by the search using only the first 240 bytes. Any end user or client application needs to take into consideration that a match for a search filter that exists in a value after the first 240 bytes might not be returned to the client depending on whether indexing is enabled for that table.
The administrator can tell if indexing has been enabled for an attribute by looking at the attribute definition in the Web Administration tool, or by looking at the attribute definition returned by a search of cn=schema. When viewing an attribute definition in the Web Administration tool, the IBM attributes fields includes one of the following index keywords: APPROX, EQUALITY, ORDERING, or SUBSTR. If the ldapsearch utility is used, the ibmattributetypes value contains the same keywords. For example, the 'cn' attribute has all indexes defined:
attributetypes=( 2.5.4.3 NAME ( 'cn' 'commonName' ) DESC 'This is the X.500
commonName attribute, which contains a name of an object.
If the object corresponds to a person, it is typically the
persons full name.' SUP 2.5.4.41 EQUALITY 2.5.13.2
ORDERING 2.5.13.3 SUBSTR 2.5.13.4 )
ibmattributetypes=( 2.5.4.3 DBNAME ( 'cn' 'cn' ) ACCESS-CLASS NORMAL LENGTH
256 EQUALITY ORDERING SUBSTR APPROX )
Sorted Search Results provides sort capabilities for LDAP clients that have limited or no sort functionality. Sorted Search Results allows an LDAP client to receive search results sorted based on a list of criteria, where each criteria represents a sort key. The sort criteria includes attribute types, matching rules, and descending order. The server uses this criteria to sort search results before returning them. This moves the responsibility of sorting from the client application to the server, where it might be done much more efficiently. For example, a client application might want to sort the list of employees at their Grand Cayman site by surname, common name, and telephone number. Instead of building the search list twice so it can be sorted (once at the server and then again at the client after all the results are returned), the search list is built only once, and then sorted, before returning the results to the client application.
The server sorts search entries based on attributes and by default allows a maximum of three sort keys (attribute names) per search operation. To change the value of this administrative limit, change the following line, ibm-slapdSortKeyLimit: 3, in the ibmslapd.conf file. See Setting Searches for information on how to do this. If the line does not exist, add it to set the new maximum (if the line does not exist, the server is using the default value). Additionally, because sorting search results before returning them uses more server resources than simply returning them, by default only requests from users binding with Administrator authority are honored by the server. If you would like the server to honor requests from all others, including those binding anonymously, you can configure the server to do so. To honor sorted search requests submitted using non-Administrator bind, change the following line, ibm-slapdSortSrchAllowNonAdmin: FALSE, in the ibmslapd.conf file. See Setting Searches. If the line does not exist, add it with a value of TRUE to allow non-Administrator bind. SeeAdding search attributes example .
The LDAP server returns all referrals to the client at the end of a search request, the same as is done today. It is up to the application using the client services to decide whether to set the criticality of the sorted search request, and to handle a lack of support of those controls on referral servers as appropriate based on the application. Additionally, the LDAP server does not ensure that the referral server supports the sorted search control. Multiple lists could be returned to the client application, some not sorted. It is the client application's decision as to how to best present this information to the end user. Possible solutions include: combine all referral results before presenting to the end user; show multiple lists and the corresponding referral server host name; take no extra steps and show all results to the end user as they are returned from the server. The client application must turn off referrals to get one truly sorted list, otherwise when chasing referrals with sorted search controls specified, unpredictable results might occur.
It is important to note when taking advantage of the server sorted search results that:
More information about the server side sorted search control can be found in RFC 2891. The control OID for sorted search results is 1.2.840.113556.1.4.473, and is included in the RootDSE information as a supported control.
Simple Paged Results provides paging capabilities for LDAP clients that want to receive just a subset of search results (page) instead of the entire list. The next page of entries is returned to the client application for each subsequent paged results search request submitted by the client until the operation is canceled or the last result is returned. The server ignores a simple paged results request if the page size is greater than or equal to the sizeLimit value for the server because the request can be satisfied in a single operation.
Because paging of search results holds server resources throughout the life of the simple paged results request, there are several new administrative limits employed to ensure that server resources cannot be abused, or misused, through the use of simple paged results search requests.
The LDAP server returns all referrals to the client at the end of a search request, the same as a search without any controls. That means that if the server has 10 pages of results returned, all the referrals are returned on the 10th page, not at the end of each page. When chasing referrals, the client application needs to send in an initial paged results request, with the cookie set to null, to each of the referral servers. It is up to the application using the client services to decide whether or not to set the criticality as to the support of paged results, and to handle a lack of support of this control on referral servers as appropriate based on the application. Additionally, the LDAP server does not ensure that the referral server supports paged results controls. Multiple lists could be returned to the client application, some not paged. It is at the client application's decision as to how to best present this information to the end user. Possible solutions include: combine all referral results before presenting to the end user; show multiple lists and the corresponding referral server host name; take no extra steps and show all results to the end user as they are returned from the server. The client application must turn off referrals to get one truly paged list, otherwise when chasing referrals with the paged results search control specified, unpredictable results may occur.
More information about the server side simple paged results control can be found in RFC 2686. The control OID for simple paged results is 1.2.840.113556.1.4.319, and is included in the RootDSE information as a supported control.
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Directory,cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration changetype: add add: ibm-slapdSortSrchAllowNonAdmin ibm-slapdSortSrchAllowNonAdmin: TRUE - add: ibm-slapdSortKeyLimit ibm-slapdSortKeyLimit: 3 - add: ibm-slapdPagedResAllowNonAdmin ibm-slapdPagedResAllowNonAdmin: TRUE - add: ibm-slapdPagedResLmt ibm-slapdPagedResLmt: 3 - add: ibm-slapdPagedSizeLmt ibm-slapdPagedSizeLmt: 50 - add: ibm-slapdIdleTimeOut ibm-slapdIdleTimeOut: 300
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope entire
Transaction processing enables an application to group a set of entry updates together in one operation. Normally each individual LDAP operation is treated as a separate transaction with the database. Grouping operations together is useful when one operation is dependent on another operation because if one of the operations fails, the entire transaction fails. Transaction settings determine the limits on the transaction activity allowed on the server.
To enable transaction support:
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Transactions tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Transaction,cn=Configuration changetype: modify replace: ibm-slapdTransactionEnable ibm-slapdTransactionEnable: TRUE - replace: ibm-slapdMaxNumOfTransactions ibm-slapdMaxNumOfTransactions: 20 - replace: ibm-slapdMaxOpPerTransaction ibm-slapdMaxOpPerTransaction: 5 - replace: ibm-slapdMaxTimeLimitOfTransactions ibm-slapdMaxTimeLimitOfTransactions: 300
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope entire
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically.
To disable transaction processing:
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Transaction,cn=Configuration changetype: modify replace: ibm-slapdTransactionEnable ibm-slapdTransactionEnable: False
You must restart the server for the changes to take effect.
See the IBM Directory Server Version 5.1 C-Client SDK Programming Reference for more information about transaction support.
The event notification function allows a server to notify a registered client that an entry in the directory tree has been changed, added or deleted. This notification is in the form of an unsolicited message.
When an event occurs, the server sends a message to the client as an LDAP v3 unsolicited notification. The messageID is 0 and the message is in the form of an extended operation response. The responseName field is set to the registration OID. The response field contains the unique registration ID and a timestamp for when the event occurred. The time field is in UTC time format.
To enable event notification:
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Event notification tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Event Notification,cn=Configuration changetype: modify replace: ibm-slapdEnableEventNotification ibm-slapdEnableEventNotification: TRUE - replace: ibm-slapdMaxEventsPerConnection ibm-slapdMaxEventsPerConnection: 100 - replace: ibm-slapdMaxEventsTotal ibm-slapdMaxEventsTotal: 0
If you have enabled event notification, you must restart the server for the changes to take effect. If you were modifying only the settings, the server does not need to be restarted.
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope entire
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically.
To disable event notification:
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=Event Notification,cn=Configuration changetype: modify replace: ibm-slapdEnableEventNotification ibm-slapdEnableEventNotification: FALSE
You must restart the server for the changes to take effect.
See the IBM Directory Server Version 5.1 C-Client SDK Programming Reference for more information about event notification.
A suffix is a DN that identifies the top entry in a locally held directory hierarchy. Because of the relative naming scheme used in LDAP, this DN is also the suffix of every other entry within that directory hierarchy. A directory server can have multiple suffixes, each identifying a locally held directory hierarchy, for example, o=ibm,c=us.
Entries to be added to the directory must have a suffix that matches the DN value, such as 'ou=Marketing,o=ibm,c=us'. If a query contains a suffix that does not match any suffix configured for the local database, the query is referred to the LDAP server that is identified by the default referral. If no LDAP default referral is specified, an Object does not exist result is returned.
To create or add a suffix use one of the following methods.
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Suffixes tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
DN: cn=Directory, cn=RDBM Backends, cn=IBM Directory, cn=Schemas, cn=Configuration changetype: modify add: ibm-slapdSuffix ibm-slapdSuffix: <suffixname> ibm-slapdSuffix: <suffix2> ibm-slapdSuffix: <suffix3>
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope single "cn=Directory,
cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration" ibm-slapdSuffix
To remove a suffix use one of the following methods:
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Suffixes tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
DN: cn=Directory, cn=RDBM Backends, cn=IBM Directory, cn=Schemas, cn=Configuration changetype: modify delete: ibm-slapdSuffix ibm-slapdSuffix: <suffixname> ibm-slapdSuffix: <suffix2> ibm-slapdSuffix: <suffix3>
You must restart the server for the change to take effect.
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope single "cn=Directory,
cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration" ibm-slapdSuffix
Referrals provide a way for servers to refer clients to additional directory servers. A referral specifies the URL of an alternate LDAP server. This alternate server handles any requests for objects that are not found within any of the subtrees of the current LDAP server. With referrals you can:
Some of the advantages of using referrals are the ability to:
set LDAP_LOCK_REC=anyvalue
Using the Web Administration utility is the recommended method to create and remove referrals.
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Referrals tab.
You must restart the server for the changes to take effect.
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Referrals tab.
You must restart the server for the changes to take effect.
This section describes how to use the referral object class and the ref attribute to construct entries in an LDAP directory containing references to other LDAP directories. This section also describes how to associate multiple servers using referrals and an example of this.
The referral object class and the ref attribute are used to facilitate distributed name resolution or to search across multiple servers. The ref attribute appears in an entry named in the referencing server. The value of the ref attribute points to an entry maintained in the referenced server.
Following is an example configuration that illustrates the use of the ref attribute.
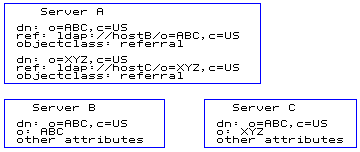
Figure 1. Example of using the referral attribute

In the example, Server A holds references to two entries: o=ABC, c=US and o=XYZ, c=US. For the o=ABC, c=US entry, Server A holds a reference to Server B and for the o=XYZ, c=US entry, Server A holds a reference to Server C.
The recommended setup of referrals is to structure the servers into a hierarchy based on the subtrees they manage. Then, provide "forward" referrals from servers that hold higher (closer to the root of the hierarchy) information and set the default referral to point back to its parent server.
To associate servers through referrals:
Use referral objects to point to the other servers for subordinate references, that is, portions of the namespace below this server that it does not service directly.
Referral objects, like other objects, go in the backend (DB2). Referral objects consist of:
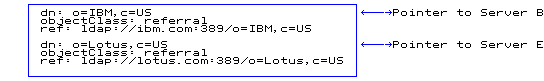
dn: o=IBM,c=US objectclass: referral ref: ldap://9.130.25.51:389/o=IBM,c=US
Define a default referral to reference a directory on another server. The default referral can be used to point to:
# referral dn: cn=Referral, cn=Configuration objectclass: top objectclass: ibm-slapdReferral cn: Referral ibm-slapdReferral: ldap://dcecds3.endicott.ibm.com:389 ibm-slapdReferral: ldap://<additional hostname:port> ibm-slapdReferral: ldap://<additional hostname:port> ibm-slapdReferral: ldap://<additional hostname:port>
To delete a single default referral, for example, austin.ibm.com:389, issue the command:
ldapmodify -D <adminDN> -w <adminPW> -f <filename>
where <filename> contains:
dn: cn=referral, cn= configuration changetype: modify delete: ibm-slapdReferral ibm-slapdReferral: ldap://referral.austin.ibm.com:398
To delete all default referrals:
ldapdelete -D <adminDN> -w <adminPW> "cn=referral,cn=configuration"
When performing searches, the same DN that was used to bind or log in to the original server is used to bind to the referred-to server, unless the IBM Directory application is designed to modify the bind DN and credentials. The correct access must be set up for the same DN to be able to bind to both servers for chasing the referrals. See Logging on to the Web Administration Tool for additional information.
Following are the steps involved in distributing the namespace using referrals.
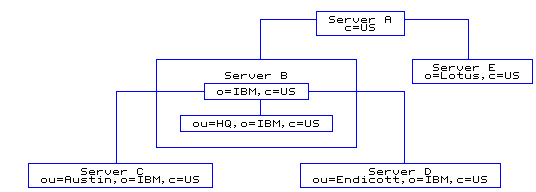
country - US company - IBM, Lotus organizationalUnit - IBM Austin, IBM Endicott, IBM Raleigh, IBM HQ
Figure 2. Setting up the servers
Server descriptions:
Figure 3. Server A database (LDIF input)
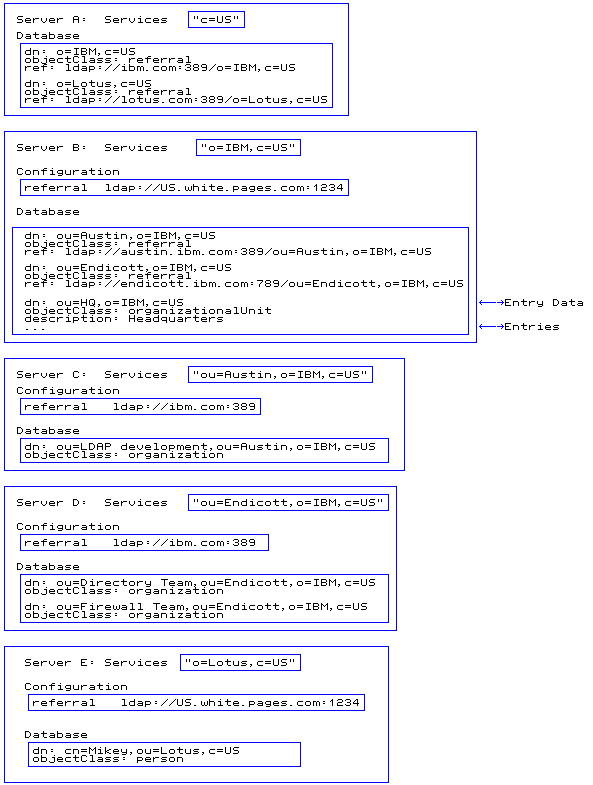
Servers can also define a default referral, which is used to point to a "more knowledgeable" server for anything that is not underneath them in the namespace.
Following is an arrangement of the same five servers, showing the referral objects in the database as well as the default referrals that are used for superior references.
Figure 4. Referral example summary
This section describes the steps necessary for keeping the data in your directory secure.
The IBM Directory Server has the ability to protect LDAP access by encrypting data with Secure Sockets Layer (SSL) security. When using SSL to secure LDAP communications with the IBM Directory, both server authentication and client authentication are supported. To use SSL you must have GSKit installed on your system. See Secure Sockets Layer and Using gsk6ikm for more information.
Expand the Manage security properties category in the navigation area of the Web Administration Tool, select the SSL settings tab.
For server authentication the IBM Directory Server supplies the client with the IBM Directory Server's X.509 certificate during the initial SSL handshake. If the client validates the server's certificate, then a secure, encrypted communication channel is established between the IBM Directory Server and the client application.
For server authentication to work, the IBM Directory Server must have a private key and associated server certificate in the server's key database file.
PS -ef | grep ibmdiradm kill -p <pid obtained by previous command>
ibmdiradm
To use the command line to configure SSL communications, issue the command:
ldapmodify -D <AdminDN> -w <Adminpassword> -i <filename>
where <filename> contains:
dn: cn=SSL,cn=Configuration changetype: modify replace: ibm-slapdSslAuth ibm-slapdSslAuth: serverAuth | serverClientAuth - replace: ibm-slapdSecurity ibm-slapdSecurity: none | SSL | SSlOnly
You must restart the server and the administration daemon for the changes to take effect.
If you have selected to use server and client authentication in your SSL settings, you might want to configure your server to check for revoked or expired certificates.
When a client sends an authenticated request to a server, the server reads the certificate and sends a query to an LDAP server with a list that contains revoked certificates. If the client certificate is not found in the list, communications between the client and server are allowed over SSL. If the certificate is found, communications are not allowed.
To configure SSL certificate revocation verification, expand the Manage security properties category in the navigation area of the Web Administration Tool, select the Certificate revocation tab.
To use the command line to configure for SSL certificate revocation verification, issue the command:
ldapmodify -D <AdminDN> -w <Adminpassword> -i <filename>
where <filename> contains:
dn: cn=CRL,cn=SSL,cn=Configuration changetype: modify replace: ibm-slapdCrlHost ibm-slapdCrlHost: <newhostname> - replace: ibm-slapdCrlPassword ibm-slapdCrlPassword: <password> - replace: ibm-slapdCrlPort ibm-slapdCrlPort: <portnumber> - replace: ibm-slapdCrlUser ibm-slapdCrlUser: <username>
You must restart the server and the administration daemon for the changes to take effect.
Expand the Manage security properties category in the navigation area of the Web Administration Tool, select the SSL key database tab.
To use the command line to set the SSL key database, issue the command:
ldapmodify -D <AdminDN> -w <Adminpassword> -i <filename>
where <filename> contains:
dn: cn=SSL,cn=Configuration changetype: modify replace: ibm-slapdSSLKeyDatabase ibm-slapdSSLKeyDatabase: <databasename> - replace: ibm-slapdSSLKeyDatabasePW ibm-slapdSSLKeyDatabasePW: <password> - replace: ibm-slapdSslKeyRingFile ibm-slapdSslKeyRingFile: <filename> - replace: ibm-slapdSslKeyRingFilePW ibm-slapdSslKeyRingFilePW: <password>
You must restart the server and the administration daemon for the changes to take effect.
By default the SSL version of IBM Directory Server uses the following list of ciphers when performing cipher negotiation with the client (during the SSL handshake).
From the navigation area in the Web Administration tool, select SSL encryption.
| Encryption level | Attribute |
|---|---|
| Triple DES encryption with a 168-bit key and a SHA-1 MAC | ibm-slapdSslCipherSpec: TripleDES-168 |
| DES encryption with a 56-bit key and a SHA-1 MAC | ibm-slapdSslCipherSpec: DES-56 |
| RC4 encryption with a 128-bit key and a SHA-1 MAC | ibm-slapdSslCipherSpec: RC4-128-SHA |
| RC4 encryption with a 128-bit key and a MD5 MAC | ibm-slapdSslCipherSpec: RC4-128-MD5 |
| RC2 encryption with a 40-bit key and a MD5 MAC | ibm-slapdSslCipherSpec: RC2-40-MD5 |
| RC4 encryption with a 40-bit key and a MD5 MAC | ibm-slapdSslCipherSpec: RC4-40-MD5 |
| AES encryption | ibm-slapdSslCipherSpec: AES |
The selected ciphers are stored in the configuration file using the ibm-slapdsslCipherSpec keyword and the attribute defined from the preceding table. For example, to use only Triple DES, select Triple DES encryption with a 168-bit key and an SHA-1 MAC. The attribute ibm-slapdSslCipherSpec: TripleDES-168 is added to the ibmslapd.conf file. In this case, only clients that also support Triple DES are able to establish an SSL connection with the server.
To use the command line to set the SSL level of encryption, in this example to AES, issue the command:
ldapmodify -D <AdminDN> -w <Adminpassword> -i <filename>
where <filename> contains:
dn: cn=SSL,cn=Configuration changetype: modify replace: ibm-slapdSslCipherSpec ibm-slapdSslCipherSpec: AES
See Table 4 for other encryption values. You must restart the server and the administration daemon for the changes to take effect.
The IBM Directory Server has the ability to protect LDAP access by encrypting data with Secure Sockets Layer (SSL) security. When using SSL to secure LDAP communications with the IBM Directory, both server authentication and client authentication are supported.
With server authentication, the IBM Directory Server must have a digital certificate (based on the X.509 standard). This digital certificate is used to authenticate the IBM Directory Server to the client application (such as the Directory Management Tool or ldapsearch) or an application built from the application development package, for LDAP access over SSL.
For server authentication the IBM Directory Server supplies the client with the IBM Directory Server's X.509 certificate during the initial SSL handshake. If the client validates the server's certificate, then a secure, encrypted communication channel is established between the IBM Directory Server and the client application.
For server authentication to work, the IBM Directory Server must have a private key and associated server certificate in the server's key database file.
Client authentication provides for two-way authentication between the LDAP client and the LDAP server.
With client authentication, the LDAP client must have a digital certificate (based on the X.509 standard). This digital certificate is used to authenticate the LDAP client to the IBM Directory Server. See Client authentication.
To conduct commercial business on the Internet, you might use a widely known Certification Authority (CA), such as VeriSign, to get a high assurance server certificate.
The following high-level steps are required to enable SSL support for IBM Directory for server authentication. These steps assume you have already installed and configured the IBM Directory Server:
If you also want to have secure communications between a master IBM Directory Server and one or more replica servers, you must complete the following additional steps:
For server authentication, you can modify the ibmslapd.conf file under the cn=SSL, cn=Configuration entry. To use the Web Administration Tool, see Configuring SSL settings.
To use the command line:
ldapmodify -D <AdminDN> -w <Adminpassword> -i <filename>
where <filename> contains:
dn: cn=SSL,cn=Configuration changetype: modify replace: ibm-slapdSSLAuth ibm-slapdSSLAuth: serverAuth
You must restart the server and the administration daemon for the changes to take effect.
In order to provide a secure connection between IBM Directory and its clients, the server must have an X.509 certificate and a private key.
The steps required to generate a private key, obtain the required server certificate from an external CA, and prepare them for use by the IBM Directory are outlined in the following:
chown ldap:ldap <mykeyring>.*
See Kerberos service name change for a more detailed explanation.
When you receive the resulting certificate from the CA:
If you are using the IBM Directory in an intranet environment, use gsk6ikm to create your own server certificates. You can also use gsk6ikm to test IBM Directory with SSL without purchasing a VeriSign high-assurance server certificate. These types of certificates are known as self-signed certificates.
Follow these steps to create a key database file using self-signed certificates.
See Using gsk6ikm for additional information.
Notes:
The following steps are required to create a key database file for an LDAP client that contains one or more self-signed server certificates that are marked as trusted by the client. The process can also be used to import CA certificates from other sources, such as VeriSign, into the client's key database file for use as trusted roots. A trusted root is simply an X.509 certificate signed by a trusted entity (for example VeriSign, or the creator of a self-signed server certificate), imported into the client's key database file, and marked as trusted.
See Using gsk6ikm for additional information.
When the LDAP client creates a secure SSL connection with the server, it uses the server's self-signed certificate to verify that it is connecting to the proper server.
Repeat the preceding steps for each IBM Directory Server that the LDAP client needs to connect to in a secure fashion.
To migrate the old key ring file which was created from MKKF utility, do the following steps:
Client authentication provides for two-way authentication between the LDAP client and the LDAP server.
With client authentication, the LDAP client must have a digital certificate (based on the X.509 standard). This digital certificate is used to authenticate the LDAP client to the IBM Directory Server.
The Simple Authentication and Security Layer (SASL) can be used to add authentication support to connection protocols. A protocol includes a command for identifying and authenticating a user to a server. It can optionally negotiate a security layer for subsequent protocol interactions.
After a server receives the authentication command or any client response, it may issue a challenge or indicate failure or completion. If a client receives a challenge it may issue a response or abort the exchange, depending on the profile of the protocol.
During the authentication protocol exchange, the SASL mechanism performs authentication, transmits an authorization identity (known as userid) from the client to the server, and negotiates the use of a mechanism-specific security layer.
When the LDAP server receives an LDAP bind request from a client, it processes the request in the following order:
For client authentication, you can modify the ibmslapd.conf file under the cn=SSL, cn=Configuration entry. To use the Web Administration Tool, see Configuring SSL settings.
To use the command line:
ldapmodify -D <AdminDN> -w <Adminpassword> -i <filename>
where <filename> contains:
dn: cn=SSL,cn=Configuration cn: SSL changetype: modify replace: ibm-slapdSSLAuth ibm-slapdSSLAuth: serverClientAuth
You must restart the server and the administration daemon for the changes to take effect.
The following key-management program is provided with IBM's Global Security Kit (GSKit):
export LIBPATH=/usr/ldap/java/bin:/usr/ldap/java/bin/classic:$LIBPATH
Use gsk6ikm to create public-private key pairs and certificate requests, receive certificate requests into a key database file, and manage keys in a key database file.
The tasks you can perform with gsk6ikm include:
If your client application is connecting to an LDAP server that requires client and server authentication, then you need to create a public-private key pair and a certificate.
If your client application is connecting to an LDAP server that only requires server authentication, it is not necessary to create a public-private key pair and a certificate. It is sufficient to have a certificate in your client key database file that is marked as a trusted root. If the Certification Authority (CA) that issued the server's certificate is not already defined in your client key database, you need to request the CA's certificate from the CA, receive it into your key database, and mark it as trusted. See Designating a key as a trusted root.
Your client uses its private key to sign messages sent to servers. The server sends its public key to clients so that they can encrypt messages to the server, which the server decrypts with its private key.
To send its public key to a server, the client needs a certificate. The certificate contains the client's public key, the Distinguished Name associated with the client's certificate, the serial number of the certificate, and the expiration date of the certificate. A certificate is issued by a CA, which verifies the identity of the client.
The basic steps to create a certificate that is signed by a CA are:
To create a public-private key pair and request a certificate:
gsk6ikm
If this is a request for a VeriSign low assurance certificate or secure server certificate, you must E-mail the certificate request to VeriSign.
You can mail the low assurance certificate request to VeriSign immediately. A secure server certificate request requires more documentation. To find out what VeriSign requires for a secure server certificate request, go to the following URL: http://www.verisign.com/ibm.
After receiving a response from your CA, you need to receive the certificate into a key database.
To receive a certificate into a key database:
To change a key database password:
To show information about a key, such as its name, size or whether it is a trusted root:
To delete a key:
The default key must be the private key the server uses for its secure communications.
To make a key the default key in the key ring:
By definition, a secure server must have a public-private key pair and a certificate.
The server uses its private key to sign messages to clients. The server sends its public key to clients so they can encrypt messages to the server, which the server decrypts with its private key.
The server needs a certificate to send its public key to clients. The certificate contains the server's public key, the Distinguished Name associated with the server's certificate, the serial number of the certificate, and the expiration date of the certificate. A certificate is issued by a CA, who verifies the identity of the server.
You can request one of the following certificates:
For information about using a CA such as VeriSign to sign the server certificate, see Creating a key pair and requesting a certificate from a Certificate Authority.
The basic steps to creating a self-signed certificate are:
If you need to transfer a key pair or certificate to another computer, you can export the key pair from its key database to a file. On the other computer, you can import the key pair into a key ring.
To export a key from a key database:
To import a key into a key ring:
A trusted root key is the public key and associated Distinguished Name of a CA. The following trusted roots are automatically defined in each new key database:
To designate a key as a trusted root:
A trusted root key is the public key and associated Distinguished Name of a CA. The following trusted roots are automatically defined in each new key database:
To remove the trusted root status of a key:
To create a certificate request for an existing key:
Send the certificate request to the CA.
If this is a request for a VeriSign low assurance certificate or secure server certificate, you must E-mail the certificate request to VeriSign.
You can mail the low assurance certificate request to VeriSign immediately. A secure server certificate request requires more documentation. To find out what VeriSign requires for a secure server certificate request, go to the following URL: http://www.verisign.com/ibm.
The gsk6ikm program can be used to migrate an existing keyring file, as created with mkkf, to the format used by gsk6ikm.
To migrate a keyring file:
Password policy is a set of rules that controls how passwords are used and administered in the IBM Directory. These rules are made to ensure that users change their passwords periodically, and that the passwords meet the organization's syntactic password requirements. These rules also can restrict the reuse of old passwords and ensure that users are locked out after a defined number of failed attempts.
All users except the directory administrator are forced to comply with this password policy. The password for the administrator never expires and the account is never locked. The directory administrator has sufficient access control privileges to modify users' passwords and the password policy.
Expand the Manage security properties category in the navigation area of the Web Administration Tool, select the Password policy tab.
See Password encryption for additional information.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=pwdpolicy changetype: modify replace: ibm-pwdpolicy ibm-pwdpolicy: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace:pwdallowuserchange pwdallowuserchange: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace:pwdmustchange pwdmustchange: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace:pwdmaxage pwdmaxage: 5 - replace:pwdexpirewarning pwdexpirewarning: 7 - replace:pwdgraceloginlimit pwdgraceloginlimit: 2
You must restart the server for the changes to take effect.
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Password lockout tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=pwdpolicy changetype: modify replace: pwdlockout pwdlockout: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace:pwdmaxfailure pwdmaxfailure: 3 - replace:pwdlockoutduration pwdlockoutduration: 15 - replace:pwdfailurecountinterval pwdfailurecountinterval: 30 - replace:pwdexpirewarning pwdexpirewarning: 7 - replace:pwdgraceloginlimit pwdgraceloginlimit: 2
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Password validation tab.
To perform the same operations using the command line, issue the following command:
ldapmodify -D <AdminDN> -w<Adminpassword> -i<filename>
where <filename> contains:
dn: cn=pwdpolicy changetype: modify replace: pwdinhistory pwdinhistory: 8 - replace:pwdchecksyntax pwdchecksyntax: 0|1|2 # 0=No syntax check #1=Check syntax (except encrypted) #2=Check syntax on all- replace:pwdminlength pwdminlength: 6 - replace:passwordminalphachars passwordminalphachars: 3 - replace:passwordminotherchars passwordminotherchars: 3 - replace:passwordmaxrepeatedchars passwordmaxrepeatedchars: 2 - replace:passwordmindiffchars passwordmindiffchars: 4
IBM Directory allows you to prevent unauthorized access to user passwords. User passwords may be encoded and stored in the directory, which prevents clear passwords from being accessed by any users including the system administrators.
The administrator may configure the server to encode userPassword attribute values in either a one-way encoding format or a two-way encoding format.
After the server is configured, any new passwords (for new users) or modified passwords (for existing users) are encoded before they are stored in the directory database. The encoded passwords are tagged with the encoding algorithm name so that passwords encoded in different formats can coexist in the directory. When the encoding configuration is changed, existing encoded passwords remain unchanged and continue to work.
For applications which require retrieval of clear passwords, such as middle-tier authentication agents, the directory administrator needs to configure the server to perform either a two-way encoding or no encryption on user passwords. In this instance, the clear passwords stored in the directory are protected by the directory ACL mechanism.
Two-way encoding format:
imask, a 2-way masking option, is provided to allow values of the userPassword attribute to be encoded in the directory and retrieved as part of an entry in the original clear format. Some applications such as middle-tier authentication servers require passwords to be retrieved in clear, however, corporate security policies might prohibit storing clear passwords in a secondary permanent storage. This option satisfies both requirements.
A simple bind will succeed if the password provided in the bind request matches with any of the multiple values of the userPassword attribute.
When you configure the server using Web Administration, you can select one of the following four encryption options:
The default option is imask. The change is registered in a password encryption directive of the server configuration file:
ibm-SlapdPwEncryption: imask
The server configuration file is located in:
<installation path>\etc\ibmslapd.conf
In addition to userPassword, values of the secretKey attribute are always "imask" encoded in the directory. Unlike userPassword, this encoding is enforced for values of secretKey. No other option is provided. The secretKey attribute is an IBM defined schema. Applications may use this attribute to store sensitive data that need to be always encoded in the directory and retrieve the data in clear via the directory access control.
Consult the Installation and Configuration Guide for additional information about the configuration file.
To change the type of encryption using the command line, for example to crypt, issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -f <filename>
where <filename>contains:
dn: cn=configuration changetype: modify replace: ibm-slapdPWEncryption ibm-slapdPWEncryption: crypt
To update the settings dynamically, issue the following ldapexop command:
ldapexop -D <adminDN> -w <adminPW> -op readconfig -scope single
"cn=configuration" ibm-slapdPWEncryption
Notes:
The IBM Directory supports Kerberos Version 1.3 servers, such as the IBM Network Authentication Service, on AIX servers and clients, and Windows NT(R) and Windows 2000 clients only.
Under Network Authentication Service, a client (generally either a user or a service) sends a request for a ticket to the Key Distribution Center (KDC). The KDC creates a ticket-granting ticket (TGT) for the client, encrypts it using the client's password as the key, and sends the encrypted TGT back to the client. The client then attempts to decrypt the TGT, using its password. If the decryption is successful, the client retains the decrypted TGT, indicating proof of the client's identity.
The TGT, which expires at a specified time, permits the client to obtain additional tickets that give permission for specific services. The requesting and granting of these additional tickets does not require user intervention.
Network Authentication Service negotiates authenticated, optionally encrypted communications between two points on the network. It can enable applications to provide a layer of security that is not dependent on which side of a firewall either client is on. Because of this, Network Authentication Service can play a vital role in the security of your network.
You need to create an LDAP server servicename in the key distribution center (KDC) using the principal name ldap/<hostname>.<mylocation>.<mycompany>.com.
Network Authentication Service provides the following components:
Expand the Manage server properties category in the navigation area of the Web Administration Tool, select the Kerberos tab.
To create a Kerberos entry issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -f <filename>
where <filename>contains:
dn: cn=Kerberos, cn=Configuration cn: Kerberos ibm-slapdKrbAdminDN: ibm-kn=admin@MYREALM.AUSTIN.IBM.COM ibm-slapdKrbEnable: true ibm-slapdKrbIdentityMap: true ibm-slapdKrbKeyTab: /keytabs/mykeytab.keytab ibm-slapdKrbRealm: MYREALM.AUSTIN.IBM.COM objectclass: ibm-slapdKerberos objectclass: ibm-slapdconfigEntry objectclass: top
To modify a Kerberos entry, for example to change the keytab file, issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -f <filename>
where <filename> contains:
dn: cn=Kerberos, cn=Configuration changetype: modify replace: ibm-slapdKrbKeyTab ibm-slapdKrbKeyTab: /keytabs/mynewkeytab.keytab
Before you can us the command line for Kerberos authentication, you need to do a Kerberos initialization. Issue the following command:
kinit <kerberos_principlename>@<realm_name>
To use Kerberos authentication you must specify the -m option with the GSSAPI parameter on the ldapadd and ldapsearch commands. For example:
ldapsearch -V 3 -m GSSAPI -b <"cn=us"> objectclass=*
Identity mapping enables the directory administrator to use the existing set of ACL data with the Kerberos authentication method. The ACL for the IBM Directory is based on the Distinguished Name (DN) assigned to the client connected to the directory server. The access rights are based on what permissions have been granted for that DN and the permissions for any groups containing that DN as a member. If the bind method for GSSAPI is used (that is, Kerberos is used for authenticating to the server), the DN is something like IBM-KN=your_principal@YOUR_REALM_NAME. This type of DN can be used as members of access groups or access IDs. You can also use the Kerberos Identity Mapping feature to grant access rights for this DN to an entry already in the directory.
For example, if there is an entry in the directory for Reginald Bender:
dn: cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US objectclass: top objectclass: person objectclass: organizationalperson cn: Reginald Bender sn: Bender aclentry: access-id:CN=THIS:critical:rwsc aclentry: group:CN=ANYBODY:normal:rsc userpassword: cL1eNt
The access rights for this entry allow anyone binding with the DN "cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US" to view critical data such as the password, but no one else.
If Reginald Bender used Kerberos to bind to the server, his DN could be something like IBM-KN=rbender@SW.REALM_1. If identity mapping is not enabled on the server, he is not allowed to view his own entry's password.
If identity mapping is enabled, he can view the password if this entry were changed to include:
dn: cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US... objectclass: ibm-securityidentities altsecurityidentities: Kerberos:rbender@SW.REALM_1
When Reginald Bender binds to the directory server, the server first searches the whole directory to determine if the directory is a KDC (Key Distribution Center) account registry. If it is not, the server searches the directory for any entry containing an altsecurityidentities attribute with a value matching the Kerberos user principal and realm. In this example, rbender is the user principal and SW.REALM_1 is the realm. This is the default for the Kerberos identity mapping. The bind fails if more than one entry has an attribute with this value. The mapping must be one-to-one. If the mapping is successful, Reginald Bender has all of the access rights for "cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US", including any access groups that has this as a member.
The IBM Directory Server can be used to contain Kerberos account information (krbRealmName-V2 = <realm_name> and krbPrincipalName = <princ_name>@<realm_name>) to serve as the backing store for a KDC.
The server with Kerberos identity mapping enabled first searches the directory for entries with objectclass krbRealm-V2 and krbRealmName-V2 =<realm_name>, such as:
dn: krbRealmName-V2=SW.REALM_1, o=SecureWay.com, c=US objectclass: krbRealm-V2 krbReamlName-V2: SW.REALM_1
If no entries are found, the server uses the default Kerberos identity mapping described previously. If more than one entry is found, the bind fails.
However, if the directory contains the single entry:
dn: krbRealmName-V2=SW.REALM_1, ou=Group, o=SecureWay.com, c=US objectclass: krbRealm-V2 krbRealmName-V2: SW.REALM_1 krbPrincSubtree: ou=internal users,o=SecureWay.com, c=US krbPrincSubtree: ou=external users,o=SecureWay.com, c=US
The server searches each subtree listed as a value of krbPrincSubtree for an entry with an attribute krbPrincipalName.
In this release, for identity mapping to work for Reginald Bender, you need to add two attributes to the "cn=Reginal Bender, ou=internal users, o=SecureWay.com, c=US" entry:
objectclass: extensibleObject krbPrincipalName: rbender@SW.REALM_1
Depending on whether the directory is a KDC account registry, the final entry is:
dn: cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US... objectclass: ibm-securityidentities altsecurityidentities: Kerberos:rbender@SW.REALM_1...
or for a KDC account registry:
dn: cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US ... objectclass: extensibleObject krbPrincipalName: rbender@SW.REALM_1
In either case, the client is mapped to "cn=Reginald Bender, ou=internal users, o=SecureWay.com, c=US".
If a DN is not mapped because no entry is found, the mapping fails but the bind is still successful. However, if more than one DN is mapped, the bind fails.
Identity mapping enables the existing ACLs to work with Kerberos authentication. A client using Kerberos with a mapped identity has two distinct identities, both of which are evaluated in granting access.
Identity mapping has some costs. The internal searches at bind time impact performance and identity mapping requires additional setup to add the appropriate attributes to the entries to be mapped.
In this release, if default identity mapping is used, the administrator (either Kerberos or LDAP) must make sure that the data in the KDC and the data in the LDAP server are synchronized. If the data is not synchronized, incorrect results might be returned because of incorrect ACL evaluation.
A schema is a set of rules that governs the way that data can be stored in the directory. The schema defines the type of entries allowed, their attribute structure and the syntax of the attributes.
Data is stored in the directory using directory entries. A entry consists of an object class, which is required, and its attributes. Attributes can be either required or optional. The object class specifies the kind of information that the entry describes and defines the set of attributes it contains. Each attribute has one or more associated values. See Working with directory entries for additional information about entries.
The schema for the IBM Directory Version 5.1 is predefined, however, you can modify the schema, if you have additional requirements.
The IBM Directory Server Version 5.1 includes dynamic schema support. The schema is published as part of the directory information, and is available in the Subschema entry (DN="cn=schema"). You can query the schema using the ldap_search() API and modify it using ldap_modify(). See the IBM Directory Client SDK Programming Reference for more information about these APIs.
The schema has more configuration information than that included in the LDAP Version 3 Request For Comments (RFCs) or standard specifications. For example, for a given attribute, you can state which indexes must be maintained. This additional configuration information is maintained in the subschema entry as appropriate. An additional object class is defined for the subschema entry IBMsubschema , which has "MAY" attributes that hold the extended schema information.
IBM Directory Server requires that the schema defined for a naming context be stored in a special directory entry, "cn=schema". The entry contains all of the schema defined for the server. To retrieve schema information, you can perform an ldap_search by using the following:
DN: "cn=schema", search scope: base, filter: objectclass=subschema or objectclass=*
The schema provides values for the following attribute types:
The syntax of these schema definitions is based on the LDAP Version 3 RFCs.
A sample schema entry might contain:
objectclasses=( 1.3.6.1.4.1.1466.101.120.111
NAME 'extensibleObject'
SUP top AUXILIARY )
objectclasses=( 2.5.20.1
NAME 'subschema'
AUXILIARY MAY
( dITStructureRules
$ nameForms
$ ditContentRules
$ objectClasses
$ attributeTypes
$ matchingRules
$ matchingRuleUse ) )
objectclasses=( 2.5.6.1
NAME 'alias'
SUP top STRUCTURAL
MUST aliasedObjectName )
attributeTypes {
( 2.5.18.10 NAME 'subschemaSubentry' EQUALITY distinguishedNameMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.12 NO-USER-MODIFICATION
SINGLE-VALUE USAGE directoryOperation )
( 2.5.21.5 NAME 'attributeTypes'
EQUALITY objectIdentifierFirstComponentMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.3 USAGE directoryOperation )
( 2.5.21.6 NAME 'objectClasses'
EQUALITY objectIdentifierFirstComponentMatch
SYNTAX 1.3.6.1.4.1.1466.115.121.1.37 USAGE directoryOperation )
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 USAGE directoryOperation )
}
ldapSyntaxes {
( 1.3.6.1.4.1.1466.115.121.1.5 DESC 'Binary' )
( 1.3.6.1.4.1.1466.115.121.1.7 DESC 'Boolean' )
( 1.3.6.1.4.1.1466.115.121.1.12 DESC 'DN' )
( 1.3.6.1.4.1.1466.115.121.1.15 DESC 'Directory String' )
( 1.3.6.1.4.1.1466.115.121.1.24 DESC 'Generalized Time' )
( 1.3.6.1.4.1.1466.115.121.1.26 DESC 'IA5 String' )
( 1.3.6.1.4.1.1466.115.121.1.27 DESC 'INTEGER' )
( 1.3.6.1.4.1.1466.115.121.1.50 DESC 'Telephone Number' )
( 1.3.6.1.4.1.1466.115.121.1.53 DESC 'UTC Time' )
}
matchingRules {
( 2.5.13.2 NAME 'caseIgnoreMatch'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 )
( 2.5.13.0 NAME 'objectIdentifierMatch'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.38 )
( 2.5.13.30 NAME 'objectIdentifierFirstComponentMatch'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.38 )
( 2.5.13.4 NAME 'caseIgnoreSubstringsMatch'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.58 )
}
As shown in the preceding example, it is not required that all of the attribute values of a given attribute type be provided in a single production.
The schema information can be modified through the ldap_modify API. Consult the Client SDK Programming Reference for additional information. With the DN "cn=schema" you can add, delete or replace an attribute type or an object class. To delete a schema entity, provide the oid in parenthesis (oid). You also can provide a full description. You can add or replace a schema entry with the LDAP Version 3 definition or with the IBM attribute extension definition or with both definitions.
The IBM Directory supports standard directory schema as defined in the following:
This version of LDAP includes the LDAP Version 3 defined schema in the default schema configuration. It also includes the DEN schema definitions.
IBM also provides a set of extended common schema definitions that other IBM products share when they exploit the LDAP directory. They include:
An object class specifies a set of attributes used to describe an object. For example, if you created the object class tempEmployee, it could contain attributes associated with a temporary employee such as, idNumber, dateOfHire, or assignmentLength. You can add custom object classes to suit the needs of your organization. The IBM Directory Server schema provides some basic types of object classes, including:
Object classes are defined by the characteristics of type, inheritance, and attributes.
An object class can be one of three types:
This version of the IBM Directory Server supports object inheritance for object class and attribute definitions. A new object class can be defined with parent classes (multiple inheritance) and the additional or changed attributes.
Each entry is assigned to a single structural object class. All object classes inherit from the abstract object class top. They can also inherit from other object classes. The object class structure determines the list of required and allowed attributes for a particular entry. Object class inheritance depends on the sequence of object class definitions. An object class can only inherit from object classes that precede it. For example, the object class structure for a person entry might be defined in the LDIF file as:
objectClass: top objectClass: person objectClass: organizationalPerson
In this structure, the organizationalPerson inherits from the person and the top object classes, while person object class only inherits from the top object class. Therefore, when you assign the organizationalPerson object class to an entry, it automatically inherits the required and allowed attributes from the superior object class. In this case, the person object class.
Schema update operations are checked against the schema class hierarchy for consistency before being processed and committed.
Every object class includes a number of required attributes and optional attributes. Required attributes are the attributes that must be present in entries using the object class. Optional attributes are the attributes that may be present in entries using the object class.
You can view the object classes in the schema using either the Web Administration Tool, the preferred method or using the command line.
Expand Schema management in the navigation area and click Manage object classes. A read-only panel is displayed that enables you to view the object classes in the schema and their characteristics. The object classes are displayed in alphabetical order. You can move one page backwards or forward by clicking Previous or Next. The field next to these buttons identifies the page that you are on. You can also use the drop down menu of this field to skip to a specific page. The first object class listed on the page is displayed with the page number to help you locate the object class you want to view. For example, if you were looking for the object class person, you expand the drop down menu and scroll down until you see Page 14 of 16 nsLiServer and Page 15 of 16 printerLPR. Because person is alphabetically between nsLiServer and printerLPR, you select Page 14 and click Go.
You can also display the object classes sorted by type. Select Type and click Sort. The object classes are sorted alphabetically within their type, Abstract, Auxiliary, or Structural. Similarly you can reverse the list order by selecting Descending and clicking Sort.
After you have located the object class that you want, you can view its type, inheritance, required attributes, and optional attributes. Expand the drop down menus for inheritance, required attributes, and optional attributes to see the full listings for each characteristic.
You can choose the object class operations you want to perform from the right-hand tool bar, such as:
When you are finished click Close to return to the IBM Directory Server Welcome panel.
To view the object classes contained in the schema issue the command:
ldapsearch -b cn=schema -s base objectclass=* objectclasses
If you have not done so already, expand Schema management in the navigation area, then click Manage object classes. To create a new object class:
To add an object class using the command line, issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -i <filename>
where <filename>contains:
dn: cn=Schema
changetype: modify
add: objectclasses
objectclasses: ( <myobjectClass-oid> NAME '<myObjectClass>' DESC '<An object class
I defined for my LDAP application>' SUP '<objectclassinheritance>'
<objectclasstype> MAY (<attribute1> $ <attribute2>))
Not all schema changes are allowed. See Disallowed schema changes for change restrictions.
If you have not done so already, expand Schema management in the navigation area, then click Manage object classes. To edit an object class:
Select an attribute from the alphabetical list of Available attributes and click Add to required to make the attribute required or click Add to optional to make the attribute optional for the object class. The attribute is displayed in the appropriate list of selected attributes.
Repeat this process for all the attributes you want to select.
You can move an attribute from one list to another or delete the attribute from the selected lists by selecting it and clicking the appropriate Move to or Delete button.
You can view the lists of required and optional inherited attributes. Inherited attributes are based on the Superior object class selected on the General tab. You cannot change the inherited attributes. However, if you change the Superior object class on the General tab, a different set of inherited attributes is displayed.
View the object classes contained in the schema issue the command:
ldapsearch -b cn=schema -s base objectclass=* objectclasses
To edit an object class using the command line, issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -i <filename>
where <filename>contains:
dn: cn=schema
changetype: modify
replace: objectclasses
objectclasses: ( <myobjectClass-oid> NAME '<myObjectClass>' DESC '<An object class
I defined for my LDAP application>' SUP '<newsuperiorclassobject>'
<newobjectclasstype> MAY (attribute1> $ <attribute2>
$ <newattribute3>) )
If you have not done so already, expand Schema management in the navigation area, then click Manage object classes. To copy an object class:
Select an attribute from the alphabetical list of Available attributes and click Add to required to make the attribute required or click Add to optional to make the attribute optional for the object class. The attribute is displayed in the appropriate list of selected attributes.
Repeat this process for all the attributes you want to select.
You can move an attribute from one list to another or delete the attribute from the selected lists by selecting it and clicking the appropriate Move to or Delete button.
You can view the lists of required and optional inherited attributes. Inherited attributes are based on the Superior object class selected on the General tab. You cannot change the inherited attributes. However, if you change the Superior object class on the General tab, a different set of inherited attributes is displayed.
View the object classes contained in the schema issue the command:
ldapsearch -b cn=schema -s base objectclass=* objectclasses
Select the object class that you want to copy. Use an editor to change the appropriate information and save the changes to <filename>. The issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -i <filename>
where <filename>contains:
dn: cn=schema
changetype: modify
replace: objectclasses
objectclasses: ( <mynewobjectClass-oid> NAME '<mynewObjectClass>'
DESC '<A new object class
I copied for my LDAP application>'
SUP '<superiorclassobject>'<objectclasstype> MAY (attribute1>
$ <attribute2> $ <attribute3>) )
Not all schema changes are allowed. See Disallowed schema changes for change restrictions.
If you have not done so already, expand Schema management in the navigation area, then click Manage object classes. To delete an object class:
View the object classes contained in the schema issue the command:
ldapsearch -b cn=schema -s base objectclass=* objectclasses
Select the object class you want to delete and issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -i <filename>
where <filename>contains:
dn: cn=schema
changetype: modify
delete: objectclasses
objectclasses: ( <myobjectClass-oid> NAME '<myObjectClass>' DESC '<An object class
I defined for my LDAP application>' SUP '<objectclassinheritance>'
<objectclasstype> MAY (<attribute1> $ <attribute2>))
Each directory entry has a set of attributes associated with it through it's object class. While the object class describes the type of information that an entry contains, the actual data is contained in attributes. An attribute is represented by one or more name-value-pairs that hold specific data element such as a name, an address, or a telephone number. The IBM Directory Server represents data as name-value-pairs, a descriptive attribute, such as commonName (cn), and a specific piece of information, such as John Doe.
For example, the entry for John Doe might contain several attribute name-value-pairs.
dn: uid=jdoe, ou=people, ou=mycompany, c=us, objectClass: top objectClass: person objectClass: organizationalPerson cn: John Doe sn: Doe givenName: Jack givenName: John
While the standard attributes are already defined in the schema file, you can create, edit, copy, or delete attributes to suit the needs of your organization.
You can view the attributes in the schema using either the Web Administration Tool, the preferred method or using the command line.
Expand Schema management in the navigation area and click Manage attributes. A read-only panel is displayed that enables you to view the attributes in the schema and their characteristics. The attributes are displayed in alphabetical order. You can move one page backwards or forward by clicking Previous or Next. The field next to these buttons identifies the page that you are on. You can also use the drop down menu of this field to skip to a specific page. The first object class listed on the page is displayed with the page number to help you locate the object class you want to view. For example, if you were looking for the attribute authenticationUserID, you expand the drop down menu and scroll down until you see Page 3 of 62 applSystemHint and Page 4 of 62 authorityRevocatonList. Because authenticationUserID is alphabetically between applSystemHint and authorityRevocatonList, you select Page 3 and click Go.
You can also display the attributes sorted by syntax. Select Syntax and click Sort. The attributes are sorted alphabetically within their syntax. SeeAttribute syntax for a listing or the types of syntax. Similarly you can reverse the list order by selecting Descending and clicking Sort.
After you have located the attribute that you want, you can view its syntax, whether it is multi-valued, and the object classes that contain it. Expand the drop down menu for object classes to see the list of object classes for the attribute.
When you are finished click Close to return to the IBM Directory Server Welcome panel.
To view the attributes contained in the schema issue the command:
ldapsearch -b cn=schema -s base objectclass=* attributeTypes IBMAttributeTypes
Use either of the following methods to create a new attribute. The Web Administration Tool is the preferred method.
If you have not done so already, expand Schema management in the navigation area, then click Manage attributes. To create a new attribute:
The following example adds an attribute type definition for an attribute called "myAttribute", with Directory String syntax (see Attribute syntax) and Case Ignore Equality matching (see Matching rules). The IBM-specific part of the definition says that the attribute data is stored in a column named "myAttrColumn" in a table called "myAttrTable". If these names were not specified, both the column and table name would have defaulted to "myAttribute". The attribute is assigned to the "normal" access class, and values have a maximum length of 200 bytes.
ldapmodify -D <admindn> -w <adminpw> -i myschema.ldif
where the myschema.ldif file contains:
dn: cn=schema
changetype: modify
add: attributetypes
attributetypes: ( myAttribute-oid NAME ( 'myAttribute' )
DESC 'An attribute I defined for my LDAP application'
EQUALITY 2.5.13.2 SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE userApplications )
-
add: ibmattributetypes
ibmattributetypes: ( myAttribute-oid DBNAME ( 'myAttrTable' 'myAttrColumn' )
ACCESS-CLASS normal LENGTH 200 )
See ldapmodify, ldapadd for more information about this command.
Not all schema changes are allowed. See Disallowed schema changes for change restrictions.
Any part of a definition can be changed before you have added entries that use the attribute. Use either of the following methods to edit an attribute. The Web Administration Tool is the preferred method.
If you have not done so already, expand Schema management in the navigation area, then click Manage attributes. To edit an attribute:
This example adds indexing to the attribute, so that searching on it is faster. Use the ldapmodify command and the LDIF file to change the definition:
ldapmodify -D <admindn> -w <adminpw> -i myschemachange.ldif
Where the myschemachange.ldif file contains:
dn: cn=schema
changetype: modify
replace: attributetypes
attributetypes: ( myAttribute-oid NAME ( 'myAttribute' ) DESC 'An attribute
I defined for my LDAP application' EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 USAGE userApplications )
-
replace: ibmattributetypes
ibmattributetypes: ( myAttribute-oid DBNAME ( 'myAttrTable' 'myAttrColumn' )
ACCESS-CLASS normal LENGTH 200 EQUALITY SUBSTR )
Use either of the following methods to copy an attribute. The Web Administration Tool is the preferred method.
If you have not done so already, expand Schema management in the navigation area, then click Manage attributes. To copy an attribute:
View the attributes contained in the schema issue the command:
ldapsearch -b cn=schema -s base objectclass=* attributeTypes IBMAttributeTypes
Select the attribute that you want to copy. Use an editor to change the appropriate information and save the changes to <filename>. Then issue the following command:
ldapmodify -D <adminDN> -w <adminPW> -i <filename>
where <filename>contains:
dn: cn=schema
changetype: modify
add: attributetypes
attributetypes: ( <mynewAttribute-oid> NAME '<mynewAttribute>' DESC '<A new
attribute I copied for my LDAP application> EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 USAGE userApplications )
-
add: ibmattributetypes
ibmattributetypes: ( myAttribute-oid DBNAME ( 'myAttrTable' 'myAttrColumn' )
ACCESS-CLASS normal LENGTH 200 )
Not all schema changes are allowed. See Disallowed schema changes for change restrictions.
Use either of the following methods to delete an attribute. The Web Administration Tool is the preferred method.
If you have not done so already, expand Schema management in the navigation area, then click Manage attributes. To delete an attribute:
ldapmodify -D <admindn> -w <adminpw> -i myschemadelete.ldif
Where the myschemadelete.ldif file includes:
dn: cn=schema
changetype: modify
delete: attributetypes
attributetypes: ( myAttribute-oid NAME ( 'myAttribute' ) DESC 'An attribute
I defined for my LDAP application' EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15 USAGE userApplications )
-
delete: ibmattributetypes
ibmattributetypes: ( myAttribute-oid DBNAME ( 'myAttrTable' 'myAttrColumn' )
ACCESS-CLASS normal LENGTH 200 EQUALITY SUBSTR )
See ldapmodify, ldapadd for more information about this command.
The IBMAttributeTypes attribute can be used to define schema information not covered by the LDAP Version 3 standard for attributes. Values of IBMAttributeTypes must comply with the following grammar:
IBMAttributeTypesDescription = "(" whsp
numericoid whsp
[ "DBNAME" qdescrs ] ; at most 2 names (table, column)
[ "ACCESS-CLASS" whsp IBMAccessClass whsp ]
[ "LENGTH" wlen whsp ] ; maximum length of attribute
[ "EQUALITY" [ IBMwlen ] whsp ] ; create index for matching rule
[ "ORDERING" [ IBMwlen ] whsp ] ; create index for matching rule
[ "APPROX" [ IBMwlen ] whsp ] ; create index for matching rule
[ "SUBSTR" [ IBMwlen ] whsp ] ; create index for matching rule
[ "REVERSE" [ IBMwlen ] whsp ] ; reverse index for substring
whsp ")"
IBMAccessClass =
"NORMAL" / ; this is the default
"SENSITIVE" /
"CRITICAL" /
"RESTRICTED" /
"SYSTEM" /
"OBJECT"
IBMwlen = whsp len
( attr-oid ... SYNTAX syntax-oid{len} ... )
can be used to indicate that the attributetype with oid attr-oid has a maximum length.
A matching rule provides guidelines for string comparison during a search operation. These rules are divided into three categories:
| Equality matching rules | ||
|---|---|---|
| Matching Rule | OID | Syntax |
| caseExactIA5Match | 1.3.6.1.4.1.1466.109.114.1 | Directory String syntax |
| caseExactMatch | 2.5.13.5 IA5 | String syntax |
| caseIgnoreIA5Match | 1.3.6.1.4.1.1466.109.114.2 | IA5 String syntax |
| caseIgnoreMatch | 2.5.13.2 | Directory String syntax |
| distinguishedNameMatch | 2.5.13.1 | DN - distinguished name |
| generalizedTimeMatch | 2.5.13.27 | Generalized Time syntax |
| ibm-entryUuidMatch | 1.3.18.0.2.22.2 | Directory String syntax |
| integerFirstComponentMatch | 2.5.13.29 | Integer syntax - integral number |
| integerMatch | 2.5.13.14 | Integer syntax - integral number |
| objectIdentifierFirstComponentMatch | 2.5.13.30 | String for containing OIDs. The OID is a string containing digits (0-9) and decimal points (.). |
| objectIdentifierMatch | 2.5.13.0 | String for containing OIDs. The OID is a string containing digits (0-9) and decimal points (.) |
| octetStringMatch | 2.5.13.17 | Directory String syntax |
| telephoneNumberMatch | 2.5.13.20 | Telephone Number syntax |
| uTCTimeMatch | 2.5.13.25 | UTC Time syntax |
| Ordering matching rules | ||
|---|---|---|
| Matching rule | OID | Syntax |
| caseExactOrderingMatch | 2.5.13.6 | Directory String syntax |
| caseIgnoreOrderingMatch | 2.5.13.3 | Directory String syntax |
| distinguishedNameOrderingMatch | 1.3.18.0.2.4.405 | DN - distinguished name |
| generalizedTimeOrderingMatch | 2.5.13.28 | Generalized Time syntax |
| Substring matching rules | ||
|---|---|---|
| Matching rule | OID | Syntax |
| caseExactSubstringsMatch | 2.5.13.7 | Directory String syntax |
| caseIgnoreSubstringsMatch | 2.5.13.4 | Directory String syntax |
| telephoneNumberSubstringsMatch | 2.5.13.21 | Telephone Number syntax |
Index rules attached to attributes make it possible to retrieve information faster. If only the attribute is given, no indexes are maintained. IBM Directory provides the following indexing rules:
Specifying an indexing rule for an attribute controls the creation and maintenance of special indexes on the attribute values. This greatly improves the response time to searches with filters which include those attributes. The five possible types of indexing rules are related to the operations applied in the search filter.
For example:
"cn = John Doe"
For example:
"sn >= Doe"
For example:
"sn ~= doe"
For example:
"sn = McC*" "cn = J*Doe"
For example:
"sn = *baugh"
At a minimum, it is recommended that you specify equal indexing on any attributes that are to be used in search filters.
You can display syntax either alphabetically or by OID. Select
Syntax or OID and click Sort.
Similarly you can reverse the list order by selecting Descending
and clicking Sort.
| Syntax | OID |
|---|---|
| Attribute Type Description syntax | 1.3.6.1.4.1.1466.115.121.1.3 |
| Binary - octet string | 1.3.6.1.4.1.1466.115.121.1.5 |
| Boolean - TRUE/FALSE | 1.3.6.1.4.1.1466.115.121.1.7 |
| Directory String syntax | 1.3.6.1.4.1.1466.115.121.1.15 |
| DIT Content Rule Description syntax | 1.3.6.1.4.1.1466.115.121.1.16 |
| DITStructure Rule Description syntax | 1.3.6.1.4.1.1466.115.121.1.17 |
| DN - distinguished name | 1.3.6.1.4.1.1466.115.121.1.12 |
| Generalized Time syntax | 1.3.6.1.4.1.1466.115.121.1.24 |
| IA5 String syntax | 1.3.6.1.4.1.1466.115.121.1.26 |
| IBM Attribute Type Description | 1.3.18.0.2.8.1 |
| Integer syntax - integral number | 1.3.6.1.4.1.1466.115.121.1.27 |
| LDAP Syntax Description syntax | 1.3.6.1.4.1.1466.115.121.1.54 |
| Matching Rule Description | 1.3.6.1.4.1.1466.115.121.1.30 |
| Matching Rule Use Description | 1.3.6.1.4.1.1466.115.121.1.31 |
| Name Form Description | 1.3.6.1.4.1.1466.115.121.1.35 |
| Object Class Description syntax | 1.3.6.1.4.1.1466.115.121.1.37 |
| String for containing OIDs. The OID is a string containing digits (0-9) and decimal points (.). See Object identifier (OID). | 1.3.6.1.4.1.1466.115.121.1.38 |
| Telephone Number syntax | 1.3.6.1.4.1.1466.115.121.1.50 |
| UTC Time syntax. UTC-Time is time string format defined by ASN.1 standards. See ISO 8601 and X680. Use this syntax for storing time values in UTC-Time format. See Generalized and UTC time. | 1.3.6.1.4.1.1466.115.121.1.53 |
An object identifier (OID) is a string, of decimal numbers, that uniquely identifies an object. These objects are typically an object class or an attribute. These numbers can be obtained from the IANA (Internet Assigned Number Authority). The IANA Website is located at: http://www.iana.org/iana/.
If you do not have an OID, you can specify the object class or attribute name appended with -oid. For example, if you create the attribute tempID, you can specify the OID as tempID-oid.
There is one subschema entry per server. All entries in the directory have an implied subschemaSubentry attribute type. The value of the subschemaSubentry attribute type is the DN of the subschema entry that corresponds to the entry. All entries under the same server share the same subschema entry, and their subschemaSubentry attribute type has the same value. The subschema entry has the hardcoded DN 'cn=schema'.
The subschema entry belongs to the object classes 'top', 'subschema', and 'IBMsubschema'. The 'IBMsubschema' object class has no MUST attributes and one MAY attribute type ('IBMattributeTypes').
The IBMsubschema object class is used only in the subschema entry as follows:
( <objectClass-oid-TBD> NAME 'IBMsubschema' AUXILIARY
MAY IBMattributeTypes )
The ldap_search() API can be used to query the subschema entry, as shown in the following example:
DN : "cn=schema" search scope : base filter : objectclass=subschema or objectclass=*
This example retrieves the full schema. To retrieve all of the values of selected attribute types, use the attrs parameter in ldap_search. You cannot retrieve only a specific value of a specific attribute type.
See the IBM Directory Version 5.1: Client SDK Programming Reference for more information about the ldap_search API.
To perform a dynamic schema change, use the ldap_modify API with a DN of "cn=schema". It is permissible to add, delete, or replace only one schema entity (for example, an attribute type or an object class) at a time.
To delete a schema entity, provide the oid in parentheses:
( oid )
You can also provide a full description. In either case, the matching rule used to find the schema entity to delete is objectIdentifierFirstComponentMatch.
To add or replace a schema entity, you MUST provide a LDAP Version 3 definition and you MAY provide the IBM definition. In all cases, you must provide only the definition or definitions of the schema entity that you want to affect.
For example, to delete the attribute type 'cn' (its OID is 2.5.4.3), use ldap_modify() with:
LDAPMod attr;
LDAPMod *attrs[] = { &attr, NULL };
char *vals [] = { "( 2.5.4.3 )", NULL };
attr.mod_op = LDAP_MOD_DELETE;
attr.mod_type = "attributeTypes";
attr.mod_values = vals;
ldap_modify_s(ldap_session_handle, "cn=schema", attrs);
To add a new attribute type bar with OID 20.20.20 that has a NAME of length 20 chars:
char *vals1[] = { "( 20.20.20 NAME 'bar' SUP NAME )", NULL };
char *vals2[] = { "( 20.20.20 LENGTH 20 )", NULL };
LDAPMod attr1;
LDAPMod attr2;
LDAPMod *attrs[] = { &attr1, &attr2, NULL };
attr1.mod_op = LDAP_MOD_ADD;
attr1.mod_type = "attributeTypes";
attr1.mod_values = vals1;
attr2.mod_op = LDAP_MOD_ADD;
attr2.mod_type = "IBMattributeTypes";
attr2.mod_values = vals2;
ldap_modify_s(ldap_session_handle, "cn=schema", attrs);
See Working with attributes for examples using the Web Administration Tool and the ldapmodify command.
See the IBM Directory Version 5.1: Client SDK Programming Reference for more information about the ldap_modify API.
Dynamic schema changes can be performed only by a replication supplier or the administrator DN.
When a dynamic schema change is performed, it is replicated just like any other ldap_modify operation.
Not all schema changes are allowed. Change restrictions include the following:
Changes to the schema that affect the operation of the server are not allowed. The following schema definitions are required by the directory server. They must not be changed.
When the server is initialized, the schema files are read and checked for consistency and correctness. If the checks fail, the server fails to initialize and issues an error message. During any dynamic schema change, the resulting schema is also checked for consistency and correctness. If the checks fail, an error is returned and the change fails. Some checks are part of the grammar (for example, an attribute type can have at most one supertype, or an object class can have any number of superclasses).
The following items are checked for attribute types:
The following items are checked for object classes:
When an entry is added or modified through an LDAP operation, the entry is checked against the schema. By default, all checks listed in this section are performed. However, you can selectively disable some of them by providing an ibm-slapdSchemaCheck value to the ibmslapd.conf configuration directive. See the IBM Directory Server Version 5.1 Installation and Configuration Guide for information about schema configuration attributes.
To comply with the schema an entry is checked for the following conditions:
The Directory-Enabled Network (DEN) specification defines a standard schema form that stores and describes the relationships among objects that represent users, applications, network elements, and networking services.
To support DEN, the IBM Directory Server provides the following features:
The parser used by the IBM Directory Server allows the attribute values of schema attribute types (objectClasses and attributeTypes ) to be specified using the grammar of iPlanet. For example, descrs and numeric-oids can be specified with surrounding single quotation marks (as if they were qdescrs). However, the schema information is always made available through ldap_search. As soon as a single dynamic change (using ldap_modify) is performed on an attribute value in a file, the whole file is replaced by one where all attribute values follow the IBM Directory Version 5.1 specifications. Because the parser used on the files and on ldap_modify requests is the same, an ldap_modify that uses the iPlanet grammar for attribute values is also handled correctly.
When a query is made on the subschema entry of a iPlanet server, the resulting entry can have more than one value for a given OID. For example, if a certain attribute type has two names (such as 'cn' and 'commonName'), then the description of that attribute type is provided twice, once for each name. The IBM Directory Server can parse a schema where the description of a single attribute type or object class appears multiple times with the same description (except for NAME and DESCR). However, when the IBM Directory Server publishes the schema it provides a single description of such an attribute type with all of the names listed (the short name comes first). For example, here is how iPlanet describes the common name attribute:
( 2.5.4.3 NAME 'cn'
DESC 'Standard Attribute'
SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' )
( 2.5.4.3 NAME 'commonName'
DESC 'Standard Attribute, alias for cn'
SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' )
This is how the IBM Directory Server describes it:
( 2.5.4.3 NAME ( 'cn' 'commonName' ) SUP name )
The IBM Directory Server supports subtypes. If you do not want 'cn' to be a subtype of name (which deviates from the standard), you can declare the following:
( 2.5.4.3 NAME ( 'cn' 'commonName' )
DESC 'Standard Attribute'
SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' )
The first name ('cn') is taken as the preferred or short name and all other names after 'cn' as alternate names. From this point on, the strings '2.3.4.3', 'cn' and 'commonName' (as well as their case-insensitive equivalents) can be used interchangeably within the schema or for entries added to the directory.
There are different notations used to designate date and time-related information. For example, the fourth day of February in the year 1999 can be written as:
2/4/99 4/2/99 99/2/4 4.2.1999 04-FEB-1999
as well as many other notations.
IBM Directory Server standardizes the timestamp representation by requiring the LDAP servers to support two syntaxes:
YYYYMMDDHHMMSS[.|,fraction][(+|-HHMM)|Z]
There are 4 digits for the year, 2 digits each for the month, day, hour, minute, and second, and an optional fraction of a second. Without any further additions, a date and time is assumed to be in a local time zone. To indicate that a time is measured in Coordinated Universal Time, append a capital letter Z to a time or a local time differential. For example:
"19991106210627.3"
which in local time is 6 minutes, 27.3 seconds after 9 p.m. on 6 November 1999.
"19991106210627.3Z"
which is the coordinated universal time.
"19991106210627.3-0500"
which is local time as in the first example, with a 5 hour difference in relation to the coordinated universal time.
If you designate an optional fraction of a second, a period or a comma is required. For local time differential, a '+' or a '-' must precede the hour-minute value
YYMMDDHHMM[SS][(+ | -)HHMM)|Z]
There are 2 digits each for the year, month, day, hour, minute, and optional second fields. As in GeneralizedTime, an optional time differential can be specified. For example, if local time is a.m. on 2 January 1999 and the coordinated universal time is 12 noon on 2 January 1999, the value of UTCTime is either:
"9901021200Z"
or
"9901020700-0500"
If the local time is a.m. on 2 January 2001 and the coordinated universal time is 12 noon on 2 January 2001, the value of UTCTime is either:
"0101021200Z"
or
"0101020700-0500"
UTCTime allows only 2 digits for the year value, therefore the usage is not recommended.
The supported matching rules are generalizedTimeMatch for equality and generalizedTimeOrderingMatch for inequality. Substring search is not allowed. For example, the following filters are valid:
generalized-timestamp-attribute=199910061030 utc-timestamp-attribute>=991006 generalized-timestamp-attribute=*
The following filters are not valid:
generalized-timestamp-attribute=1999* utc-timestamp-attribute>=*1010
Replication is a technique used by directory servers to improve performance and reliability. The replication process keeps the data in multiple directories synchronized.
Replication provides two main benefits:
Replication topology is managed in a new way in the IBM Directory Server Version 5.1. Some terminology used in describing replication:
Specific entries in the directory are identified as the roots of replicated subtrees, by adding the ibm-replicationContext objectclass to them. Each subtree is replicated independently. The subtree continues down through the directory information tree (DIT) until reaching the leaf entries or other replicated subtrees. Entries are added below the root of the replicated subtree to contain the replication configuration information. These entries are one or more replica group entries, under which are created replica subentries. Associated with each replica subentry are replication agreements that identify the servers that are supplied (replicated to) by each server, as well as defining the credentials and schedule information.
Through replication, a change made to one directory is propagated to one or more additional directories. In effect, a change to one directory shows up on multiple different directories. The IBM Directory supports an expanded master-slave replication model. Replication topologies are expanded to include:
The advantage of replicating by subtrees is that a replica does not need to replicate the entire directory. It can be a replica of a part, or subtree, of the directory.
The expanded model changes the concept of master and replica. These terms no longer apply to servers, but rather to the roles that a server has regarding a particular replicated subtree. A server can act as a master for some subtrees and as a replica for others. The term, master, is used for a server that accepts client updates for a replicated subtree. The term, replica, is used for a server that only accepts updates from other servers designated as a supplier for the replicated subtree.
There are three types of directories as defined by function:
master/peer, cascading, and
read-only.
| Master/peer | The master/peer server contains the master directory information from
where updates are propagated to the replicas. All changes are made and
occur on the master server, and the master is responsible for propagating
these changes to the replicas.
There can be several servers acting as masters for directory information, with each master responsible for updating other master servers and replica servers. This is referred to as peer replication. Peer replication can improve performance and reliability. Performance is improved by providing a local server to handle updates in a widely distributed network. Reliability is improved by providing a backup master server ready to take over immediately if the primary master fails. Notes:
|
| Cascading (forwarding) | A cascading server is a replica server that replicates all changes sent to it. This contrasts to a master/peer server in that a master/peer server only replicates changes that are made by clients connected to that server. A cascading server can relieve the replication workload from the master servers in a network which contains many widely dispersed replicas. |
| Replica (read-only) | An additional server that contains a copy of directory information. The replicas are copies of the master (or the subtree that it is a replica of). The replica provides a backup of the replicated subtree. |
You can request updates on a replica server, but the update is actually forwarded to the master server by returning a referral to the client. If the update is successful, the master server then sends the update to the replicas. Until the master has completed replication of the update, the change is not reflected on the replica server where it was originally requested. If the replication fails, it is repeated even if the master is restarted. Changes are replicated in the order in which they are made on the master.
If you are no longer using a replica, you must remove the replica agreement from the supplier. Leaving the definition causes the server to queue up all updates and use unnecessary directory space. Also, the supplier continues trying to contact the missing consumer to retry sending the data.
A replication agreement is an entry in the directory with the object class ibm-replicationAgreement created beneath a replica subentry to define replication from the server represented by the subentry to another server. These objects are similar to the replicaObject entries used by prior versions of the Directory Server. The replication agreement consists of the following items:
The user friendly name might be the consumer server name or some other descriptive string.
The consumer server id is used by the administrative GUI to traverse the topology. Given the consumer's server ID, the GUI can find the corresponding subentry and its agreements. To aid in enforcing the accuracy of the data, when the supplier binds to the consumer, it retrieves the server IDfrom the root DSE and compares it to the value in the agreement. A warning is logged if the server IDs do not match.
Because the replication agreement can be replicated, a DN to a credentials object is used. This allows the credentials to be stored in a nonreplicated area of the directory. Replicating the credentials objects (from which 'clear text' credentials must be obtainable) represents a potential security exposure. The cn=localhost suffix is an appropriate default location for creating credentials objects. Use of a separate object also makes it easier to support various authentication methods; new object classes can be created rather than trying to make sense of numerous optional attributes.
Object classes are defined for each of the supported authentication methods:
You can designate that part of a replicated subtree not be replicated by adding the ibm-replicationContext auxiliary class to the root of the subtree, without defining any replica subentries.
To define a replication topology, you must
This task designates an entry as the root of an independently replicated subtree and creates a ibm-replicasubentry representing this server as the single master for the subtree. To create a replicated subtree, you must designate the subtree that you want the server to replicate. Expand the Replication management category in the navigation area and click Manage topology.
If the entry that you trying to add is not a suffix in the server, before you can use the Add subtree function, you must ensure that its ACLs defined as follows:
ownersource: <same as the entry DN> ownerpropagate: TRUE aclsource: <same as the entry DN> aclpropagate: TRUE
ibm-filteraclinherit: FALSE
To satisfy the ACL requirements, if the entry is not a suffix in the server, edit the ACL for that entry in the Manage entries panel. Select the entry and click Edit ACL. If you want to add Non-fltered ACLs, select that tab and add an entry cn=this with the role access-id for both ACLs and owners. Ensure that Propagate ACLs and Propagate owner are checked. If you want to add Fltered ACLs select that tab and add an entry cn=this with the role access-id for both ACLs and owners. Ensure that Accumulate filtered ACLs is unchecked and that Propagate owner is checked. See Working with Access Control Lists for more detailed information.
ldap://<myservername>.<mylocation>.<mycompany>.com
To add additional masters (peers), you first add the server as a read-only replica of the existing masters (see Creating a replica server), initialize the directory data, and then promote the server to be a master (see Moving or promoting a server).
Initially, the ibm-replicagroup object created by this process inherits the ACL of the root entry for the replicated subtree. These ACLs might be inappropriate for controlling access to the replication information in the directory.
For the Add subtree operation to be successful, the entry DN which you are adding must have correct ACLs, if it is not a suffix in the server.
Use the Edit ACLs function to set ACLs for the replication information associated with the newly created replicated subtree (see Editing access control lists).
set LDAP_LOCK_REC=anyvalue
Expand the Replication management category in the navigation area of the Web Administration Tool and click Manage credentials
Placing credentials in cn=replication,cn=localhost is considered more secure. Credentials placed in the replicated subtree are created beneath the ibm-replicagroup=default entry for that subtree.
By default, the supplier uses its own service principal to bind with the consumer. For example, if the supplier is named master.our.org.com and the realm is SOME.REALM, the DN is ibm-Kn=ldap/master1.our.org.com@SOME.REALM. If there is more than one supplier, you must specify the principal and password to be used by all of the suppliers.
See Secure Sockets Layer for additional information.
Expand the Replication management category in the navigation area and click Manage topology.
On the Server tab of the Add replica window:
On the Additional tab:
Placing credentials in cn=replication,cn=localhost is considered more secure. Credentials placed in the replicated subtree are created beneath the ibm-replicagroup=default entry for that subtree.
See Creating credentials for additional information on agreement credentials.
If your network has a mix of servers at different releases, capabilities are available on later releases that are not available on earlier releases. Some capabilities, like filter ACLs and password policy, make use of operational attributes that are replicated with other changes. In most cases, if these features are used, you want all servers to support them. If all of the servers do not support the capability, you do not want to use it. For example, you would not want different ACLs in effect on each server. However, there might be cases where you might want to use a capability on the servers that support it, and not have changes related to the capability replicated to servers that do not support the capability. In such cases, you can use the capabilities list to mark certain capabilities to not be replicated.
After creating the replica, you must now export the topology from the master to the replica. This is a manual procedure.
On the master server create an LDIF file for the data. To copy all the data contained on the master server, issue the command:
db2ldif -o <masterfile.ldif>
If you want to copy just the data from a single subtree the command is:
db2ldif -o <masterfile.ldif> -s <subtreeDN>
On the machine where you are creating the replica:
ldif2db -r no -i <masterfile.ldif>
The replication agreements, schedules, credentials (if stored in the replicated subtree) and entry data are loaded on the replica.
You need to change the replica's configuration to identify who is authorized to replicate changes to it, and add a referral to a master.
On the machine where you are creating the replica:
See Creating credentials.
See Modifying replication properties for additional information.
The replica is in a suspended state and no replication is occurring. After you have finished setting up your replication topology, you must click Manage queues, select the replica and click Suspend/resume to start replication. See Managing queues for more detailed information. The replica now receives updates from the master.
If you have set up a replication topology (see Creating a replicated subtree (master server)) with a master (server1) and a replica (server2), you can change the role of server2 to that of a forwarding server. To do this you need to create a new replica (server3) under server2.
On the Server tab of the Add replica window:
On the Additional tab:
Placing credentials in cn=replication,cn=localhost is considered more secure. Credentials placed in the replicated subtree are created beneath the ibm-replicagroup=default entry for that subtree.
See Creating credentials for additional information on agreement credentials.
If your network has a mix of servers at different releases, capabilities are available on later releases that are not available on earlier releases. Some capabilities, like filter ACLs and password policy, make use of operational attributes that are replicated with other changes. In most cases, if these features are used, you want all servers to support them. If all of the servers do not support the capability, you do not want to use it. For example, you would not want different ACLs in effect on each server. However, there might be cases where you might want to use a capability on the servers that support it, and not have changes related to the capability replicated to servers that do not support the capability. In such cases, you can use the capabilities list to mark certain capabilities to not be replicated.
Your topology in now:
Topologies are specific to the replicated subtrees.
Expand the Replication management category in the navigation area and click Manage topology.
The topology is displayed in the Replication topology list. Expand the topologies by clicking the blue triangles. From this list you can:
See Creating a replica server.
You can change the following information for the replica:
On the Server tab you can only change
On the Additional tab you can change:
The change in the topology tree reflects the moving of the server.
See Peer to peer replication for more information.
Expand the Replication management category in the navigation area and click Manage topology.
ldap://<myservername>.<mylocation>.<mycompany>.com
set LDAP_LOCK_REC=anyvalue
Use this option to change the URL of the master server that this subtree and its replicas send updates to. You need do this if you change the port number or host name of the master server, change the master to a different server
ldap://<mynewservername>.<mylocation>.<mycompany>.com
Depending on the role being played by the server on this subtree (whether it is a master, replica or forwarding), different labels and buttons appear on the panel.
The subtree is removed from the Replicated subtree list.
This function is useful when you want to perform maintenance on or make changes to the topology. It minimizes the number of updates that can be made to the server. A quiesced server does not accept client requests. It accepts requests only from an administrator using the Server Administration control.
This function is Boolean.
Replication information (replica subentries, replication agreements, schedules, possibly credentials) are stored under a special object, ibm-replicagroup=default. The ibm-replicagroup object is located immediately beneath the root entry of the replicated subtree. By default, this subtree inherits ACL from the root entry of the replicated subtree. This ACL might not be appropriate for controlling access to replication information.
Required authorities:
To view ACL properties using the Web Administration Tool utility and to work with ACLs, see Working with Access Control Lists.
See Access Control Lists for additional information.
Expand the Replication management category in the navigation area and click Manage replication properties.
On this panel you can:
The subtree of the supplier is added to the Supplier information list.
The subtree is removed from the Supplier information list.
You can optionally define replication schedules to schedule replication for particular times, or to not replicate during certain times. If you do not use a schedule, the server schedules replication whenever a change is made. This is equivalent to specifying a schedule with immediate replication starting at 12:00 AM on all days.
Expand the Replication management category in the navigation area and click Manage schedules.
On the Weekly schedule tab, select the subtree for which you want to create the schedule and click Show schedules. If any schedules exist, they are displayed in the Weekly schedules box. To create or add a new schedule:
See Creating a daily schedule for more information on setting up daily schedules.
Expand the Replication management category in the navigation area and click Manage schedules.
On the Daily schedule tab, select the subtree for which you want to create the schedule and click Show schedules. If any schedules exist, they are displayed in the Daily schedules box. To create or add a new schedule:
For example:
| Replication type | Start time |
|---|---|
| Immediate | 12:00 AM |
| Once | 10:00 AM |
| Once | 2:00 PM |
| Immediate | 4:00 PM |
| Once | 8:00 PM |
In this schedule, the first replication event occurs at midnight and updates any pending changes prior to that time. Replication updates continue to be made as they occur until 10:00 AM. Updates made between 10:00 AM and 2:00 PM wait until 2:00 PM to be replicated. Any updates made between 2:00 PM and 4:00 PM wait the replication event scheduled at 4:00 PM, afterwards replication updates continue until the next scheduled replication event at 8:00 PM. Any updates made after 8:00 PM wait until the next scheduled replication event.
This task allows you to monitor status of replication for each replication agreement (queue) used by this server.
Expand the Replication management category in the navigation area and click Manage queues.
Select the replica for which you want to manage the queue.
If you clicked Queue details, three tabs are displayed:
The Status tab displays the replica name, its subtree, its status, and a record of replication times. From this panel you can suspend or resume replication by clicking Resume. Click Refresh to update the queue information.
The Last attempted details tab gives information about the last update attempt. If an entry is not able to be loaded press Skip blocking entry to continue replication with the next pending entry. Click Refresh to update the queue information.
The Pending changes tab shows all the pending changes to the replica. If replication is blocked you can delete all the pending changes by clicking Skip all. Click Refresh to update the list of pending changes to reflect any new update or updates that have been processed.
Peer replication is a replication topology in which multiple servers are masters. However, unlike a multi-master environment, no conflict resolution is done among peer servers. LDAP servers accept the updates provided by peer servers, and update their own copies of the data. No consideration is given for the order the updates are received, or whether multiple updates conflict.
Use peer replication only in environments where the update vectors are well known. Updates to particular objects within the directory must be done only by one peer server. This is intended to prevent the scenario of one server deleting an object, followed by another server modifying the object. This scenario creates the possibility of a peer server receiving a delete command followed by a modify command; which creates a conflict.
Use this high level overview as a guide for setting up a complex replication topology.
Using the forwarding topology created in Setting up a forwarding server, you can promote a server to be a peer. In this example you are going to promote the replica (server3) to be a peer to the master server (server1).
As it can be seen from the topology, an agreement between server2 and server3 which was exisitng previously was deleted. An agreement between server1 and server3 is created (required for a peer master) A subentry corresponding to the machine server3 is also created. To complete the setting up of a peer master, an agreement from server3 to server1 must be added.
The peer topology is now:
If you wanted to promote server2 so that the topology contains three master-peer servers, use the same procedure that was used to promote server3. Agreements must be made among all peer servers. The three-peer topology is now:
To change the role of a server from a master to a replica do the following:
The following are examples of setting up replication using the command line utilities and an LDIF file. The scenarios are of increasing complexity:
Each of these scenarios assume that you are creating new replicated subtrees.
dn: o=ibm,c=us objectclass: organization objectclass: ibm-replicationContext
is the subtree you want to create. If this entry already exists, then modify it to add objclass=ibm-replicationContext instead of adding the entire entry.
To create a replica for a subtree, you need to create a replica agreement between the master and the replica, see Replication agreements. This agreement needs to be loaded on both the master and the replica.
The relationship between the two servers is that the master is a supplier to the replica and the replica is a consumer of the master.
To create the master (master) and replica (replica1) for the subtree o=ibm,c=us:
###Replication Context - needs to be on all suppliers and consumers
dn: cn=replication,cn=localhost
objectclass: container
dn: o=ibm,c=us
objectclass: organization
objectclass: ibm-replicationContext
###Copy the following to servers at v5.1 or later.
###Replica Group
dn: ibm-replicaGroup=default, o=IBM, c=US
objectclass: top
objectclass: ibm-replicaGroup
ibm-replicaGroup: default
###Bind Credentials/method to replica server - replication agreement
###points to this.
dn: cn=replica1 BindCredentials,cn=replication,cn=localhost
objectclass: ibm-replicationCredentialsSimple
cn: replica1 BindCredentials
replicaBindDN: cn=master
replicaCredentials: master
description: Bindmethod of master to replica1
###Replica SubEntry
dn: ibm-replicaServerId=<master-uuid>,ibm-replicaGroup=default,o=IBM, c=US
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <master-uuid>
ibm-replicationServerIsMaster: true
cn: master
description: master server
###Replication Agreement to Replica Server
dn: cn=replica1,ibm-replicaServerId=<master-uuid>,
ibm-replicaGroup=default,o=IBM,c=US
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica1
ibm-replicaConsumerId: <replica1-uuid>
ibm-replicaUrl: ldap://<replicahostname:replicaport>
ibm-replicaCredentialsDN: cn=replica1 BindCredentials,cn=replication,
cn=localhost
description: replica server number one
ldif2db -r no -i <myreplicainfofile>
db2ldif -o <masterfile.ldif>
See db2ldif utility for more information.
dn: cn=Master Server, cn=configuration objectclass: ibm-slapdReplication cn: Master Server ibm-slapdMasterDN: <cn=masterbndn> ibm-slapdMasterPW: <masterbnpw> ibm-slapdMasterReferral: ldap://<masterhostname>:<masterport>/
ldif2db -r no -i <masterfile.ldif>
This procedure is similar to the one for a single master and replica, except that the entire topology must be added to each of the servers and the content of the agreement information file is more complex. The file now includes information for the forwarding server and supplier-consumer information.
The supplier-consumer relationship for this scenario is:
To create the master (master), a forwarder (forwarder1), and replica (replica1) for the subtree o=ibm,c=us:
dn: cn=replication,cn=localhost
objectclass: container
dn: o=ibm,c=us
objectclass: organization
objectclass: ibm-replicationContext
dn: ibm-replicaGroup=default, o=ibm,c=us
objectclass: top
objectclass: ibm-replicaGroup
ibm-replicaGroup: default
dn: cn=forwarder1 BindCredentials,cn=replication,cn=localhost
objectclass: ibm-replicationCredentialsSimple
#or ibm-replicationCredentialsExternal or
#ibm-replicationCredentialsKerberos
cn: forwarder1 BindCredentials
replicaBindDN: <cn=forw1bnddn>
replicaCredentials: <forw1bndpw>
cn:forwarder1 BindCredentials
description: Bindmethod of master to forwarder1
dn: cn=replica1 BindCredentials,cn=replication,cn=localhost
objectclass: ibm-replicationCredentialsSimple
cn: replica1 BindCredentials
replicaBindDN: <cn=rep1bnddn>
replicaCredentials: <rep1bndpw>
description: Bindmethod of forwarder1 to replica1
dn: ibm-replicaServerId=<master-uuid>,ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <master-uuid> #whatever the id is in the config
ibm-replicationServerIsMaster: true #true if master, false if forwarder
cn: master
description: master ibm-replicaSubentry
dn: ibm-replicaServerId=<forwarder1-uuid>,ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <forwarder1-uuid>ibm-replicationServerIsMaster: false
cn: forwarder1
description: forwarder1 ibm-replicaSubentry
dn: cn=forwarder1,ibm-replicaServerId=<master-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: forwarder1
ibm-replicaConsumerId: <forwarder1-uuid>
ibm-replicaUrl: ldap://<forwarder1hostname:forwarder1port>
ibm-replicaCredentialsDN: cn=forwarder1 BindCredentials,cn=replication,
cn=localhost
description: master1 to forwarder1 agreement
dn: cn=replica1,ibm-replicaServerId=<forwarder1-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica1
ibm-replicaConsumerId: <replica1-uuid>-uuid
ibm-replicaUrl: ldap://<replica1hostname:replica1port>
ibm-replicaCredentialsDN: cn=replica1 BindCredentials,cn=replication,
cn=localhost
description: forwarder1 to replica1 agreement
ldif2db -r no -i <myreplicainfofile>
db2ldif -o <masterfile.ldif>
See db2ldif utility for more information.
dn: cn=Master Server, cn=configuration
objectclass: ibm-slapdReplication
cn: Master Server
ibm-slapdMasterDN: <cn=masterbnddn>
ibm-slapdMasterPW: <masterbndp>w
ibm-slapdMasterReferral: ldap://masterhostname:masterport/
#referral to master when trying to add to consumer.
#Referral can also be added to replicaContext, which would be
#checked first for a valid server.
dn: cn=Master Server, cn=configuration objectclass: ibm-slapdReplication cn: Master Server ibm-slapdMasterDN: <cn=forw1bndn> ibm-slapdMasterPW: <forw1bnpw> ibm-slapdMasterReferral: ldap://forw1hostname:forw1port/
ldif2db -r no -i <masterfile.ldif>
In this example the topology is more complex. It includes two peer-masters (peer1 and peer2), two forwarders (forwarder1 and forwarder2) and four replicas (replica1, replica2, replica3, and replica4). The relationship among the servers is as follows:
There is no interaction between forwarder1 and forwarder2.
To create the peer-masters (peer1 and peer2), the forwarders (forwarder1 and forwarder2), and the replicas (replica1, replica2, replica3, and replica4) for the subtree o=ibm,c=us:
dn: cn=MasterServer, cn=configuration objectclass: ibm-slapdReplication cn: Master Server ibm-slapdMasterDN: cn=master ibm-slapdMasterPW: master
dn: cn=simple,cn=replication,cn=localhost objectclass: ibm-replicationCredentialsSimple cn: peer2 BindCredentials replicaBindDN: cn=master replicaCredentials: master description: Bindmethod for topology
ldif2db -r no -i <mycredentialsfile>
ldif2db -r no -i <mycredentialsfile>
on each machine.
dn: cn=replication,cn=localhost
objectclass: container
dn: o=ibm,c=us
o: ibm
objectclass: top
objectclass: organization
objectclass: ibm-replicationContext
objectclass: ibm-replicaGroup
ibm-replicaGroup: default
dn: ibm-replicaGroup=default, o=ibm,c=us
objectclass: top
objectclass: ibm-replicaGroup
ibm-replicaGroup: default
dn: ibm-replicaServerId=<peer1-uuid>,ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <peer1-uuid>
ibm-replicationServerIsMaster: true
cn: peer1
description: peer1 server
dn: ibm-replicaServerId=<peer2-uuid>,ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <peer2-uuid>
ibm-replicationServerIsMaster: true
cn: peer2
description: peer2 server
dn: ibm-replicaServerId=<forwarder1-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <forwarder1-uuid>ibm-replicationServerIsMaster: false
cn: forwarder1
description: forwarder server number one
dn: ibm-replicaServerId=<forwarder2-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <forwarder2-uuid>
ibm-replicationServerIsMaster: false
cn: forwarder2
description: forwarder server number two
#peer1 to peer2 agreement
dn: cn=peer2,ibm-replicaServerId=<peer1-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: peer2
ibm-replicaConsumerId: <peer2-uuid>
ibm-replicaUrl: ldap://<peer2hostname:peer2port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: peer2 server
#peer1 to forwarder1 agreement
dn: cn=forwarder1,ibm-replicaServerId=<peer1-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: forwarder1
ibm-replicaConsumerId: <forwarder1-uuid>
ibm-replicaUrl: ldap://<forwarder1hostname:forwarder1port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: forwarder server one
#peer1 to forwarder2 agreement
dn: cn=forwarder2,ibm-replicaServerId=<peer1-uuid>
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: forwarder2
ibm-replicaConsumerId: <forwarder2-uuid>
ibm-replicaUrl: ldap://<forwarder2hostname:forwarder2port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: forwarder server two
#peer2 to peer1 agreement
dn: cn=peer1,ibm-replicaServerId=<peer2-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: forwarder1
ibm-replicaConsumerId: <peer1-uuid>
ibm-replicaUrl: ldap://<peer1hostname:peer1port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: peer server one
#peer2 to forwarder1 agreement
dn: cn=forwarder1,ibm-replicaServerId=<peer2-uuid>
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: forwarder1
ibm-replicaConsumerId: forwarder1-uid
ibm-replicaUrl: ldap://<forwarder1hostname:forwarder1port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: forwarder server one
#peer2 to forwarder2 agreement
dn: cn=forwarder2,ibm-replicaServerId=<peer2-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: forwarder2
ibm-replicaConsumerId: <forwarder2-uuid>
ibm-replicaUrl: ldap://$<forwarder2hostname:forwarder2port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: forwarder server two
#forwarder1 to replica1 agreement
dn: cn=replica1,ibm-replicaServerId=<forwarder1-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica1
ibm-replicaConsumerId: <replica1-uuid>
ibm-replicaUrl: ldap://<replica1hostname:replica1port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: replica server number one
#forwarder1 to replica2 agreement
dn: cn=replica2,ibm-replicaServerId=<forwarder1-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica2
ibm-replicaConsumerId: <replica2-uuid>
ibm-replicaUrl: ldap://<replica2hostname:replica2port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: replica server number two
#forwarder2 to replica3 agreement
dn: cn=replica3,ibm-replicaServerId=<forwarder2-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica3
ibm-replicaConsumerId: <replica3-uuid>
ibm-replicaUrl: ldap://<replica3hostname:replica3port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: replica server number three
#forwarder2 to replica4 agreement
dn: cn=replica4,ibm-replicaServerId=<forwarder2-uuid>,
ibm-replicaGroup=default,o=ibm,c=us
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica4
ibm-replicaConsumerId: <replica4-uuid>
ibm-replicaUrl: ldap://<replica4hostname:replica4port>
ibm-replicaCredentialsDN: cn=simple,cn=replication,cn=localhost
description: replica server number four
ldif2db -r no -i <mytopologyfile>
db2ldif -s"o=ibm,c=us" -o <mymasterfile.ldif>
See db2ldif utility for more information.
ldif2db -r no -i <masterfile.ldif>
dn: cn=MasterServer, cn=configuration cn: Master Server ibm-slapdMasterDN: cn=master ibm-slapdMasterPW: master ibm-slapdMasterReferral: ldap://peer1hostname:peer1port/
ldif2db -r no -i <masterfile.ldif>
dn: cn=MasterServer, cn=configuration cn: Master Server ibm-slapdMasterDN: cn=master ibm-slapdMasterPW: master ibm-slapdMasterReferral: ldap://peer1hostname:peer1port/
ldif2db -r no -i <masterfile.ldif>
You can specify a supplier DN and PW for a particular subtree. To do this the following information is needed on the replica and master.
To create a replica for a subtree, you need to create a replica agreement between the master and the replica, see Replication agreements. This agreement needs to be loaded on both the master and the replica. The relationship between the two servers is that the master is a supplier to the replica and the replica is a consumer of the master.
#Replication data on the master:
dn: o=IBM,c=US
objectclass: organization
dn: ou=Test,o=IBM,c=US
objectclass: organizationalunit
objectclass: ibm-replicationContext
aclentry: access-id:CN=this:object:a:normal:rwsc:sensitive:rwsc:critical:rwsc
entryowner: access-id:CN=this
dn: ibm-replicaGroup=default, ou=Test,o=IBM,c=US
objectclass: top
objectclass: ibm-replicaGroup
ibm-replicaGroup: default
dn: cn=replica1 BindCredentials, cn=localhost
objectclass: ibm-replicationCredentialsSimple
cn: replica1 BindCredentials
replicaBindDN: cn=s1
replicaCredentials: s1
description: Bindmethod of master to replica1
dn: ibm-replicaServerId=<master-uuid>,ibm-replicaGroup=default,
ou=Test,o=IBM,c=US
#master uuid is whatever the server ID is set to in your ibmslapd.conf
#on the master.
objectclass: top
objectclass: ibm-replicaSubentry
ibm-replicaServerId: <master-uuid>
ibm-replicationServerIsMaster: true
cn: master
description: master server
dn: cn=replica1,ibm-replicaServerId=<master-uuid>,ibm-replicaGroup=default,
ou=Test,o=IBM,c=US
objectclass: top
objectclass: ibm-replicationAgreement
cn: replica1
ibm-replicaConsumerId: <replica1-uuid>
#<replica1-uuid> is whatever the server ID is set to in your
#replica ibmslapd.conf file.
ibm-replicaUrl: ldap://<replica1hostname:replica1port>
ibm-replicaCredentialsDN: cn=replica1 BindCredentials, cn=localhost
description: replica server number one
ldif2db -r no -i <mysupplierinfofile>
db2ldif -o <masterfile.ldif>
See db2ldif utility for more information.
dn: cn=MasterServer, cn=configuration cn: Master Server ibm-slapdMasterDN: cn=master ibm-slapdMasterPW: <masterserverpassword> ibm-slapdMasterReferral: ldap://<masterhostname:masterport> objectclass: ibm-slapdReplication dn: cn=Supplier s1, cn=configuration cn: Supplier s1 ibm-slapdMasterDN: cn=s1 ibm-slapdMasterPW: s1 ibm-slapdReplicaSubtree: ou=Test, o=IBM, c=US objectclass: ibm-slapdSupplier
ldif2db -r no -i <masterfile.ldif>
A great deal of information related to replication activity is available using searches. To see the replication topology information related to a particular replicated subtree, you can do a one-level search with the base set to the DN of the subtree and the filter set as (objectclass=ibm-replicaGroup) to find the subentry that is the base of the topology information. If this replication context was created through the web admin interface, the name of the entry will be ibm-replicaGroup=default.
ldapsearch -D <adminDN> -w <adminPW> -b <suffixentryDN> (objectclass=*)
The objects returned will include the replica group itself, plus the following:
Agreements may also contain the following:
In addition, there are many operational attributes that provide replication status information when explicitly requested on a search. One of these attributes is associated with the entry that is the base of the replicated subtree, that is, the entry that the ibm-replicationContext objectclass was added to. If you do a base search of that entry, and request that the ibm-replicationIsQuiesced attribute is returned. This attribute is a boolean that indicates if the subtree has been quiesced. If the subtree is quiesced, no client updates are allowed (only updates from replication suppliers are accepted). There is an extended operation that can be used to quiesce a subtree, see ldapexop.
The remainder of the status-related operational attributes are all associated with a replication agreement object. These attributes are only returned when explicitly requested on the search. The attributes available are:
<time stamp> <change id> <result code> <operation> <entry DN>
<change id> <operation> <entry DN>
Requesting this attribute might return many values. Check the change count before requesting this attribute.
The IBM Directory Server Version 5.1 provides several logging utilities that can be viewed either through the Web Administration Tool or the system command line.
Notes:
The error log, ibmslapd.log, is enabled by default, to modify the error log settings:
Mar 29 11:03:23 2002 IBM Directory, Version 5.1 slapd started.
Mar 29 11:07:51 2002 Configuration read securePort 636.
Mar 29 11:07:51 2002 Plugin of type PREOPERATION is successfully
loaded from libDSP.dll.
Mar 29 11:07:51 2002 Plugin of type DATABASE is successfully loaded from
C:\Program Files\IBM\LDAP/bin/libback-rdbm.dll.
Mar 29 11:08:11 2002 Non-SSL port initialized to 389.
Mar 29 11:08:12 2002 IBM Directory, Version 5.1
slapd started.
Mar 29 11:04:05 2002 Configuration read securePort 636.
Mar 29 11:04:05 2002 Configuration read cipher specifications
mask to be 12288.
Mar 29 11:04:05 2002 Plugin of type PREOPERATION is successfully
loaded from libDSP.dll.
Mar 29 11:04:05 2002 Plugin of type DATABASE is successfully loaded from
C:\Program Files\IBM\LDAP/bin/libback-rdbm.dll
Mar 29 11:04:24 2002 Configuration file successfully read.
Mar 29 11:04:24 2002 Non-SSL port initialized to 389.
Mar 29 11:04:25 2002 IBM Directory, Version 5.1
slapd started.
Issue the command:
ldapmodify -D <AdminDN <-w >AdminPW> -i <filename>
where <filename> contains:
dn: cn=Configuration
changetype: modify
replace: ibm-slapdErrorLog
ibm-slapdErrorLog: <newpathname>
-
replace: ibm-slapdSysLogLevel
ibm-slapdSysLogLevel: {l | m | h}
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope entire
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically.
Use the following procedures to view the error log.
To view the error log issue the following command:
more /var/ldap/ibmslapd.log
where var/ldap/ibmslapd.log is your error log.
To view and clear the error log dynamically:
ldapexop -D cn=root -w root -op readlog -log slapd -lines all ldapexop -D cn=root -w root -op clearlog -log slapd
Audit logging is used to improve the security of the directory server. A default audit plug-in is provided with the server. Depending on the audit configuration parameters, this plug-in might log an audit entry in the default or specified audit log for each LDAP operation the server processed. The system administrator can use the activities stored in the audit log to check for suspicious patterns of activity in an attempt to detect security violations. If security is violated, the audit log can be used to determine how and when the problem occurred and perhaps the amount of damage done. This information is very useful, both for recovery from the violation and, possibly, in the development of better security measures to prevent future problems. You can also write your own audit plug-ins to either replace, or add more processing to, the default audit plug-in.
By default the audit log is disabled.
To enable audit logging:
Issue the command:
ldapmodify -D <AdminDN> -w <AdminPW> -i <filename>
where <filename> contains:
dn: cn=audit, cn=localhost changetype: modify replace: ibm-audit ibm-audit: true - replace: ibm-auditadd ibm-auditadd: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditbind ibm-auditbind: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditdelete ibm-auditdelete: TRUE|FALSE - replace: ibm-auditextopevent ibm-auditextopevent: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditfailedoponly ibm-auditfailedoponly: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditlog ibm-auditlog: <newpathname> - replace: ibm-auditmodify ibm-auditmodify: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditmodifydn ibm-auditmodifydn: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditsearch ibm-auditsearch: TRUE|FALSE #select TRUE to enable, FALSE to disable - replace: ibm-auditunbind ibm-auditunbind: TRUE|FALSE #select TRUE to enable, FALSE to disable
To disable audit logging:
Issue the command:
ldapmodify -D <AdminDN> -w <AdminPW> -i <filename>
where <filename> contains:
dn: cn=audit, cn=localhost changetype: modify replace: ibm-audit ibm-audit: flase
The audit log displays log entries chronologically. Each non-message entry contains a general information header followed by operation-specific data. For example,
2000-03-23-16:01:01.345-06:00--V3 Bind--bindDN:Y249bWFuYWdlcg0K --client:9.1.2.3:12345-- ConnectionID:12--received:2000-03-23-16:01:01.330-06:00 --success name: Y249bWFuYWdlcg0K authenticationChoice: simple
The header is in the following format:
Operation-specific data follows the header and displays operation-specific data, for example,
name: Y249bWFuYWdlcg0K authenticationChoice: simple
entry: cn=Jim Brown, ou=sales,o=ibm_us,c=us attributes: objectclass, cn, sn, telphonenumber
entry: cn=Jim Brown, ou=sales,o=ibm_us,c=us
object: cn=Jim Brown, ou=sales,o=ibm_us,c=us add: mail delete: telephonenumber
Use the following procedures to view the audit log:
To view the audit log :
To view the error log issue the following command:
more /var/ldap/audit.log
where /var/ldap/audit.log is your error log.
To view and clear the audit log dynamically:
ldapexop -D cn=root -w root -op readlog -log audit -lines all ldapexop -D cn=root -w root -op clearlog -log audit
Issue the command:
ldapmodify -D <AdminDN> -w <AdminPW> -i <filename>
where <filename> contains:
dn: cn=Directory, cn=RDBM Backends, cn=IBM Directory, cn=Schemas, cn=Configuration changetype: modify replace: ibm-slapdCLIErrors ibm-slapdCLIErrors: <newpathname>
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope single
"cn=Directory,cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration"
ibm-slapdCLIErrors
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically.
Use the following procedures to view the DB2 error log.
To view the DB2 error log issue the following command:
more /var/ldap/db2cli.log
where var/ldap/db2cli.log is your DB2 error log.
To view and clear the DB2 error log dynamically:
ldapexop -D cn=root -w root -op readlog -log cli -lines all ldapexop -D cn=root -w root -op clearlog -log cli
Issue the command:
ldapmodify -D <AdminDN> -w <AdminPW> -i <filename>
where <filename> contains:
dn: cn=Directory, cn=RDBM Backends, cn=IBM Directory, cn=Schemas, cn=Configuration changetype: modify replace: ibm-slapdBulkloadErrors ibm-slapdBulkloadErrors: <newpathname>
To update the settings dynamically issue the following ldapexop command:
ldapexop -D cn=root -w root -op readconfig -scope single
"cn=Directory,cn=RDBM Backends,cn=IBM Directory,cn=Schemas,cn=Configuration"
ibm-slapdBulkloadErrors
The ldapexop command only updates those attributes that are dynamic. For other changes to take effect you must stop and restart the server. See Dynamically-changed attributes for a list of the attributes that can be updated dynamically.
Use the following procedures to view the bulkload error log.
To view the bulkload error log issue the following command:
more /var/ldap/bulkload.log
where var/ldap/bulkload.log is your bulkload error log.
To view and clear the bulkload error log dynamically:
ldapexop -D cn=root -w root -op readlog -log bulkload -lines all ldapexop -D cn=root -w root -op clearlog -log bulkload
Issue the command:
ldapmodify -D <AdminDN <-w >AdminPW> -i <filename>
where <filename> contains:
dn: cn=Admin, cn=Configuration changetype: modify replace: ibm-slapdErrorLog ibm-slapdErrorLog: <newpathname>
Use the following procedures to view the administration daemon error log.
To view the administration daemon error log issue the following command:
more /var/ldap/ibmdiradm.log
where var/ldap/ibmdiradm.log is your Web Administration error log.
To view and clear the Web Administration error log dynamically:
ldapexop -D cn=root -w root -op readlog -log ibmdiradm -lines all ldapexop -D cn=root -w root -op clearlog -log ibmdiradm
Expand the Directory management category in the navigation area of the Web Administration Tool. All the directory entry tasks that you want to perform can be accessed by selecting Manage entries. Two short cuts have been added to the navigation area for the specific tasks of adding an entry and finding (searching for) entries
You can perform the following operations with directory entries:
If you have not done so already, expand the Directory management category in the navigation area, then click Manage entries. You can expand the various subtrees and select the entry that you want to work on. You can choose the operation you want to perform from the right-side tool bar.
If you have not done so already, expand the Directory management category in the navigation area.
If you have not done so already, expand the Directory management category in the navigation area, then click Manage entries. You can expand the various subtrees and select the subtree, the suffix, or the entry that you want to work on. Click Delete from the right-side tool bar.
If you have not done so already, expand the Directory management category in the navigation area, then click Manage entries. You can expand the various subtrees and select the entry that you want to work on. Click Edit attributes from the right-side tool bar.
If an attribute requires binary data, a Binary data button is displayed next to the attribute field. If the attribute has no data the field is blank. Because binary attributes cannot be displayed, if an attribute contains binary data, the field displays Binary Data - 1. If the attribute contains multiple values, the field displays as a drop-down list.
Click the Binary data button to work with binary attributes.
You can import, export or delete binary data.
To add binary data to the attribute:
To export binary data:
To delete binary data:
This function is useful if you are creating similar entries. The copy inherits all the attributes of the original. You need to make some modifications to name the new entry.
If you have not done so already, expand the Directory management category in the navigation area, then click Manage entries. You can expand the various subtrees and select the entry, such as John Doe, that you want to work on. Click Copy from the right-side tool bar.
To view ACL properties using the Web Administration Tool utility and to work with ACLs, see Working with Access Control Lists.
See Access Control Lists for additional information.
Use the Add auxiliary class button on the toolbar to add an auxiliary object class to an existing entry in the directory tree. An auxiliary object class provides additional attributes to the entry to which it is added.
If you have not done so already, expand the Directory management category in the navigation area, then click Manage entries. You can expand the various subtrees and select the entry, such as John Doe, that you want to work on. Click Add auxiliary class from the right-side tool bar.
Although you can delete an auxiliary class during the add auxiliary class procedure, it is easier to use the delete auxiliary class function if you are going to delete a single auxiliary class from an entry. However, it might be more convenient to use the add auxiliary class procedure if you are going to delete multiple auxiliary classes from and entry.
Repeat these steps for each auxiliary class that you want to delete.
If you have not done so already, expand the Directory management category in the navigation area.
There are three options for searching the directory tree:
The search options are accessible by expanding the Directory management category in the navigation area, click Find entries. Select one of the following tabs:
Select on of the following types of searches:
A simple search uses a default search criteria:
To perform a simple search:
An advanced search enables you to specify search constraints and enable search filters. Use the Simple search to use default search criteria.
Use this method to create a search filter. For example to search on surnames enter sn=* in the field. If you are searching on multiple attributes, you must use search filter syntax. For example to search for the surnames of a particular department you enter:
(&(sn=*)(dept=<departmentname>))
At the Options tab:
See Setting Searches for additional information about searches.
Access Control Lists (ACL) provide a means to protect information stored in a LDAP directory. Administrators use ACLs to restrict access to different portions of the directory, or specific directory entries. LDAP directory entries are related to each other by a hierarchical tree structure. Each directory entry (or object) contains the distinguished name of the object as well as a set of attributes and their corresponding values.
The object attributes associated with access control, such as owner, ownerSource, ownerPropagate, aclEntry, aclSource and aclPropagate are unusual in that they are logically associated with each object, but can have values that depend upon other objects higher in the tree. Depending upon how they are established, these attribute values can be explicit to an object or inherited from an ancestor.
The access control model defines two sets of attributes: The Access Control Information (ACI) and the entryOwner Information. The ACI specifically defines a subject's permission to perform a given operation against certain LDAP objects. The entryOwner information controls which subjects can define the ACIs. The entryOwnership also acquires full access rights to the target object.
Using ACL, administrators can restrict access to different portions of the directory, specific directory entries and, based on the attribute name or attribute access class, the attributes contained in the entries. Each entry within the LDAP directory has a set of associated ACI. In conformance with the LDAP model, the ACI and entryOwner information is represented as attribute-value pairs. Furthermore, the LDIF syntax is used to administer these values. The attributes are:
In the current access control model, ACLs apply explicitly to the directory entry that contains them, but may be propagated to none, or all of its descendant entries. Filter-based ACLs differ in that they employ a filter-based comparison, using a specified object filter, to match target objects with the effective access that applies to them.
Although they perform the same function, the behavior of the two types of ACLs is significantly different. Filter-based ACLs do not propagate in the same way that non-filter-based ACLs currently do. By nature, they inherently propagate to any comparison matched objects in the associated subtree. For this reason, the aclPropagate attribute, which is used to stop propagation of non-filter ACLs, does not apply to the new filter-based ACLs.
The default behavior of filter-based ACLs to accumulate from the lowest containing entry, upward along the ancestor entry chain, to the highest containing entry in the DIT. The effective access is calculated as the union of the access rights granted, or denied, by the constituent ancestor entries. There is an exception to this behavior. For compatibility with the subtree replication feature, and to allow greater administrative control, a ceiling attribute is used as a means to stop accumulation at the entry in which it is contained.
A new set of access control attributes are used specifically for filter-based ACL support, rather than merging filter-based characteristics into the existing non-filter based ACLs. The attributes are:
The ibm-filterAclEntry attribute has the same format as aclEntry, with the addition of an object filter component. The associated ceiling attribute is ibm-filterAclInherit. By default it is set to true. When set to false, it terminates the accumulation.
Each of these attributes can be managed using LDIF notation. The syntax for the new filter-based ACL attributes are modified versions of the current non-filter-based ACL attributes.The following defines the syntax for the ACI and entryOwner attributes using baccus naur form (BNF).
<aclEntry> ::= <subject> [ ":" <rights> ] <aclPropagate> ::= "true" | "false"
<ibm-filterAclEntry> ::= <subject> ":" <object filter> [ ":" <rights> ] <ibm-filterAclInherit> ::= "true" | "false"
<entryOwner> ::= <subject>
<ownerPropagate> ::= "true" | "false"
<subject> ::= <subjectDnType> ':' <subjectDn> |
<pseudoDn>
<subjectDnType> ::= "role" | "group" | "access-id"
<subjectDn> ::= <DN>
<DN> ::= distinguished name as described in RFC 2251, section 4.1.3.
<pseudoDn> ::= "group:cn=anybody" | "group:cn=authenticated" |
"access-id:cn=this"
<object filter> ::= string search filter as defined in RFC 2254, section 4 (extensible matching is not supported).
<rights> ::= <accessList> [":" <rights> ]
<accessList> ::= <objectAccess> | <attributeAccess> |
<attributeClassAccess>
<objectAccess> ::= "object:" [<action> ":"] <objectPermissions>
<action> ::= "grant" | "deny"
<objectPermisssions> ::= <objectPermission> [ <objectPermissions> ]
<objectPermission> ::= "a" | "d" | ""
<attributeAccess> ::= "at." <attributeName> ":" [<action> ":"]
<attributePermissions>
<attributeName> ::= attributeType name as described in RFC 2251, section 4.1.4.
(OID or alpha-numeric string with leading
alphabet, "-" and ";" allowed)
<attributePermissions> ::= <attributePermission>
[<attributePermissions>]
<attributePermission> ::= "r" | "w" | "s" | "c" | ""
<attributeClassAccess> ::= <class> ":" [<action> ":"]
<attributePermissions>
<class> ::= "normal" | "sensitive" | "critical"
A subject (the entity requesting access to operate on an object) consists of the combination of a DN (Distinguished Name) type and a DN. The valid DN types are: access Id, Group and Role.
The DN identifies a particular access-id, role or group. For example, a subject might be access-id: cn=personA, o=IBM or group: cn=deptXYZ, o=IBM.
Because the field delimiter is the colon ( : ), a DN containing colons must be surrounded by double-quotation marks ( "" ). If a DN already contains characters with double-quotation marks, these characters must be escaped with a backslash (\).
All directory groups can be used in access control.
Another DN type used within the access control model is role. While roles and groups are similar in implementation, conceptually they are different. When a user is assigned to a role, there is an implicit expectation that the necessary authority has already been set up to perform the job associated with that role. With group membership, there is no built in assumption about what permissions are gained (or denied) by being a member of that group.
Roles are similar to groups in that they are represented in the directory by an object. Additionally, roles contain a group of DNs. Roles that are used in access control must have an objectclass of AccessRole.
The LDAP directory contains several pseudo DNs. These are used to refer to large numbers of DNs which at bind time share a common characteristic, in relation to either the operation being performed, or the target object on which the operation is being performed.
Currently, three pseudo DNs are defined:
This parameter applies to filtered ACLs only. The string search filter as defined in RFC 2254, is used as the object filter format. Because the target object is already known, the string is not used to perform an actual search. Instead, a filter-based compare on the target object in question is performed to determine if a given set of ibm-filterAclEntry values apply to it.
Access rights can apply to an entire object or to attributes of the object. The LDAP access rights are discrete. One right does not imply another right. The rights may be combined together to provide the desired rights list following a set of rules discussed later. Rights can be of an unspecified value, which indicates that no access rights are granted to the subject on the target object. The rights consist of three parts:
The possible attribute permissions are: read ( r ), write ( w ), search ( s ), and compare ( c ). Additionally, object permissions apply to the entry as a whole. These permissions are add child entries ( a ) and delete this entry ( d ).
The following table summarizes the permissions needed to perform each of
the LDAP operations.
| Operation | Permission Needed |
| ldapadd | add (on parent) |
| ldapdelete | delete (on object) |
| ldapmodify | write (on attributes being modified) |
| ldapsearch |
|
| ldapmodrdn | write (on RDN attributes) |
| ldapcompare | compare (on compared attribute) |
Attributes requiring similar permissions for access are grouped together in classes. Attributes are mapped to their attribute classes in the directory schema file. These classes are discrete; access to one class does not imply access to another class. Permissions are set with regard to the attribute access class as a whole. The permissions set on a particular attribute class apply to all attributes within that access class unless the individual attribute access permissions are specified.
IBM defines three attribute classes that are used in evaluation of access to user attributes: normal, sensitive, and critical. For example, attribute commonName falls into the normal class, and attribute userpassword belongs to the critical class. User defined attributes belong to the normal access class unless otherwise specified.
Two other access classes are also defined: system and restricted. The system class attributes are:
These are attributes maintained by the LDAP server and are read-only to the directory users. OwnerSource and aclSource are described in the Propagation section.
The restricted class of attributes that define the access control are:
All users have read access to the restricted attributes but only entryOwners can create, modify, and delete these attributes.
The entry owners have complete permissions to perform any operation on the object regardless of the aclEntry. Additionally, the entry owners are the only ones who are permitted to administer the aclEntries for that object. EntryOwner is an access control subject, it can be defined as individuals, groups or roles.
Entries on which an aclEntry has been placed are considered to have an explicit aclEntry. Similarly, if the entryOwner has been set on a particular entry, that entry has an explicit owner. The two are not intertwined, an entry with an explicit owner may or may not have an explicit aclEntry, and an entry with an explicit aclEntry might have an explicit owner. If either of these values is not explicitly present on an entry, the missing value is inherited from an ancestor node in the directory tree.
Each explicit aclEntry or entryOwner applies to the entry on which it is set. Additionally, the value might apply to all descendants that do not have an explicitly set value. These values are considered propagated; their values propagate through the directory tree. Propagation of a particular value continues until another propagating value is reached.
AclEntry and entryOwner can be set to apply to just a particular entry with the propagation value set to "false", or an entry and its subtree with the propagation value set to "true". Although both aclEntry and entryOwner can propagate, their propagation is not linked in anyway.
The aclEntry and entryOwner attributes allow multi-values, however, the propagation attributes (aclPropagate and ownerPropagate) can only have a single value for all aclEntry or entryOwner attribute values within the same entry.
The system attributes aclSource and ownerSource contain the DN of the effective node from which the aclEntry or entryOwner are evaluated, respectively. If no such node exists, the value default is assigned.
An object's effective access control definitions can be derived by the following logic:
Access for a particular operation is granted or denied based on the subject's bind DN for that operation on the target object. Processing stops as soon as access can be determined.
The checks for access are done by first finding the effective entryOwnership and ACI definition, checking for entry ownership, and then by evaluating the object's ACI values.
Filter-based ACLs accumulate from the lowest containing entry, upward along the ancestor entry chain, to the highest containing entry in the DIT. The effective access is calculated as the union of the access rights granted, or denied, by the constituent ancestor entries. The existing set of specificity and combinatory rules are used to evaluate effective access for filter based ACLs.
Filter-based and non-filter-based attributes are mutually exclusive within a single containing directory entry. Placing both types of attributes into the same entry is not allowed, and is a constraint violation. Operations associated with the creation of, or updates to, a directory entry fail if this condition is detected.
When calculating effective access, the first ACL type to be detected in the ancestor chain of the target object entry sets the mode of calculation. In filter-based mode, non-filter-based ACLs are ignored in effective access calculation. Likewise, in non-filter-based mode, filter-based ACLs are ignored in effective access calculation.
To limit the accumulation of filter-based ACLs in the calculation of effective access, an ibm-filterAclInherit attribute set to a value of "false" may be placed in any entry between the highest and lowest occurrence of ibm-filterAclEntry in a given subtree. This causes the subset of ibm-filterAclEntry attributes above it in the target object's ancestor chain to be ignored.
To exclude the accumulation of filter-based ACLs in the calculation of effective access, an ibm-filterAclInherit attribute set to a value of "false" may be placed in any entry below the lowest occurrence of ibm-filterAclEntry in a given subtree. This causes all ibm-filterAclEntry attributes above it in the target object's ancestor chain to be ignored. The resulting access resolves to the default filter ACL value.
By default, the directory administrator and the master server or the peer server (for replication) get full access rights to all objects in the directory except write access to system attributes. Other entryOwners get full access rights to the objects under their ownership except write access to system attributes. All users have read access rights to system and restricted attributes. These predefined rights cannot be altered. If the requesting subject has entryOwnership, access is determined by the above default settings and access processing stops.
If the requesting subject is not an entryOwner, then the ACI values for the object entries are checked. The access rights as defined in the ACIs for the target object are calculated by the specificity and combinatory rules.
In other words, within the object entry, if a defined ACI entry contains an access-id subject DN that matches the bind DN, then the permissions are first evaluated based on that aclEntry. Under the same subject DN, if matching attribute level permissions are defined, they supersede any permissions defined under the attribute classes. Under the same attribute or attribute class level definition, if conflicting permissions are present, denied permissions override granted permissions.
If access still can not be determined and all found matching aclEntries are defined under "cn=this", then group membership is evaluated. If a user belongs to more than one groups, the user receives the combined permissions from these groups. Additionally, the user automatically belongs to the cn=Anybody group and possibly the cn=Authenticated group if the user did an authenticated bind. If permissions are defined for those groups, the user receives the specified permissions.
For example, assume attribute1 is in the sensitive attribute class, and user cn=Person A, o=IBM belongs to both group1 and group2 with the following aclEntries defined:
This user gets:
For another example, with the following aclEntries:
The user has:
The following two examples show an administrative subdomain being established. The first example shows a single user being assigned as the entryOwner for the entire domain. The second example shows a group assigned as the entryOwner.
entryOwner: access-id:cn=Person A,o=IBM ownerPropagate: true entryOwner: group:cn=System Owners, o=IBM ownerPropagate: true
The next example shows how an access id "cn=Person 1, o=IBM" is being given permissions to read, search, and compare attribute1. The permission applies to any node in the entire subtree, at or below the node containing this ACI, that matches the "(objectclass=groupOfNames)" comparison filter. The accumulation of matching ibm-filteraclentry attributes in any ancestor nodes has been terminated at this entry by setting the ibm-filterAclInherit attribute to "false".
ibm-filterAclEntry: access-id:cn=Person 1,o=IBM:(objectclass=groupOfNames):
at.attribute1:grant:rsc
ibm-filterAclInherit: false
The next example shows how a group "cn=Dept XYZ, o=IBM" is being given permissions to read, search and compare attribute1. The permission applies to the entire subtree below the node containing this ACI.
aclEntry: group:cn=Dept XYZ,o=IBM:at.attribute1:grant:rsc aclPropagate: true
The next example shows how a role "cn=System Admins,o=IBM" is being given permissions to add objects below this node, and read, search and compare attribute2 and the critical attribute class. The permission applies only to the node containing this ACI.
aclEntry: role:cn=System Admins,o=IBM:object:grant:a:at.
attribute2:grant:rsc:critical:grant:rsc
aclPropagate: false
Given the following ACIs for an entry:
aclEntry: group:cn=Dept ABC,o=IBM:normal:grant:rsc aclPropagate: true
perform the following change:
dn: cn=some entry changetype: modify replace: aclEntry aclEntry: group:cn=Dept XYZ,o=IBM:normal:grant:rsc
The resulting ACI is:
aclEntry: group:cn=Dept XYZ,o=IBM:normal:grant:rsc aclPropagate: true
ACI values for Dept ABC are lost through the replace.
Given the following ACIs for an entry:
ibm-filterAclEntry: group:cn=Dept ABC,o=IBM:(cn=Manager ABC):normal
:grant:rsc
ibm-filterAclInherit: true
perform the following changes:
dn: cn=some entry
changetype: modify
replace: ibm-filterAclEntry
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:grant:rsc
dn: cn=some entry
changetype: modify
replace: ibm-filterAclInherit
ibm-filterAclInherit: false
The resulting ACI is:
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:grant:rsc
ibm-filterAclInherit: false
ACI values for Dept ABC are lost through the replace.
aclEntry: group:cn=Dept XYZ,o=IBM:normal:grant:rsc
with a modification:
dn: cn=some entry changetype: modify add: aclEntry aclEntry: group:cn=Dept ABC,o=IBM:at.attribute1:grant:rsc
would yield an multi-valued aclEntry of:
aclEntry: group:cn=Dept XYZ,o=IBM:normal:grant:rsc aclEntry: group:cn=Dept ABC,o=IBM:at.attribute1:grant:rsc
For example, given the ACI:
Ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:grant:rsc
with a modification:
dn: cn=some entry
changetype: modify
add: ibm-filterAclEntry
ibm-filterAclEntry: group:cn=Dept ABC,o=IBM:(cn=Manager ABC)
:at.attribute1:grant:rsc
would yield an multi-valued aclEntry of:
Ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:grant:rsc
ibm-filterAclEntry: group:cn=Dept ABC,o=IBM:(cn=Manager ABC):at.attribute1
:grant:rsc
The permissions under the same attribute or attribute class are considered as the basic building blocks and the actions are considered as the qualifiers. If the same permission value is being added more than once, only one value is stored. If the same permission value is being added more than once with different action values, the last action value is used. If the resulting permission field is empty (""), this permission value is set to null and the action value is set to grant.
For example, given the following ACI:
aclEntry: group:cn=Dept XYZ,O=IBM:normal:grant:rsc
with a modification:
dn: cn=some entry
changetype: modify
add: aclEntry
aclEntry: group:cn=Dept XYZ,o=IBM:normal:deny:r:critical:deny::sensitive
:grant:r
yields an aclEntry of:
aclEntry: group:cn=Dept XYZ,O=IBM:normal:grant:sc:normal:deny:r:critical
:grant::sensitive:grant:r
For example, given the following ACI:
Ibm-filterAclEntry: group:cn=Dept XYZ,O=IBM:(cn=Manager XYZ):normal
:grant:rsc
with a modification:
dn: cn=some entry
changetype: modify
add: ibm-filterAclEntry
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:deny:r:critical:deny::sensitive:grant:r
yields an aclEntry of:
ibm-filterAclEntry: group:cn=Dept XYZ,O=IBM:(cn=Manager XYZ):normal
:grant:sc:normal:deny:r:critical:grant::sensitive
:grant:r
Given an ACI of:
aclEntry: group:cn=Dept XYZ,o=IBM:object:grant:ad aclEntry: group:cn=Dept XYZ,o=IBM:normal:grant:rwsc dn: cn = some entry changetype: modify delete: aclEntry aclEntry: group:cn=Dept XYZ,o=IBM:object:grant:ad
yields a remaining ACI on the server of :
aclEntry: group:cn=Dept XYZ,o=IBM:normal:grant:rwsc
Given an ACI of:
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):object
:grant:ad
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:grant:rwsc
dn: cn = some entry
changetype: modify
delete: ibm-filterAclEntry
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):object
:grant:ad
yields a remaining ACI on the server of:
ibm-filterAclEntry: group:cn=Dept XYZ,o=IBM:(cn=Manager XYZ):normal
:grant:rwsc
Deleting an ACI or entryOwner value that does not exist results in an unchanged ACI or entryOwner and a return code specifying that the attribute value does not exist.
With the ldapmodify-delete operation, the entryOwner can be deleted by specifying
dn: cn = some entry changetype: modify delete: entryOwner
In this case, the entry would then have no explicit entryOwner. The ownerPropagate is also removed automatically. This entry would inherit its entryOwner from the ancestor node in the directory tree following the propagation rule.
The same can be done to delete aclEntry completely:
dn: cn = some entry changetype: modify delete: aclEntry
Deleting the last ACI or entryOwner value from an entry is not the same as deleting the ACI or entryOwner. It is possible for an entry to contain an ACI or entryOwner with no values. In this case, nothing is returned to the client when querying the ACI or entryOwner and the setting propagates to the descendent nodes until it is overridden. To prevent dangling entries that nobody can access, the directory administrator always has full access to an entry even if the entry has a null ACI or entryOwner value.
The effective ACI or entryOwner values can be retrieved by simply specifying the desired ACL or entryOwner attributes in a search, for example,
ldapsearch -b "cn=object A, o=ibm" -s base "objectclass=*"
aclentry aclpropagate aclsource entryowner ownerpropagate ownersource
ibm-filterAclEntry ibm-filterAclInherit ibm-effectiveAcl
returns all ACL or entryOwner information that is used in access evaluation on object A. Note that the returned values might not look exactly the same as they are first defined. The values are the equivalent of the original form.
Searching on the ibm-filterAclEntry attribute alone only returns the values specific to the containing entry.
A read-only operational attribute, ibm-effectiveAcl, is used to show the accumulated effective access. A search request for ibm-effectiveAcl returns the effective access that applies to the target object based on: non-filter ACLs, or filter ACLs, depending on how they have been distributed in the DIT.
Because filter-based ACLs might come from several ancestor sources, a search on the aclSource attribute produces a list of the associated sources.
To view ACL properties using the Web Administration Tool utility and to work with ACLs.
This panel has five tabs:
The Effective ACLs and Effective owners tabs contain read-only information about the ACLs.
Effective ACLs are the explicit and inherited ACLs of the selected entry. You can view the access rights for a specific effective ACL by selecting it and clicking the View button. The View access rights panel opens.
Click OK to return to the Effective ACLs tab.
Click Cancel to return to the Edit ACL panel.
Effective owners are the explicit and inherited owners of the selected entry.
You can add new non-filtered ACLs to an entry, or edit existing non-filtered ACLs.
Non-filtered ACLs can be propagated. This means that access control information defined for one entry can be applied to all of its subordinate entries. The ACL source is the source of current ACL for the selected entry. If the entry does not have an ACL, it inherits an ACL from parent objects based on the ACL settings of the parent objects.
Enter the following information on the Non-filtered ACLs tab:
Click the either the Add button to add the DN in the DN (Distinguished Name) field to the ACL list or the Edit button to modify the ACLs of an existing DN.
The Add access rights and Edit access rights panels allow you to set the access rights for a new or existing Access Control List (ACLs). The Type field defaults to the type you selected on the Edit ACL panel. If you are adding an ACL, all other fields default to blank. If you are editing an ACL, the fields contain the values set last time the ACL was modified.
You can:
To set access rights:
Each security class has permissions associated with it.
Additionally, you may specify permissions based on the attribute instead of the security class to which the attribute belongs. The attribute section is listed below the Critical security class.
You can remove ACLs in either of two ways:
You can add new filtered ACLs to an entry, or edit existing filtered ACLs.
Filter-based ACLs employ a filter-based comparison, using a specified object filter, to match target objects with the effective access that applies to them.
The default behavior of filter-based ACLs to accumulate from the lowest containing entry, upward along the ancestor entry chain, to the highest containing entry in the DIT. The effective access is calculated as the union of the access rights granted, or denied, by the constituent ancestor entries. There is an exception to this behavior. For compatibility with the subtree replication feature, and to allow greater administrative control, a ceiling attribute is used as a means to stop accumulation at the entry in which it is contained.
Enter the following information on the Filtered ACLs tab:
Click the either the Add button to add the DN in the DN (Distinguished Name) field to the ACL list or the Edit button to modify the ACLs of an existing DN.
The Add access rights and Edit access rights panels allow you to set the access rights for a new or existing Access Control List (ACLs). The Type field defaults to the type you selected on the Edit ACL panel. If you are adding an ACL, all other fields default to blank. If you are editing an ACL, the fields contain the values set last time the ACL was modified.
You can:
To set access rights:
Each security class has permissions associated with it.
Additionally, you may specify permissions based on the attribute instead of the security class to which the attribute belongs. The attribute section is listed below the Critical security class.
You can remove ACLs in either of two ways:
Entry owners have complete permissions to perform any operation on an object. Entry owners can be explicit or propagated (inherited).
Enter the following information on the Owners tab:
Click Add to add the DN in the DN (Distinguished Name) field to the list.
You can remove an owner in either of two ways:
For filter-based access to be included in subtree replication, any ibm-filterAclEntry attributes must reside at, or below, the associated ibm-replicationContext entry.
Because effective access cannot be accumulated from an ancestor entry above a replicated subtree, the ibm-filterAclInherit attribute must be set to a value of false, and reside at the associated ibm-replicationContext entry.
A group is a list, a collection of names. A groups can be used in aclentry, ibm-fliterAclEntry, and entryowner attributes to control access or in application-specific uses such as a mailing list; see Access Control Lists. Groups can be defined as either static, dynamic, or nested.
A static group defines each member individually using the structural objectclass groupOfNames, groupOfUniqueNames, accessGroup, or accessRole; or the auxiliary objectclass ibm-staticgroup. These objectclasses require the attribute member (or uniqueMember in the case of groupOfUniqueNames). A static group using these structural objectclasses must have at least one member; it cannot be empty. A static group may also be defined using the auxiliary objectclass: ibm-staticGroup, which does not require the member attribute, and therefore may be empty.
A typical group entry is:
DN: cn=Dev.Staff,ou=Austin,c=US objectclass: accessGroup cn: Dev.Staff member: cn=John Doe,o=IBM,c=US member: cn=Jane Smith,o=IBM,c=US member: cn=James Smith,o=IBM,c=US
Each group object contains a multivalued attribute consisting of member DNs.
Upon deletion of an access group, the access group is also deleted from all ACLs to which it has been applied.
A dynamic group defines its members differently than a static group. Instead of listing them individually, the dynamic group defines its members using an LDAP search. The dynamic group uses the structural objectclass groupOfURLs (or auxiliary objectclass ibm-dynamicGroup) and the attribute, memberURL to define the search using a simplified LDAP URL syntax.
ldap:///<base DN of search> ? ? <scope of search> ? <searchfilter>
The search for dynamic members is always internal to the server, so unlike a full ldap URL, a host name and port number is never specified, and the protocol is always ldap (never ldaps). The memberURL attribute may contain any kind of URL, but the server only uses memberURLs beginning with ldap:/// to determine dynamic membership.
A single entry in which the scope defaults to base and the filter defaults to objectclass=*:
ldap:///cn=John Doe, cn=Employees, o=Acme, c=US
All entries that are 1-level below cn=Employees, and the filter defaults to objectclass=*:
ldap:///cn=Employees, o=Acme, c=US??one
All entries that are under o-Acme with the objectclass=person:
ldap:///o=Acme, c=US??sub?objectclass=person
Depending on the object classes you use to define user entries, those entries might not contain attributes which are appropriate for determining group membership. You can use the auxiliary object class, ibm-dynamicMember, to extend your user entries to include the ibm-group attribute. This attribute allows you to add arbitrary values to your user entries to serve as targets for the filters of your dynamic groups. For example:
The members of this dynamic group are entries directly under the cn=users,ou=Austin entry that have an ibm-group attribute of GROUP1:
dn: cn=GROUP1,ou=Austin objectclass: groupOfURLs cn: GROUP1 memberURL: ldap:///cn=users,ou=Austin??one?(ibm-group=GROUP1)
Here is an example member of cn=GROUP1,ou=Austin:
dn: cn=Group 1 member, cn=users, ou=austin objectclass: person objectclass: ibm-dynamicMember sn: member userpassword: memberpassword ibm-group: GROUP1
The nesting of groups enables the creation of hierarchical relationships that can be used to define inherited group membership. A nested group is defined as a child group entry whose DN is referenced by an attribute contained within a parent group entry. A parent group is created by extending one of the structural group object classes (groupOfNames, groupOfUniqueNames, accessGroup, accessRole, or groupOfURLs) with the addition of the ibm-nestedGroup auxiliary object class. After nested group extension, zero or more ibm-memberGroup attributes may be added, with their values set to the DNs of nested child groups. For example:
dn: cn=Group 2, cn=Groups, o=IBM, c=US objectclass: groupOfNames objectclass: ibm-nestedGroup objectclass: top cn: Group 2 description: Group composed of static, and nested members. member: cn=Person 2.1, cn=Dept 2, cn=Employees, o=IBM, c=US member: cn=Person 2.2, cn=Dept 2, cn=Employees, o=IBM, c=US ibm-memberGroup: cn=Group 8, cn=Nested Static, cn=Groups, o=IBM, c=US
The introduction of cycles into the nested group hierarchy is not allowed. If it is determined that a nested group operation results in a cyclical reference, either directly or through inheritance, it is considered a constraint violation and therefore, the update to the entry fails.
Any of the structural group object classes mentioned can be extended such that group membership is described by a combination of static, dynamic, and nested member types. For example:
dn: cn=Group 10, cn=Groups, o=IBM, c=US objectclass: groupOfURLs objectclass: ibm-nestedGroup objectclass: ibm-staticGroup objectclass: top cn: Group 10 description: Group composed of static, dynamic, and nested members. memberURL: ldap:///cn=Austin, cn=Employees, o=IBM, c=US??one?objectClass=person ibm-memberGroup: cn=Group 9, cn=Nested Dynamic, cn=Groups, o=IBM, c=US member: cn=Person 10.1, cn=Dept 2, cn=Employees, o=IBM, c=US member: cn=Person 10.2, cn=Dept 2, cn=Employees, o=IBM, c=US
Two operational attributes can be used to query aggregate group membership. For a given group entry, the ibm-allMembers operational attribute enumerates the aggregate set of group membership, including static, dynamic, and nested members, as described by the nested group hierarchy. For a given user entry, the ibm-allGroups operational attribute enumerates the aggregate set of groups, including ancestor groups, to which that user has membership.
A requester may only receive a subset of the total data requested, depending on how the ACLs have been set on the data. Anyone can request the ibm-allMembers and ibm-allGroups operational attributes, but the data set returned only contains data for the LDAP entries and attributes that the requester has access rights to. The user requesting the ibm-allMembers or ibm-allGroups attribute must have access to the member or uniquemember attribute values for the group and nested groups in order to see static members, and must be able to perform the searches specified in the memberURL attribute values in order to see dynamic members. For examples:
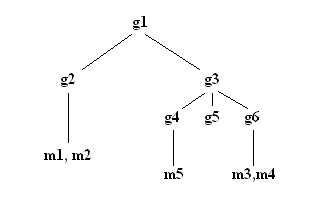
For this example, m1 and m2 are in the member attribute of g2. The ACL for g2 allows user1 to read the member attribute, but user 2 does not have access to the member attribute. The entry LDIF for the g2 entry is as follows:
dn: cn=g2,cn=groups,o=ibm,c=us objectclass: accessGroup cn: g2 member: cn=m1,cn=users,o=ibm,c=us member: cn=m2,cn=users,o=ibm,c=us aclentry: access-id:cn=user1,cn=users,o=ibm,c=us:normal:rsc aclentry: access-id:cn=user2,cn=users,o=ibm,c=us:normal:rsc:at.member:deny:rsc
The g4 entry uses the default aclentry, which allows both user1 and user2 to read its member attribute. The LDIF for the g4 entry is as follows:
dn: cn=g4, cn=groups,o=ibm,c=us objectclass: accessGroup cn: g4 member: cn=m5, cn=users,o=ibm,c=us
The g5 entry is a dynamic group, which gets its two members from the memberURL attribute. The LDIF for the g5 entry is as follows:
dn: cn=g5, cn=groups,o=ibm,c=us objectclass: container objectclass: ibm-dynamicGroup cn: g5 memberURL: ldap:///cn=users,o=ibm,c=us??sub?(|(cn=m3)(cn=m4))
The entries m3 and m4 are members of group g5 because they match the memberURL The ACL for the m3 entry allows both user1 and user2 to search for it. The ACL for the m4 entries doesn't allow user2 to search for it. The LDIF for m4 is as follows:
dn: cn=m4, cn=users,o=ibm,c=us objectclass:person cn: m4 sn: four aclentry: access-id:cn=user1,cn=users,o=ibm,c=us:normal:rsc aclentry: access-id:cn=user2,cn=users,o=ibm,c=us
ldapsearch -D cn=user1,cn=users,o=ibm,c=us -w user1pwd -s base -b cn=g1,
cn=groups,o=ibm,c=us objectclass=* ibm-allmembers
cn=g1,cn=groups,o=ibm,c=us
ibm-allmembers: CN=M1,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M2,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M3,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M4,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M5,CN=USERS,O=IBM,C=US
ldapsearch -D cn=user2,cn=users,o=ibm,c=us -w user2pwd -s base -b cn=g1,
cn=groups,o=ibm,c=us objectclass=* ibm-allmembers
cn=g1,cn=groups,o=ibm,c=us
ibm-allmembers: CN=M3,CN=USERS,O=IBM,C=US
ibm-allmembers: CN=M5,CN=USERS,O=IBM,C=US
ldapsearch -D cn=user2,cn=users,o=ibm,c=us -w user2pwd -s base -b cn=m3,
cn=users,o=ibm,c=us objectclass=* ibm-allgroups
cn=m3,cn=users,o=ibm,c=us
ibm-allgroups: CN=G1,CN=GROUPS,O=IBM,C=US
ldapsearch -D cn=user2,cn=users,o=ibm,c=us -w user2pwd -s base -b
cn=m1,cn=users,o=ibm,c=us objectclass=* ibm-allgroups
cn=m1,cn=users,o=ibm,c=us
Role-based authorization is a conceptual complement to the group-based authorization, and is useful in some cases. As a member of a role, you have the authority to do what is needed for the role in order to accomplish a job. Unlike a group, a role comes with an implicit set of permissions. There is not a built-in assumption about what permissions are gained (or lost) by being a member of a group.
Roles are similar to groups in that they are represented in the directory by an object. Additionally, roles contain a group of DNs. Roles which are to be used in access control must have an objectclass of 'AccessRole'. The 'Accessrole' objectclass is a subclass of the 'GroupOfNames' objectclass.
For example, if there are a collection of DNs such as 'sys admin', your first reaction may be to think of them as the 'sys admin group' (since groups and users are the most familiar types of privilege attributes). However, since there are a set of permissions that you would expect to receive as a member of 'sys admin' the collection of DNs may be more accurately defined as the 'sys admin role'.
A realm is a collection of users and the groups to which they belong. For example a company, a bowling team, or a club could all be realms.
Realms are defined by creating entries of object class "ibm-realm" anywhere in a user naming context (not under cn=localhost, cn=schema or cn=configuration). The ibm-realm object defines the realm's name (cn), a group of realm administrators (ibm-realmAdminGroup), a user-template object (ibm-realmUserTemplate) specifying the object classes and attributes for users in the realm, and the location of container entries under which user and group entries are stored (ibm-realmUserContainer and ibm-realmGroupContainer). The directory administrator is responsible for managing user-templates, realms and realm administrator groups. After a realm is created, members of that realm's administrator group (realm administrators) are responsible for managing the users and groups within that realm.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
To create a realm administrator, you must first create an administration group for the realm.
Expand the Directory management category in the navigation area of the Web Administration Tool.
If you do not already have a user entry for the administrator, you must create one.
Expand the Directory management category in the navigation area of the Web Administration Tool.
Expand the Directory management category in the navigation area of the Web Administration Tool.
You have created an administrator that can manage entries within the realm.
After you have created a realm, your next step is to create a user template. A template helps you to organize the information you want to enter. Expand the Realms and templates category in the navigation area of the Web Administration Tool.
After you have created a realm and a template, you need to add the template to the realm. Expand the Realms and templates category in the navigation area of the Web Administration Tool.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
See Groups for additional information.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
After you have set up and populated your initial realm, you can add more realms or modify existing realms.
Expand the Realms and templates category in the navigation area and click Manage realms. A list of existing realms is displayed. From this panel you can add a realm, edit a realm, remove a realm or edit the access control list (acls) of the realm.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
To view ACL properties using the Web Administration Tool utility and to work with ACLs, see Working with Access Control Lists.
See Access Control Lists for additional information.
After you have created your initial template, you can add more templates or modify existing templates.
Expand the Realms and templates category in the navigation area and click Manage user templates. A list of existing templates is displayed. From this panel you can add a template, edit a template, remove a template or edit the access control list (ACLs) of the template.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
Expand the Realms and templates category in the navigation area of the Web Administration Tool.
Expand the Realms and template category in the navigation area of the Web Administration Tool.
To view ACL properties using the Web Administration Tool utility and to work with ACLs, see Working with Access Control Lists.
See Access Control Lists for additional information.
After you have set up your realms and templates, you can populate them with users.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
If you need to create a number of users that have mostly identical information, you can create the additional users by copying the initial user and modifying the information.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
After you have set up your realms and templates, you can create groups.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
See Groups for additional information.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
If you need to create a number of groups that have mostly the same members, you can create the additional groups by copying the initial group and modifying the information.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
Expand the Users and groups category in the navigation area of the Web Administration Tool.
Use these utilities as an alternative method of administering your IBM Directory Server.
This section describes the utilities that can be run from a command prompt.
The client utilities all use the ldap_sasl_bind API. When bind is invoked, several results can be returned. Following are bind results using various combinations of user IDs and passwords.
This section provides a description of the client utilities. They are also documented in "Chapter 2. Ldap Utilities" in the IBM Directory Server Version 5.1: Client SDK Programming Reference.
The LDAP modify-entry and LDAP add-entry tools
ldapmodify [-a] [-b] [-c] [-C charset] [-d debuglevel][-D binddn][-i file] [-h ldaphost] [-k] [-K keyfile] [-m mechanism] [-M] [-N certificatename] [-O maxhops] [-p ldapport] [-P keyfilepw] [-r] [-R] [-v] [-V] [-w passwd | ?] [-Z] ldapadd [-a] [-b] [-c] [-C charset] [-d debuglevel][-D binddn][-i file] [-h ldaphost] [-k] [-K keyfile] [-m mechanism] [-M] [-N certificatename] [-O maxhops] [-p ldapport] [-P keyfilepw] [-r] [-R] [-v] [-V] [-w passwd | ?] [-Z]
ldapmodify is a command-line interface to the ldap_modify and ldap_add library calls. ldapadd is implemented as a renamed version of ldapmodify. When invoked as ldapadd, the -a (add new entry) flag is turned on automatically.
ldapmodify opens a connection to an LDAP server, and binds to the server. You can use ldapmodify to modify or add entries. The entry information is read from standard input or from file through the use of the -i option.
To display syntax help for ldapmodify or ldapadd, type
ldapmodify -?
or
ldapadd -?
A default keyring file that is, ldapkey.kdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See the IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -Z switch.
The contents of file (or standard input if no -i flag is given on the command line) should conform to the LDIF format.
An alternative input format is supported for compatibility with older versions of ldapmodify. This format consists of one or more entries separated by blank lines, where each entry looks like the following:
Distinguished Name (DN) attr=value [attr=value ...]
where attr is the name of the attribute and value is the value.
By default, values are added. If the -r command line flag is given, the default is to replace existing values with the new one. It is permissible for a given attribute to appear more than once, for example, to add more than one value for an attribute. Also note that you can use a trailing `\\' to continue values across lines and preserve new lines in the value itself.
attr should be preceded by a - to remove a value. The = and value should be omitted to remove an entire attribute.
attr should be preceded by a + to add a value in the presence of the -r flag.
Assuming that the file /tmp/entrymods exists and has the following contents:
dn: cn=Modify Me, o=University of Higher Learning, c=US
changetype: modify
replace: mail
mail: modme@student.of.life.edu
-
add: title
title: Grand Poobah
-
add: jpegPhoto
jpegPhoto: /tmp/modme.jpeg
-
delete: description
-
the command:
ldapmodify -b -r -i /tmp/entrymods
will replace the contents of the Modify Me entry's mail attribute with the value modme@student.of.life.edu, add a title of Grand Poobah, and the contents of the file /tmp/modme.jpeg as a jpegPhoto, and completely remove the description attribute. These same modifications can be performed using the older ldapmodify input format:
cn=Modify Me, o=University of Higher Learning, c=US
mail=modme@student.of.life.edu
+title=Grand Poobah
+jpegPhoto=/tmp/modme.jpeg
-description
and the command:
ldapmodify -b -r -i /tmp/entrymods
Assuming that the file /tmp/newentry exists and has the following contents:
dn: cn=John Doe, o=University of Higher Learning, c=US
objectClass: person
cn: John Doe
cn: Johnny
sn: Doe
title: the world's most famous mythical person
mail: johndoe@student.of.life.edu
uid: jdoe
the command:
ldapadd -i /tmp/entrymods
adds a new entry for John Doe, using the values from the file /tmp/newentry.
Assuming that the file /tmp/newentry exists and has the contents:
dn: cn=John Doe, o=University of Higher Learning, c=US
changetype: delete
the command:
ldapmodify -i /tmp/entrymods
removes John Doe's entry.
If entry information is not supplied from file through the use of the -i option, the ldapmodify command will wait to read entries from standard input. To break out of the wait, use Ctrl+C or Ctrl+D.
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The content of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as 'trusted', you can establish a trust relationship with LDAP servers that use 'trusted' certificates issued by one of the trusted CAs. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s. For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
ldapchangepwd, ldapdelete, ldapexop, ldapmodrdn, ldapsearch
The LDAP modify password tool.
ldapchangepwd -D binddn -w passwd | ? -n newpassword | ?
[-C charset] [-d debuglevel][-h ldaphost] [-K keyfile]
[-m mechanism] [-M] [-N certificatename] [-O maxhops]
[-p ldapport] [-P keyfilepw] [-R] [-v] [-V version]
[-Z] [-?]
Sends modify password requests to an LDAP server.
A default keyring file that is, ldapkey.kdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -Z switch.
The following command,
ldapchangepwd -D cn=John Doe -w a1b2c3d4 -n wxyz9876
changes the password for the entry named with commonName "John Doe" from a1b2c3d4 to wxyz9876
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The content of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as 'trusted', you can establish a trust relationship with LDAP servers that use 'trusted' certificates issued by one of the trusted CAs. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s. For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
ldapadd, ldapdelete, ldapexop, ldapmodify, ldapmodrdn, ldapsearch
The LDAP delete-entry tool
ldapdelete [-c] [-C charset] [-d debuglevel][-D binddn][-i file]
[-h ldaphost] [-k] [-K keyfile] [-m mechanism] [-M] [-n] [-N certificatename]
[-O maxops] [-p ldapport] [-P keyfilepw] [-R] [-s][-v] [-V version]
[-w passwd | ?] [-Z] [dn]...
ldapdelete is a command-line interface to the ldap_delete library call.
ldapdelete opens a connection to an LDAP server, binds, and deletes one or more entries. If one or more Distinguished Name (DN) arguments are provided, entries with those DNs are deleted. Each DN is a string-represented DN. If no DN arguments are provided, a list of DNs is read from standard input, or from file if the -i flag is used.
To display syntax help for ldapdelete, type:
ldapdelete -?
.
A default keyring file that is, ldapkey.kdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -Z switch.
The following command,
ldapdelete "cn=Delete Me, o=University of Life, c=US"
attempts to delete the entry named with commonName "Delete Me" directly below the University of Life organizational entry. It might be necessary to supply a binddn and passwd for deletion to be allowed (see the -D and -w options).
If no DN arguments are provided, the ldapdelete command waits to read a list of DNs from standard input. To break out of the wait, use Ctrl+C or Ctrl+D.
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The content of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as 'trusted', you can establish a trust relationship with LDAP servers that use 'trusted' certificates issued by one of the trusted CAs. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s. For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
ldapadd, ldapchangepwd, ldapexop, ldapmodify, ldapmodrdn, ldapsearch
The LDAP extended operation tool
ldapexop [-C charset] [-d debuglevel][-D binddn][-e] [-h ldaphost]
[-help][-K keyfile] [-m mechanism] [-N certificatename]
[-p ldapport] [-P keyfilepw] [-?] [-v] [-w passwd | ?] [-Z]
-op {cascrepl | clearlog | controlqueue | controlrepl | getlogsize |
quiesce | readconfig | readlog}
The ldapexop utility is a command-line interface that provides the capability to bind to a directory and issue a single extended operation along with any data that makes up the extended operation value.
The ldapexop utility supports the standard host, port, SSL, and authentication options used by all of the LDAP client utilities. In addition, a set of options is defined to specify the operation to be performed, and the arguments for each extended operation
To display syntax help for ldapexop, type:
ldapexop -?
or
ldapexop -help
The options for the ldapexop command are divided into two categories:
These options specify the methods of connecting to the server and must be specified before the -op option.
A default keyring file that is, ldapkey.kdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -Z switch.
The -op extended-op option identifies the extended operation to be performed. The extended operation can be one of the following values:
ldapexop -op cascrepl -action -quiesce -rc "o=acme,c=us" -timeout 60
ldapexop -op clearlog -log audit
ldapexop -op controlqueue -skip all -ra "cn=server3,
ibm-replicaSubentry=master1-id,ibm-replicaGroup=default,
o=acme,c=us"
ldapexop -op controlqueue -skip 2185 -ra "cn=server3,
ibm-replicaSubentry=master1-id,ibm-replicaGroup=default,
o=acme,c=us"
ldapexop -op controlrepl -action suspend -ra "cn=server3,
ibm-replicaSubentry=master1-id,ibm-replicaGroup=default,
o=acme,c=us"
ldapexop -op getlogsize -log slapd 2000 lines
ldapexop -op quiesce -rc "o=acme,c=us" ldapexop -op quiesce -end -rc "o=ibm,c=us"
ldapexop -op readconfig -scope entire ldapexop -op readconfig -scope single "cn=configuration" ibm-slapdAdminPW
ldapexop -op readlog -log audit -lines 10 20 ldapexop -op readlog -log slapd -lines all
If no DN arguments are provided, the ldapdexop command waits to read a list of DNs from standard input. To break out of the wait, use Ctrl+C or Ctrl+D.
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The content of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as 'trusted', you can establish a trust relationship with LDAP servers that use 'trusted' certificates issued by one of the trusted CAs. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s. For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
ldapadd, ldapchangepwd, ldapdelete, ldapmodify, ldapmodrdn, ldapsearch
The LDAP modify-entry RDN tool
ldapmodrdn [-c] [-C charset] [-d debuglevel][-D binddn] [-h ldaphost] [-i file] [-k] [-K keyfile] [-m mechanism] [-M] [-n] [-N certificatename] [-O hopcount] [-p ldapport] [-P keyfilepw] [-r] [-R] [-v] [-V] [-w passwd | ?] [-Z] [dn newrdn | [-i file]]
ldapmodrdn is a command-line interface to the ldap_modrdn library call.
ldapmodrdn opens a connection to an LDAP server, binds, and modifies the RDN of entries. The entry information is read from standard input, from file through the use of the - f option, or from the command-line pair dn and rdn.
See LDAP Distinguished Names for information about RDNs (Relative Distinguished Names) and DNs (Distinguished Names).
To display syntax help for ldapmodrdn, type:
ldapmodrdn -?
A default keyring file (that is, ldapkey.kdb) and the associated password stash file (that is, ldapkey.sth) are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -Z switch.
If the command-line arguments dn and newrdn are given, newrdn replaces the RDN of the entry specified by the DN, dn. Otherwise, the contents of file (or standard input if no - i flag is given) consist of one or more entries:
Distinguished Name (DN) Relative Distinguished Name (RDN)
One or more blank lines may be used to separate each DN and RDN pair.
Assuming that the file /tmp/entrymods exists and has the contents:
cn=Modify Me, o=University of Life, c=US cn=The New Me
the command:
ldapmodrdn -r -i /tmp/entrymods
changes the RDN of the Modify Me entry from Modify Me to The New Me and the old cn, Modify Me is removed.
If entry information is not supplied from file through the use of the -i option (or from the command-line pair dn and rdn), the ldapmodrdn command waits to read entries from standard input. To break out of the wait, use Ctrl+C or Ctrl+D.
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The content of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as 'trusted', you can establish a trust relationship with LDAP servers that use certificates issued by one of the trusted CAs. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted, including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s. For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
ldapadd, ldapchangepwd, ldapdelete, ldapexop, ldapmodify, ldapsearch
The LDAP search tool and sample program
ldapsearch [-a deref] [-A] [-b searchbase] [-B] [-C charset] [-d debuglevel] [-D binddn] [-F sep] [-h ldaphost] [-i file] [-K keyfile] [-l timelimit] [-L] [-m mechanism] [-M] [-n] [-N certificatename][-o attr_type] [-O maxhops] [-p ldapport] [-P keyfilepw] [-q pagesize] [-R] [-s scope ] [-t] [-T seconds] [-v] [-V version] [-w passwd | ?] [-z sizelimit] [-Z] filter [-9 p] [-9 s] [attrs...]
ldapsearch is a command-line interface to the ldap_search library call.
ldapsearch opens a connection to an LDAP server, binds, and performs a search using the filter. The filter should conform to the string representation for LDAP filters (see ldap_search in the IBM Directory Server Version 5.1 C-Client SDK Programming Reference for more information on filters).
If ldapsearch finds one or more entries, the attributes specified by attrs are retrieved and the entries and values are printed to standard output. If no attrs are listed, all attributes are returned.
To display syntax help for ldapsearch, type ldapsearch -?.
A default keyring file (that is, ldapkey.kdb) and the associated password stash file (that is, ldapkey.sth) are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See the "Default Keyring and Password" section of the LDAP_SSL API in the IBM C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes below and LDAP SSL APIs for more information about SSL and certificates.
This parameter effectively enables the -Z switch.
-o sn -o -givenname
Thus, the syntax of the sort parameter is as follows:
[-]<attribute name>[:<matching rule OID>]
where
The default ldapsearch operation is not to sort the returned results.
-q 25 -T 15
If the -v (verbose) parameter is specified, ldapsearch lists how many entries have been returned so far, after each page of entries returned from the server, for example, 30 total entries have been returned.
Multiple -q parameters are enabled such that you can specify different page sizes throughout the life of a single search operation. In the following example, the first page is 15 entries, the second page is 20 entries, and the third parameter ends the paged result/search operation:
-q 15 -q 20 -q 0
In the following example, the first page is 15 entries, and all the rest of the pages are 20 entries, continuing with the last specified -q value until the search operation completes:
-q 15 -q 20
The default ldapsearch operation is to return all entries in a single request. No paging is done for the default ldapsearch operation.
<filter> ::='('<filtercomp>')'
<filtercomp> ::= <and>|<or>|<not>|<simple>
<and> ::= '&' <filterlist>
<or> ::= '|' <filterlist>
<not> ::= '!' <filter>
<filterlist> ::= <filter>|<filter><filtertype>
<simple> ::= <attributetype><filtertype>
<attributevalue>
<filtertype> ::= '='|'~='|'<='|'>='
The '~=' construct is used to specify approximate matching. The representation for <attributetype> and <attributevalue> are as described in "RFC 2252, LDAP V3 Attribute Syntax Definitions". In addition, <attributevalue> can be a single * to achieve an attribute existence test, or can contain text and asterisks ( * ) interspersed to achieve substring matching.
For example, the filter "mail=*" finds any entries that have a mail attribute. The filter "mail=*@student.of.life.edu" finds any entries that have a mail attribute ending in the specified string. To put parentheses in a filter, escape them with a backslash (\) character.
See "RFC 2254, A String Representation of LDAP Search Filters" for a more complete description of allowable filters.
If one or more entries are found, each entry is written to standard output in the form:
Distinguished Name (DN)
attributename=value
attributename=value
attributename=value
...
Multiple entries are separated with a single blank line. If the -F option is used to specify a separator character, it will be used instead of the `=' character. If the -t option is used, the name of a temporary file is used in place of the actual value. If the -A option is given, only the "attributename" part is written.
The following command:
ldapsearch "cn=john doe" cn telephoneNumber
performs a subtree search (using the default search base) for entries with a commonName of "john doe". The commonName and telephoneNumber values is retrieved and printed to standard output. The output might look something like this if two entries are found:
cn=John E Doe, ou="College of Literature, Science, and the Arts", ou=Students, ou=People, o=University of Higher Learning, c=US cn=John Doe cn=John Edward Doe cn=John E Doe 1 cn=John E Doe telephoneNumber=+1 313 555-5432 cn=John B Doe, ou=Information Technology Division, ou=Faculty and Staff, ou=People, o=University of Higher Learning, c=US cn=John Doe cn=John B Doe 1 cn=John B Doe telephoneNumber=+1 313 555-1111
The command:
ldapsearch -t "uid=jed" jpegPhoto audio
performs a subtree search using the default search base for entries with user id of "jed". The jpegPhoto and audio values are retrieved and written to temporary files. The output might look like this if one entry with one value for each of the requested attributes is found:
cn=John E Doe, ou=Information Technology Division, ou=Faculty and Staff, ou=People, o=University of Higher Learning, c=US audio=/tmp/ldapsearch-audio-a19924 jpegPhoto=/tmp/ldapsearch-jpegPhoto-a19924
This command:
ldapsearch -L -s one -b "c=US" "o=university*" o description
will perform a one-level search at the c=US level for all organizations whose organizationName begins with university. Search results will be displayed in the LDIF format (see LDAP Data Interchange Format). The organizationName and description attribute values will be retrieved and printed to standard output, resulting in output similar to this:
dn: o=University of Alaska Fairbanks, c=US o: University of Alaska Fairbanks description: Preparing Alaska for a brave new tomorrow description: leaf node only dn: o=University of Colorado at Boulder, c=US o: University of Colorado at Boulder description: No personnel information description: Institution of education and research dn: o=University of Colorado at Denver, c=US o: University of Colorado at Denver o: UCD o: CU/Denver o: CU-Denver description: Institute for Higher Learning and Research dn: o=University of Florida, c=US o: University of Florida o: UFl description: Shaper of young minds ...
This command:
ldapsearch -b "c=US" -o ibm-slapdDN "objectclass=person" ibm-slapdDN
performs a subtree level search at the c=US level for all persons. This special attribute is new in 5.1 and when used for sorted searches, the search results are sorted by the string representation of the Distinguished Name (DN). The output might look something like this:
cn=Al Edwards,ou=Widget Division,ou=Austin,o=IBM,c=US cn=Al Garcia,ou=Home Entertainment,ou=Austin,o=IBM,c=US cn=Amy Nguyen,ou=In Flight Systems,ou=Austin,o=IBM,c=US cn=Arthur Edwards,ou=Widget Division,ou=Austin,o=IBM,c=US cn=Becky Garcia,ou=In Flight Systems,ou=Austin,o=IBM,c=US cn=Ben Catu,ou=In Flight Systems,ou=Austin,o=IBM,c=US cn=Ben Garcia Jr,ou=Home Entertainment,ou=Austin,o=IBM,c=US cn=Bill Keller Jr.,ou=In Flight Systems,ou=Austin,o=IBM,c=US cn=Bob Campbell,ou=In Flight Systems,ou=Austin,o=IBM,c=US
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The contents of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as trusted, you can establish a trust relationship with LDAP servers that use certificates issued by one of the CAs that are marked as trusted. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted (including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s (see the LDAP_Bind APIs).
For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
ldapadd, ldapchangepwd, ldapdelete, ldapexop, ldapmodify, ldapmodrdn
The administration daemon control program.
ibmdirctl [-D adminDN] [-h hostname] [-K keyfile] [ -N key_name ]
[-p port] [-v] [-w adminPW | ?] [-Z] [-?]
command -- [ibmslapd options]
where command is {start|stop|restart|status}
The administration daemon control program, ibmdirctl, is used to start, stop, restart or query the status of the IBM Directory Server. If ibmslapd options are requested, they must be preceded by the --.
To display syntax help for ibmdirctl, type ibmdirctl -?.
Notes:
To start the server in configuration only mode issue the command:
ibmdirctl -h mymachine -D myDN -w mypassword -p 3538 start -- -a
To stop the server issue the command:
ibmdirctl -h mymachine -D myDN -w mypassword -p 3538 stop
This sections describes the server utilities.
Notes:
The LDAP Data Interchange Format (LDIF) tool ldif is a shell-accessible utility that converts arbitrary data values to LDIF. It reads input values from standard input and produces records appropriate for use in an LDIF file.
See Appendix D, LDAP data interchange format (LDIF) for more information about LDIF.
To find the LDIF format for the attribute sn (surname) with a value of smith at a command line enter:
Using the -b option:
This program is used to load entries specified in text LDAP Directory Interchange Format (LDIF) into a directory stored in a relational database. The database must already exist. ldif2db can be used to add entries to an empty directory database or to a database that already contains entries.
Notes:
All other command line inputs result in a syntax error message, after which the correct syntax is displayed.
The bulkload utility is used to load the directory data from an LDIF file. It is a faster alternative to ldif2db and is available for bulk-loading large amounts of data in LDIF format.
Notes:
update database configuration for ldapdb2 using LOGRETAIN OFF USEREXIT OFF
bulkload -i <ldiffile> -s $
Schema checking verifies that all object classes and attributes have been defined, that all attributes specified for each entry comply with the list of "required" and "allowed" attributes in the object class definition, and that binary attribute values are in the correct 64-bit encoded form.
The recommended approach is to use the -S only option first to validate the data, and thereafter to use the default -S no whenever loading the data into the directory.
For better performance the bulkload tool assumes that the data in the input file is correct or that the data has been checked in an earlier loading. The bulkload tool can, however, perform some basic checks on the input data.
The bulkload utility cannot run while the directory server (slapd) is running.
In addition to the disk space required for data storage in the local database directory, the bulkload tool requires temporary storage for data manipulation before inserting the data into the database. The default path for this temporary storage is platform specific. See the -L option description for the path names. You can change the path using the -L option:
bulkload -i <ldiffile> -L /newpath
You must have write permission to this directory. You need temporary storage at least 2.5 times the size of the LDIF file that is available in the ldapimport directory. You still might need additional temporary storage depending on your data.
If you receive an error like the following:
SQL3508N Error in accessing a file of type "SORTDIRECTORY" during load or load query. Reason code: "2". Path: "/u/ldapdb2/sqllib/tmp/".
you need to set the environment variable DB2SORTTMP to a directory (or directories) in a file system with more space to be utilized during the bulkload. Multiple directories can be specified separated by a comma ( , ) as in:
export DB2SORTTMP=/sortdir1,/sortdir2
When running bulkload, inspect the output messages carefully. If errors occur during execution, the directory might be incompletely populated. You might need to drop all the LDAP tables, or drop the database (recreate an empty database), and start over. If this happens, no data was added to the directory, and the bulkload must be attempted again. In addition, you might lose data when you drop all the LDAP tables.
The file /usr/ldap/examples/sample.ldif includes sample data. You can use the data in the file to experiment with populating a directory using the bulkload tool, or you can use the ldif2db command line utility. However, the ldif2db utility might be considerably slower than the bulkload utility for large amounts of data.
For performance reasons, the bulkload tool does not check for duplicate entries. Ensure that your input LDIF file does not contain duplicate entries. If any duplicates exist, remove the duplicate entries.
If bulkload fails at the DB2 LOAD phase, see the db2load.log file for the reasons. This log file is located on the Windows operating systems in c:\tmp\ldapimport, on AIX operating systems in /tmp/ldapimport, and on Linux , Solaris, and HP operating systems in /var/ldap/ldapimport. If the -L option was specified, find the file in the directory defined by the -L option. Correct the problem and rerun bulkload. Bulkload reloads the files from the last successful load consistency point.
When bulkload fails, the recovery information is stored in <installation directory>/etc/bulkload_status. This file is not removed until all of the data is loaded successfully. This insures the data integrity of the directory. If you decide to reconfigure the database and start over, the bulkload_status file needs to be removed manually or bulkload still tries to recover from the last successful load point.
This program is used to dump entries from a directory stored in a relational database into a text file in LDAP Directory Interchange Format (LDIF).
All other command line inputs result in a syntax error message, after which the proper syntax is displayed.
The LDAP replica synchronization tool
ldapdiff -b baseDN -sh host -ch host [-a] [-C countnumber] [-cD dn] [-cK keyStore] [-cw password] -[cN keyStoreType] [-cp port] [-cP keyStorePwd] [-ct trustStoreType] [-cT trustStore] [-cY trustStorePwd] [-cZ] [-F] [-L filename] [-sD dn] [-sK keyStore] [-sw password] -[sN keyStoreType] [-sp port] [-sP keyStorePwd] [-st trustStoreType] [-sT trustStore] [-sY trustStorePwd] [-sZ] [-v]
or
ldapdiff -S -sh host -ch host [-a] [-C countnumber][-cD dn] [-cK keyStore] [-cw password] -[cN keyStoreType] [-cp port] [-cP keyStorePwd] [-ct trustStoreType] [-cT trustStore] [-cY trustStorePwd] [-cZ] [-L filename] [-sD dn] [-sK keyStore] [-sw password] [-sN keyStoreType] [-sp port] [-sP keyStorePwd] [-st trustStoreType] [-sT trustStore] [-sY trustStorePwd] [-sZ] [-v]
This tool synchronizes a replica server with its master. To display syntax help for ldapdiff, type:
ldapdiff -?
The following options apply to the ldapdiff command. There are two subgroupings that apply specifically to either the supplier server or the consumer server.
The following options apply to the consumer server and are denoted by an initial 's' in the option name.
A default keyring file that is, ldapkey.kdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -sZ switch.
A default keyring file that is, ldapkey.tdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -sZ switch.
The following options apply to the consumer server and are denoted by an initial 'c' in the option name.
A default keyring file that is, ldapkey.kdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -cZ switch.
A default keyring file that is, ldapkey.tdb, and the associated password stash file that is, ldapkey.sth, are installed in the /lib directory under LDAPHOME, where LDAPHOME is the path to the installed LDAP support. LDAPHOME varies by operating system platform:
See IBM Directory C-Client SDK Programming Reference for more information about default key database files, and default Certificate Authorities.
If a keyring database file cannot be located, a "hard-coded" set of default trusted certificate authority roots is used. The key database file typically contains one or more certificates of certificate authorities (CAs) that are trusted by the client. These types of X.509 certificates are also known as trusted roots. For more information on managing an SSL key database, see Using gsk6ikm. Also see the SSL notes and Secure Sockets Layer for more information about SSL and certificates.
This parameter effectively enables the -cZ switch.
ldapdiff -b <baseDN> -sh <supplierhostname> -ch <consumerhostname> [options]
or
ldapdiff -S > -sh <supplierhostname> -ch <consumerhostname> [options]
If no DN arguments are provided, the ldapdiff command waits to read a list of DNs from standard input. To break out of the wait, use Ctrl+C or Ctrl+D.
To use the SSL-related functions associated with this utility, the SSL libraries and tools must be installed. The SSL libraries and tools are provided with IBM's Global Security Kit (GSKit), which includes security software developed by RSA Security Inc.
The content of a client's key database file is managed with the gsk6ikm utility. For more information on this Java utility, see Using gsk6ikm. The gsk6ikm utility is used to define the set of trusted certification authorities (CAs) that are to be trusted by the client. By obtaining certificates from trusted CAs, storing them in the key database file, and marking them as 'trusted', you can establish a trust relationship with LDAP servers that use 'trusted' certificates issued by one of the trusted CAs. The gsk6ikm utility can also be used to obtain a client certificate, so that client and server authentication can be performed.
If the LDAP servers accessed by the client use server authentication only, it is sufficient to define one or more trusted root certificates in the key database file. With server authentication, the client can be assured that the target LDAP server has been issued a certificate by one of the trusted CAs. In addition, all LDAP transactions that flow over the SSL connection with the server are encrypted including the LDAP credentials that are supplied on the ldap_bind or ldap_simple_bind_s. For example, if the LDAP server is using a high-assurance VeriSign certificate, you should obtain a CA certificate from VeriSign, import it into your key database file, and mark it as trusted. If the LDAP server is using a self-signed server certificate, the administrator of the LDAP server can supply you with a copy of the server's certificate request file. Import the certificate request file into your key database file and mark it as trusted.
If the LDAP servers accessed by the client use client and server authentication, it is necessary to:
Exit status is 0 if no errors occur. Errors result in a non-zero exit status and a diagnostic message being written to standard error.
On UNIX-based systems file, permissions are frequently altered inadvertently by the actions of copying or editing a key database file. This is because these actions are generally done as the userid root, therefore permissions are set for the user root. For the Directory Server to make use of this file, you must change the file permissions so that it is readable by the userid ldap. Otherwise the Directory Server fails to start.
chown ldap:ldap <mykeyring>.*
Before IBM Directory Server 4.1, the LDAP server uses LDAP as its Kerberos service name, (LDAP/ldaphost.austin.ibm.com, ldaphost is the hostname of the machine where the LDAP server is located) to communicate with its client and the Kerberos KDC. For Version 4.1 and above, a lower case service name is used (ldap/ldapname.austin.ibm.com). Because of this change, a 4.1 or 5.1 server might not be able to start after migrating from a 3.x server. This is because the 4.1 or 5.1 server is looking for ldap in the keytab file in which an LDAP service name was located and used by the previous 3.x server. To correct this situation you can do either of the following:
Starting the embedded version of IBM Websphere Application Server - Express on AIX (startServer.sh server1), might not work because port (9090) already being used. See the BOBCAT_install_path/logs/server1 directory for the actual log files. Usually SystemErr.log and SystemOut.log are most helpful, although the other logs might have some useful information.
To change the port number for the embedded version of IBM Websphere Application Server - Express from 9090 to 9091, which is the port used on AIX machines, edit the BOBCAT_install_path/config/cells/DefaultNode/virtualhosts.xml file and change 9090 to 9091. Do the same thing in the
BOBCAT_install_path/config/cells/DefaultNode/nodes/DefaultNode/servers/
server1/server.xml
file.
During configuration, you might experience some problems with the IBM Directory configuration programs. There are some extra debugging steps that can help you and IBM support teams determine the cause of these problems.
There are three configuration programs in the IBM Directory product. Two are run from a command line, and one is GUI-based. The configuration programs are:
See the IBM Directory Server Version 5.1 Installation and Configuration Guide for information on these utilities.
These configuration programs support two main functions:
The configuration of the Admin DN is very straightforward. Generally, the only reasons the configuration of the Admin DN fails are if the IBM Directory configuration file ( <install dir>/etc/ibmslapd.conf ) has had the permissions accidentally changed, or if the user enters an invalid DN.
This leaves the most problematic option, the database configuration/unconfiguration. Because there are so many variables at play during configuration, errors can occur. Some of the factors that can affect this option are:
If the database configuration fails, the bottom-line question for the user is, "What failed, and how do I fix it?" The following sections describe sources of output that can be used to debug configuration problems.
There are several "standard" sources of information available to the user:
All of the configuration programs are either started from a console command line prompt (ldapcfg, ldapucfg) or open a background console (ldapxcfg). As the database configuration progresses, status messages (and limited error messages) are displayed in the associated console window. If a problem occurs, the user should copy these messages to the system clipboard and then save them in a file for the support teams.
If the error is a direct error from DB2, then DB2 often creates message/error files in the /tmp directory (on UNIX platforms). If the user has a database configuration problem on UNIX systems , they need to examine all of the files in the /tmp directory that were created around the time of the attempted configuration. On Windows systems , examine any DB2 error logs in your DB2 install directory under the directory named for the instance you were trying to configure. For example, if your were trying to create the default ldapdb2 instance and database, and if your DB2 was installed in D:\sqllib, then you need to examine the files in the D:\sqllib\ldadb2 directory if it exists. Especially look for and examine the 'db2diag.log' file in that directory.
IBM Directory logs most configuration errors in the file 'ldacfg.out'. On UNIX platforms, this file can be found in the /tmp directory. On Windows platforms, this file is created in the root directory of the drive you ran configuration from.
There are two more sources of output that can be used to debug configuration problems. Both of them are initiated by setting environment variables before running the configuration. For both of these debug options, it is strongly recommended that your console window be set to scrollable so that any messages that scroll off the screen can be seen later.
JAVA_DEBUG=1
On UNIX platforms, use export JAVA_DEBUG=1. This causes certain Java debug information built into the code to be displayed on stdout (the console).
LDAP_DBG =1
On UNIX platforms, use export LDAP_DBG=1. This causes a debug file to be created for the IBM support and development teams. The file name that is created is dbg.log.
On the Windows NT and Windows 2000 platforms, dbg.log is created in the <ldapinstalldir> /var directory. On UNIX platforms, dbg.log is created in the /var/ldap directory.
The ibmslapd command has two parameters on UNIX systems and an additional two parameters on Windows systems.
Additional parameters for Windows systems:
If the error logs do not provide enough information to resolve a problem, you can run the IBM Directory Server in a special debug mode that generates very detailed information. The server executable ibmslapd must be run from a command prompt to enable debug output. The syntax is as follows:
ldtrc on ibmslapd -h bitmaskwhere the specified bitmask value determines which categories of debug output are generated.
| Hex | Decimal | Value | Description |
|---|---|---|---|
| 0x0001 | 1 | LDAP_DEBUG_TRACE | Entry and exit from routines |
| 0x0002 | 2 | LDAP_DEBUG_PACKETS | Packet activity |
| 0x0004 | 4 | LDAP_DEBUG_ARGS | Data arguments from requests |
| 0x0008 | 8 | LDAP_DEBUG_CONNS | Connection activity |
| 0x0010 | 16 | LDAP_DEBUG_BER | Encoding and decoding of data |
| 0x0020 | 32 | LDAP_DEBUG_FILTER | Search filters |
| 0x0040 | 64 | LDAP_DEBUG_MESSAGE | Messaging subsystem activities and events |
| 0x0080 | 128 | LDAP_DEBUG_ACL | Access Control List activities |
| 0x0100 | 256 | LDAP_DEBUG_STATS | Operational statistics |
| 0x0200 | 512 | LDAP_DEBUG_THREAD | Threading statistics |
| 0x0400 | 1024 | LDAP_DEBUG_REPL | Replication statistics |
| 0x0800 | 2048 | LDAP_DEBUG_PARSE | Parsing activities |
| 0x1000 | 4096 | LDAP_DEBUG_PERFORMANCE | Relational backend performance statistics |
| 0x1000 | 8192 | LDAP_DEBUG_RDBM | Relational backend activities (RDBM) |
| 0x4000 | 16384 | LDAP_DEBUG_REFERRAL | Referral activities |
| 0x8000 | 32768 | LDAP_DEBUG_ERROR | Error conditions |
| 0xffff | 65535 | ALL |
|
| 0x7fffffff | 2147483647 | LDAP_DEBUG_ANY | All levels of debug |
For example, specifying a bitmask value of "65535" turns on full debug output and generates the most complete information.
When you are finished, issue the following command at a command prompt:
ldtrc off
It is recommended that you contact IBM Service for assistance with interpreting of the debug output and resolving of the problem.
If you are using Windows 2000 or Windows NT and have a master server configured to do replication, you might see an error like the following in the ibmslapd error log during updates :
[IBM][CLI Driver] CLI0157E Error opening a file. SQLSTATE=S1507
This problem can be resolved by adding the following stanza to the \sqllib\db2cli.ini file:
[COMMON] TempDir=x:\<your directory>
where x:\<your directory> specifies an existing directory on a drive that has space available. DB2 database writes temporary files to this directory. The amount of space required depends on the size of the directory entries you are adding or updating, but generally does require more space than the size of the largest entry you are updating.
You can configure DB2 to enforce unique values for an LDAP attribute, such as UID, in the IBM Directory Server. There are some requirements:
All of the values for the attribute must be stored on each LDAP server where values for the attribute can be created or updated. This means that you cannot have referrals in the directory tree that point to other servers that contain values for the attribute. If you have multiple masters (peer servers) where values for the attribute can be updated, be sure that your directory administrators and applications update the attribute on only one of these servers. If applications created, for example, the same value for the UID attribute on two peer servers at exactly the same time, replication conflicts might occur.
The following is a simple procedure you can use to enforce unique values for UID. In this procedure, you issue the SQL statement to set up a DB2 constraint on the table that contains the UID attribute. Then DB2 ensures that the attribute values are unique. To make this work, you must know how to set the parameters of the SQL statement. The first two steps in this procedure determine these SQL statement parameters. The third step creates the SQL constraint.
You can tell what the maximum length of an attribute is by looking at its definition in the LDAP schema, for example with the Web Administration Tool. Note that in the case of the UID attribute, the default length in the schema packaged with the IBM Directory Server is 256. Therefore, the second point is true for this attribute. In this example, we must set a uniqueness constraint on the column "UID_T". If we try to set it on the "UID" column, the SQL command fails because the required index cannot be created.
db2 alter table "ldapdb2.uid" add CONSTRAINT const1 UNIQUE (uid_t)
This SQL statement establishes the constraint. Notice that the UNIQUE parameter value is uid_t because the UID attribute can be longer than 255 characters. From now on, DB2 does not allow a value to be specified, if the first 255 characters are not unique in the local database. The constraint is named const1 in this example, but you can name it anything you want. Remember the constraint name in case you want to drop it and allow non-unique values again. To drop the uniqueness constraint issue the following SQL command:
alter table "ldapdb2.uid" drop constraint const1
When an application tries to add an entry to the directory with a value for the UID attribute that duplicates an existing directory entry, an error with result code 20 is returned from the LDAP server; for example:
LDAP: error code 20 - Attribute or Value Exists
The possible values for an LDAP error code are shown in the
following tables:
Table 13. General return codes
| Dec value | Value | Hex value | Brief description | Detailed description |
|---|---|---|---|---|
| 00 | LDAP_SUCCESS | 00 | Success | The request was successful. |
| 00 | LDAP_OPERATIONS_ERROR | 01 | Operations error | An operations error occurred. |
| 02 | LDAP_PROTOCOL_ERROR | 02 | Protocol error | A protocol violation was detected. |
| 03 | LDAP_TIMELIMIT_EXCEEDED | 03 | Time limit exceeded | An LDAP time limit was exceeded. |
| 04 | LDAP_SIZELIMIT_EXCEEDED | 04 | Size limit exceeded | An LDAP size limit was exceeded. |
| 05 | LDAP_COMPARE_FALSE | 05 | Compare false | A compare operation returned false. |
| 06 | LDAP_COMPARE_TRUE | 06 | Compare true | A compare operation returned true. |
| 07 | LDAP_STRONG_AUTH_NOT_SUPPORTED | 07 | Strong authentication not supported | The LDAP server does not support strong authentication. |
| 08 | LDAP_STRONG_AUTH_REQUIRED | 08 | Strong authentication required | Strong authentication is required for the operation. |
| 09 | LDAP_PARTIAL_RESULTS | 09 | Partial results and referral received | Partial results only returned. |
| 10 | LDAP_REFERRAL | 0A | Referral returned | Referral returned. |
| 11 | LDAP_ADMIN_LIMIT_EXCEEDED | 0B | Administration limit exceeded | Administration limit exceeded. |
| 12 | LDAP_UNAVAILABLE_CRITICAL_EXTENSION | 0C | Critical extension not supported | Critical extension is not supported. |
| 13 | LDAP_CONFIDENTIALITY_REQUIRED | 0D | Confidentiality is required | Confidentiality is required. |
| 14 | LDAP_SASLBIND_IN_PROGRESS | 0E | SASL bind in progress | An SASL bind is in progress. |
| 16 | LDAP_NO_SUCH_ATTRIBUTE | 10 | No such attribute | The attribute type specified does not exist in the entry. |
| 17 | LDAP_UNDEFINED_TYPE | 11 | Undefined attribute type | The attribute type specified is not valid. |
| 18 | LDAP_INAPPROPRIATE_MATCHING | 12 | Inappropriate matching | Filter type not supported for the specified attribute. |
| 19 | LDAP_CONSTRAINT_VIOLATION | 13 | Constraint violation | An attribute value specified violates some constraint (for example, a postal address has too many lines, or a line that is too long). |
| 20 | LDAP_TYPE_OR_VALUE_EXISTS | 14 | Type or value exists | An attribute type or attribute value specified already exists in the entry. |
| 21 | LDAP_INVALID_SYNTAX | 15 | Invalid syntax | An attribute value that is not valid was specified. |
| 32 | LDAP_NO_SUCH_OBJECT | 20 | No such object | The specified object does not exist in the directory. |
| 33 | LDAP_ALIAS_PROBLEM | 21 | Alias problem | An alias in the directory points to a nonexistent entry. |
| 34 | LDAP_INVALID_DN_SYNTAX | 22 | Invalid DN syntax | A DN that is syntactically not valid was specified. |
| 35 | LDAP_IS_LEAF | 23 | Object is a leaf | The object specified is a leaf. |
| 36 | LDAP_ALIAS_DEREF_PROBLEM | 24 | Alias dereferencing problem | A problem was encountered when dereferencing an alias. |
| 48 | LDAP_INAPPROPRIATE_AUTH | 30 | Inappropriate authentication | Inappropriate authentication was specified (for example, LDAP_AUTH_SIMPLE was specified and the entry does not have a userPassword attribute). |
| 49 | LDAP_INVALID_CREDENTIALS | 31 | Invalid credentials | Invalid credentials were presented (for example, the wrong password). |
| 50 | LDAP_INSUFFICIENT_ACCESS | 32 | Insufficient access | The user has insufficient access to perform the operation. |
| 51 | LDAP_BUSY | 33 | DSA is busy | The DSA is busy. |
| 52 | LDAP_UNAVAILABLE | 34 | DSA is unavailable | The DSA is unavailable. |
| 53 | LDAP_UNWILLING_TO_PERFORM | 35 | DSA is unwilling to perform | The DSA is unwilling to perform the operation. |
| 54 | LDAP_LOOP_DETECT | 36 | Loop detected | A loop was detected. |
| 64 | LDAP_NAMING_VIOLATION | 40 | Naming violation | A naming violation occurred. |
| 65 | LDAP_OBJECT_CLASS_VIOLATION | 41 | Object class violation | An object class violation occurred (for example, a "required" attribute was missing from the entry). |
| 66 | LDAP_NOT_ALLOWED_ON_NONLEAF | 42 | Operation not allowed on nonleaf | The operation is not allowed on a nonleaf object. |
| 67 | LDAP_NOT_ALLOWED_ON_RDN | 43 | Operation not allowed on RDN | The operation is not allowed on an RDN. |
| 68 | LDAP_ALREADY_EXISTS | 44 | Already exists | The entry already exists. |
| 69 | LDAP_NO_OBJECT_CLASS_MODS | 45 | Cannot modify object class | Object class modifications are not allowed. |
| 70 | LDAP_RESULTS_TOO_LARGE | 46 | Results too large | Results too large. |
| 71 | LDAP_AFFECTS_MULTIPLE_DSAS | 47 | Affects multiple DSAs | Affects multiple DSAs. |
| 80 | LDAP_OTHER | 50 | Unknown error | An unknown error occurred. |
| 81 | LDAP_SERVER_DOWN | 51 | Can't contact LDAP server | The LDAP library cannot contact the LDAP server. |
| 82 | LDAP_LOCAL_ERROR | 52 | Local error | Some local error occurred. This is usually a failed memory allocation. |
| 83 | LDAP_ENCODING_ERROR | 53 | Encoding error | An error was encountered encoding parameters to send to the LDAP server. |
| 84 | LDAP_DECODING_ERROR | 54 | Decoding error | An error was encountered decoding a result from the LDAP server. |
| 85 | LDAP_TIMEOUT | 55 | Timed out | A time limit was exceeded while waiting for a result. |
| 86 | LDAP_AUTH_UNKNOWN | 56 | Unknown authentication method | The authentication method specified on a bind operation is not known. |
| 87 | LDAP_FILTER_ERROR | 57 | Bad search filter | An invalid filter was supplied to ldap_search (for example, unbalanced parentheses). |
| 88 | LDAP_USER_CANCELLED | 58 | User cancelled operation | The user cancelled the operation. |
| 89 | LDAP_PARAM_ERROR | 59 | Bad parameter to an LDAP routine | An LDAP routine was called with a bad parameter (for example, a NULL ld pointer, etc.). |
| 90 | LDAP_NO_MEMORY | 5A | Out of memory | A memory allocation (for example malloc) call failed in an LDAP library routine. |
| 91 | LDAP_CONNECT_ERROR | 5B | Connection error | Connection error. |
| 92 | LDAP_NOT_SUPPORTED | 5C | Not supported | Not supported. |
| 93 | LDAP_CONTROL_NOT_FOUND | 5D | Control not found | Control not found. |
| 94 | LDAP_NO_RESULTS_RETURNED | 5E | No results returned | No results returned. |
| 95 | LDAP_MORE_RESULTS_TO_RETURN | 5F | More results to return | More results to return. |
| 96 | LDAP_URL_ERR_NOTLDAP | 60 | URL doesn't begin with ldap:// | The URL does not begin with ldap://. |
| 97 | LDAP_URL_ERR_NODN | 61 | URL has no DN (required) | The URL does not have a DN (required). |
| 98 | LDAP_URL_ERR_BADSCOPE | 62 | URL scope string is invalid | The URL scope string is not valid. |
| 99 | LDAP_URL_ERR_MEM | 63 | Can't allocate memory space | Cannot allocate memory space. |
| 100 | LDAP_CLIENT_LOOP | 64 | Client loop | Client loop. |
| 101 | LDAP_REFERRAL_LIMIT_EXCEEDED | 65 | Referral limit exceeded | Referral limit exceeded. |
| 112 | LDAP_SSL_ALREADY_INITIALIZED | 70 | ldap_ssl_client_init successfully called previously in this process | The ldap_ssl_client_init was successfully called previously in this process. |
| 113 | LDAP_SSL_INITIALIZE_FAILED | 71 | Initialization call failed | SSL Initialization call failed. |
| 114 | LDAP_SSL_CLIENT_INIT_NOT_CALLED | 72 | Must call ldap_ssl_client_init before attempting to use SSL connection | Must call ldap_ssl_client_init before attempting to use SSL connection. |
| 115 | LDAP_SSL_PARAM_ERROR | 73 | Invalid SSL parameter previously specified | An SSL parameter that was not valid was previously specified. |
| 116 | LDAP_SSL_HANDSHAKE_FAILED | 74 | Failed to connect to SSL server | Failed to connect to SSL server. |
| 117 | LDAP_SSL_GET_CIPHER_FAILED | 75 | Not used | Deprecated. |
| 118 | LDAP_SSL_NOT_AVAILABLE | 76 | SSL library cannot be located | Ensure that GSKit has been installed. |
| 128 | LDAP_NO_EXPLICIT_OWNER | 80 | No explicit owner found | No explicit owner was found. |
| 129 | LDAP_NO_LOCK | 81 | Could not obtain lock | Client library was not able to lock a required resource. |
In addition, the following DNS-related error codes are defined in
the ldap.h file:
Table 14. DNS-related return codes
| Dec value | Value | Hex value | Detailed description |
|---|---|---|---|
| 133 | LDAP_DNS_NO_SERVERS | 85 | No LDAP servers found |
| 134 | LDAP_DNS_TRUNCATED | 86 | Warning: truncated DNS results |
| 135 | LDAP_DNS_INVALID_DATA | 87 | Invalid DNS Data |
| 136 | LDAP_DNS_RESOLVE_ERROR | 88 | Can't resolve system domain or nameserver |
| 137 | LDAP_DNS_CONF_FILE_ERROR | 89 | DNS Configuration file error |
The following UTF8-related error codes are defined in the
ldap.h file:
Table 15. UTF8-related return codes
| Dec value | Value | Hex value | Detailed description |
|---|---|---|---|
| 160 | LDAP_XLATE_E2BIG | A0 | Output buffer overflow |
| 161 | LDAP_XLATE_EINVAL | A1 | Input buffer truncated |
| 162 | LDAP_XLATE_EILSEQ | A2 | Unusable input character |
| 163 | LDAP_XLATE_NO_ENTRY | A3 | No codeset point to map to |
This documentation describes the LDAP Data Interchange Format (LDIF), as used by the ldapmodify, ldapsearch and ldapadd utilities. The LDIF specified here is also supported by the server utilities provided with the IBM Directory.
LDIF is used to represent LDAP entries in text form. The basic form of an LDIF entry is:
dn: <distinguished name> <attrtype> : <attrvalue> <attrtype> : <attrvalue> ...
A line can be continued by starting the next line with a single space or tab character, for example:
dn: cn=John E Doe, o=University of Higher
Learning, c=US
Multiple attribute values are specified on separate lines, for example:
cn: John E Doe
cn: John Doe
If an <attrvalue> contains a non-US-ASCII character, or begins with a space or a colon ':', the <attrtype> is followed by a double colon and the value is encoded in base-64 notation. For example, the value " begins with a space" would be encoded like this:
cn:: IGJlZ2lucyB3aXRoIGEgc3BhY2U=
Multiple entries within the same LDIF file are separated by a blank line. Multiple blank lines are considered a logical end-of-file.
Here is an example of an LDIF file containing three entries.
dn: cn=John E Doe, o=University of High
er Learning, c=US
cn: John E Doe
cn: John Doe
objectclass: person
sn: Doe
dn: cn=Bjorn L Doe, o=University of High
er Learning, c=US
cn: Bjorn L Doe
cn: Bjorn Doe
objectclass: person
sn: Doe
dn: cn=Jennifer K. Doe, o=University of High
er Learning, c=US
cn: Jennifer K. Doe
cn: Jennifer Doe
objectclass: person
sn: Doe
jpegPhoto:: /9j/4AAQSkZJRgABAAAAAQABAAD/2wBDABALD
A4MChAODQ4SERATGCgaGBYWGDEjJR0oOjM9PDkzODdASFxOQ
ERXRTc4UG1RV19iZ2hnPk1xeXBkeFxlZ2P/2wBDARESEhgVG
...
The jpegPhoto in Jennifer Jensen's entry is encoded using base-64. The textual attribute values can also be specified in base-64 format. However, if this is the case, the base-64 encoding must be in the code page of the wire format for the protocol (that is, for LDAP V2, the IA5 character set and for LDAP V3, the UTF-8 encoding).
The client utilities (ldapmodify and ldapadd) have been enhanced to recognize the latest version of LDIF, which is identified by the presence of the "version: 1" tag at the head of the file. Unlike the original version of LDIF, the newer version of LDIF supports attribute values represented in UTF-8 (instead of the very limited US-ASCII).
However, manual creation of an LDIF file containing UTF-8 values may be difficult. In order to simplify this process, a charset extension to the LDIF format is supported. This extension allows an IANA character set name to be specified in the header of the LDIF file (along with the version number). A limited set of the IANA character sets are supported. See IANA character sets supported by platform for the specific charset values that are supported for each operating system platform.
The version 1 LDIF format also supports file URLs. This provides a more flexible way to define a file specification. File URLs take the following form:
attribute:< file:///path (where path syntax depends on platform)
For example, the following are valid file Web addresses:
jpegphoto:< file:///d:\temp\photos\myphoto.jpg (DOS/Windows style paths)
jpegphoto:< file:///etc/temp/photos/myphoto.jpg (Unix style paths)
You can use the optional charset tag so that the utilities will automatically convert from the specified character set to UTF-8 as in the following example:
version: 1 charset: ISO-8859-1 dn: cn=Juan Griego, o=University of New Mexico, c=US cn: Juan Griego sn: Griego description:: V2hhdCBhIGNhcmVmdWwgcmVhZGVyIHlvd title: Associate Dean title: [title in Spanish] jpegPhoto:> file:///usr/local/photos/jgriego.jpg
In this instance, all values following an attribute name and a single colon are translated from the ISO-8859-1 character set to UTF-8. Values following an attribute name and a double colon (such as description:: V2hhdCBhIGNhcm... ) must be base-64 encoded, and are expected to be either binary or UTF-8 character strings. Values read from a file, such as the jpegPhoto attribute specified by the Web address in the previous example, are also expected to be either binary or UTF-8. No translation from the specified "charset" to UTF-8 is done on those values.
In this example of an LDIF file without the charset tag, content is expected to be in UTF-8, or base-64 encoded UTF-8, or base-64 encoded binary data:
# IBM Directorysample LDIF file # # The suffix "o=IBM, c=US" should be defined before attempting to load # this data. version: 1 dn: o=IBM, c=US objectclass: top objectclass: organization o: IBM dn: ou=Austin, o=IBM, c=US ou: Austin objectclass: organizationalUnit seealso: cn=Linda Carlesberg, ou=Austin, o=IBM, c=US
This same file could be used without the version: 1 header information, as in previous releases of the IBM Directory:
# IBM Directorysample LDIF file # # The suffix "o=IBM, c=US" should be defined before attempting to load # this data. dn: o=IBM, c=US objectclass: top objectclass: organization o: IBM dn: ou=Austin, o=IBM, c=US ou: Austin objectclass: organizationalUnit seealso: cn=Linda Carlesberg, ou=Austin, o=IBM, c=US
The following table defines the set of IANA-defined character sets that can be defined for the charset tag in a Version 1 LDIF file, on a per-platform basis. The value in the left-most column defines the text string that can be assigned to the charset tag. An "X" indicates that conversion from the specified charset to UTF-8 is supported for the associated platform, and that all string content in the LDIF file is assumed to be represented in the specified charset. "n/a" indicates that the conversion is not supported for the associated platform.
String content is defined to be all attribute values that follow an attribute name and a single colon.
See IANA Character Sets for more information about
IANA-registered character sets.
| Character | Locale | DB2 Code Page | |||||
| Set Name | HP-UX | Linux, Linux_390, | NT | AIX | Solaris | UNIX | NT |
| ISO-8859-1 | X | X | X | X | X | 819 | 1252 |
| ISO-8859-2 | X | X | X | X | X | 912 | 1250 |
| ISO-8859-5 | X | X | X | X | X | 915 | 1251 |
| ISO-8859-6 | X | X | X | X | X | 1089 | 1256 |
| ISO-8859-7 | X | X | X | X | X | 813 | 1253 |
| ISO-8859-8 | X | X | X | X | X | 916 | 1255 |
| ISO-8859-9 | X | X | X | X | X | 920 | 1254 |
| ISO-8859-15 | X | n/a | X | X | X |
|
|
| IBM437 | n/a | n/a | X | n/a | n/a | 437 | 437 |
| IBM850 | n/a | n/a | X | X | n/a | 850 | 850 |
| IBM852 | n/a | n/a | X | n/a | n/a | 852 | 852 |
| IBM857 | n/a | n/a | X | n/a | n/a | 857 | 857 |
| IBM862 | n/a | n/a | X | n/a | n/a | 862 | 862 |
| IBM864 | n/a | n/a | X | n/a | n/a | 864 | 864 |
| IBM866 | n/a | n/a | X | n/a | n/a | 866 | 866 |
| IBM869 | n/a | n/a | X | n/a | n/a | 869 | 869 |
| IBM1250 | n/a | n/a | X | n/a | n/a |
|
|
| IBM1251 | n/a | n/a | X | n/a | n/a |
|
|
| IBM1253 | n/a | n/a | X | n/a | n/a |
|
|
| IBM1254 | n/a | n/a | X | n/a | n/a |
|
|
| IBM1255 | n/a | n/a | X | n/a | n/a |
|
|
| IBM1256 | n/a | n/a | X | n/a | n/a |
|
|
| TIS-620 | n/a | n/a | X | X | n/a | 874 | 874 |
| EUC-JP | X | X | n/a | X | X | 954 | n/a |
| EUC-KR | n/a | n/a | n/a | X | X | 970 | n/a |
| EUC-CN | n/a | n/a | n/a | X | X | 1383 | n/a |
| EUC-TW | X | n/a | n/a | X | X | 964 | n/a |
| Shift-JIS | n/a | X | X | X | X | 932 | 943 |
| KSC | n/a | n/a | X | n/a | n/a | n/a | 949 |
| GBK | n/a | n/a | X | X | n/a | 1386 | 1386 |
| Big5 | X | n/a | X | X | X | 950 | 950 |
| GB18030 | n/a | X | X | X | X |
|
|
| HP15CN | X (with non-GB18030) |
|
|
|
|
|
|
These are the configuration object classes and attributes that are included in the IBM Directory Server Version 5.1. They can be found in the V3config.oc and V3.config.at files in the etc directory. They define the objects that can appear in the ibmslapd.conf file.
These are the schema object classes that are shipped with the IBM Directory Server Version 5.1
# File generated at 3:51:37 PM on 8/28/02 from IBM LDAP schema version 1.5 objectclasses=( 1.3.18.0.2.6.489 NAME 'ibm-slapdAdmin' DESC 'Global configuration settings for IBM Admin Daemon' SUP ( ibm-slapdConfigEntry $ top ) STRUCTURAL MUST ( cn $ ibm-slapdErrorLog $ ibm-slapdPort ) MAY ( ibm-slapdSecurePort ) ) objectclasses=( 1.3.18.0.2.6.490 NAME 'ibm-slapdConfigBackend' DESC 'Config backend configuration for IBM Directory' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdPlugin $ ibm-slapdSuffix ) MAY ( ibm-slapdReadOnly ) ) objectclasses=( 1.3.18.0.2.6.486 NAME 'ibm-slapdConfigEntry' DESC 'ibm slapd config entry' SUP 'top' ABSTRACT MUST ( cn ) MAY ( ibm-slapdInvalidLine ) ) objectclasses=( 1.3.18.0.2.6.493 NAME 'ibm-slapdCRL' DESC 'Certificate revocation list settings for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdLdapCrlHost $ ibm-slapdLdapCrlPort ) MAY ( ibm-slapdLdapCrlPassword $ ibm-slapdLdapCrlUser ) ) objectclasses=( 1.3.18.0.2.6.500 NAME 'ibm-slapdEventNotification' DESC 'Global event notification settings for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdEnableEventNotification ) MAY ( ibm-slapdMaxEventsPerConnection $ ibm-slapdMaxEventsTotal ) ) objectclasses=( 1.3.18.0.2.6.501 NAME 'ibm-slapdFrontEnd' DESC 'Global front-end settings which the server will load at startup.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn ) MAY ( ibm-slapdPlugin $ ibm-slapdSetenv $ ibm-slapdIdleTimeOut $ ibm-slapdACLCache $ ibm-slapdACLCacheSize $ ibm-slapdFilterCacheSize $ ibm-slapdFilterCacheBypassLimit $ ibm-slapdEntryCacheSize $ ibm-slapdDB2CP ) ) objectclasses=( 1.3.18.0.2.6.494 NAME 'ibm-slapdKerberos' DESC 'Global kerberos authentication settings for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdKrbAdminDN $ ibm-slapdKrbEnable $ ibm-slapdKrbIdentityMap $ ibm-slapdKrbKeyTab $ ibm-slapdKrbRealm ) ) objectclasses=( 1.3.18.0.2.6.495 NAME 'ibm-slapdLdcfBackend' DESC 'LDCF backend configuration for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn ) MAY ( ibm-slapdSuffix $ ibm-slapdPlugin ) ) objectclasses=( 1.3.18.0.2.6.526 NAME 'ibm-slapdPendingMigration' DESC 'Indicates that a server component requires migration.' SUP 'top' AUXILIARY MAY ( ibm-slapdMigrationInfo ) ) objectclasses=( 1.3.18.0.2.6.497 NAME 'ibm-slapdRdbmBackend' DESC 'DB2 database backend configuration for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdDbName $ ibm-slapdDbInstance $ ibm-slapdDbUserID $ ibm-slapdDbUserPW ) MAY ( ibm-slapdPlugin $ ibm-slapdSuffix $ ibm-slapdReadOnly $ ibm-slapdChangeLogMaxEntries $ ibm-slapdPagedResAllowNonAdmin $ ibm-slapdPagedResLmt $ ibm-slapdPageSizeLmt $ ibm-slapdSortKeyLimit $ ibm-slapdSortSrchAllowNonAdmin $ ibm-slapdDbConnections $ ibm-slapdDbLocation $ ibm-slapdDB2CP $ ibm-slapdReplDbConns $ ibm-slapdCLIErrors $ ibm-slapdBulkloadErrors $ ibm-slapdDBAlias $ ibm-slapdUseProcessIdPW ) ) objectclasses=( 1.3.18.0.2.6.485 NAME 'ibm-slapdReferral' DESC 'Global superior referrals for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdReferral ) ) objectclasses=( 1.3.18.0.2.6.496 NAME 'ibm-slapdReplication' DESC 'Contains the default bind credentials and master server referral URL. This is used when the server contains one or more replication contexts that are replicated to it by other servers. This server may be acting as one of several masters or as a read only replica. If the MasterDN is specified without the Master PW attribute, kerberos authentication is used.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn ) MAY ( ibm-slapdMasterDN $ ibm-slapdMasterPW $ ibm-slapdMasterReferral ) ) objectclasses=( 1.3.18.0.2.6.499 NAME 'ibm-slapdSchema' DESC 'Global schema settings for IBM Directory. Multiple schemas are not currently supported, but if they were then there would be one ibm-slapdSchema entry per schema.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdSchemaCheck $ ibm-slapdIncludeSchema ) MAY ( ibm-slapdSchemaAdditions ) ) objectclasses=( 1.3.18.0.2.6.492 NAME 'ibm-slapdSSL' DESC 'Global SSL connection settings for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdSecurity $ ibm-slapdSecurePort $ ibm-slapdSslAuth ) MAY ( ibm-slapdSslCertificate $ ibm-slapdSslCipherSpec $ ibm-slapdSslCipherSpecs $ ibm-slapdSSLKeyDatabase $ ibm-slapdSSLKeyDatabasePW $ ibm-slapdSslKeyRingFilePW ) ) objectclasses=( 1.3.18.0.2.6.488 NAME 'ibm-slapdSupplier' DESC 'Contains bind credentials used by a replication supplier server to update the specified subtree on this consumer server. Use of theis object class overrides the default bind credentials specified in an ibm-slapdReplication object' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdReplicaSubtree $ ibm-slapdMasterDN ) MAY ( ibm-slapdMasterPW ) ) objectclasses=( 1.3.18.0.2.6.498 NAME 'ibm-slapdTop' DESC 'Global configuration settings for IBM Directory Server.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdAdminDN $ ibm-slapdAdminPW $ ibm-slapdErrorLog $ ibm-slapdPort $ ibm-slapdPwEncryption $ ibm-slapdSizeLimit $ ibm-slapdSysLogLevel $ ibm-slapdTimeLimit ) MAY ( ibm-slapdServerId $ ibm-slapdVersion $ ibm-slapdACLAccess $ ibm-slapdMaxPendingChangesDisplayed $ ibm-slapdSupportedWebAdmVersion ) ) objectclasses=( 1.3.18.0.2.6.491 NAME 'ibm-slapdTransaction' DESC 'Global transaction support settings for IBM Directory.' SUP ( top $ ibm-slapdConfigEntry ) STRUCTURAL MUST ( cn $ ibm-slapdMaxNumOfTransactions $ ibm-slapdMaxOpPerTransaction $ ibm-slapdMaxTimeLimitOfTransactions $ ibm-slapdTransactionEnable ) )
These are the configuration attributes that are shipped with the IBM Directory Server Version 5.1. For descriptive names to go with the syntax OIDs, see the V3.ldapsyntaxes file in the etc directory.
# File generated at 3:50:52 PM on 8/28/02 from IBM LDAP schema version 1.5
attributetypes=( 1.3.18.0.2.4.2485
NAME 'ibm-slapdACLAccess'
DESC 'If set to true anyone that can read an entry can also read the entrys ACL
attributes. If set to false only the entry owner or the administrator can read
the ACL attributes.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2485
DBNAME( 'slapdACLAccess' 'slapdACLAccess' )
ACCESS-CLASS normal
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2374
NAME 'ibm-slapdACLCache'
DESC 'Controls whether or not the server caches ACL information'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2374
DBNAME( 'ACLCache' 'ACLCache' )
ACCESS-CLASS normal
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2373
NAME 'ibm-slapdACLCacheSize'
DESC 'Maximum number of entries to keep in the ACL Cache'
EQUALITY 2.5.13.14
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2373
DBNAME( 'slapdACLCacheSize' 'slapdACLCacheSize' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2428
NAME 'ibm-slapdAdminDN'
DESC 'Bind DN for the directory administrator, e.g.: cn=root'
EQUALITY 2.5.13.1
ORDERING 1.3.18.0.2.4.405
SYNTAX 1.3.6.1.4.1.1466.115.121.1.12
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2428
DBNAME( 'slapdAdminDN' 'slapdAdminDN' )
ACCESS-CLASS critical
LENGTH 1000
EQUALITY ORDERING )
attributetypes=( 1.3.18.0.2.4.2425
NAME 'ibm-slapdAdminPW'
DESC 'Bind password for the directory administrator'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.5
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2425
DBNAME( 'slapdAdminPW' 'slapdAdminPW' )
ACCESS-CLASS critical )
attributetypes=( 1.3.18.0.2.4.2366
NAME 'ibm-slapdAuthIntegration'
DESC 'Specifies integration of LDAP administrator access with
local OS users. Legal values are : 0 - do not map local OS
users to LDAP administrator, 1 - map local OS users with proper
authority to LDAP administrator. This is supported
only on OS/400.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2366
DBNAME( 'slapdAuthIntegrat' 'slapdAuthIntegrat' )
ACCESS-CLASS system
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2368
NAME 'ibm-slapdBulkloadErrors'
DESC 'File path or device on ibmslapd host machine to which bulkload
error messages will be written. On Windows, forward slashes are
allowed, and a leading slash not preceded by a drive letter is
assumed to be rooted at the install directory
(i.e.: /tmp/bulkload.errors = D:\Program Files\IBM\ldap\tmp\bulkload.errors).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2368
DBNAME( 'slapdBulkloadErro' 'slapdBulkloadErro' )
ACCESS-CLASS normal
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2427
NAME 'ibm-slapdChangeLogMaxEntries'
DESC 'Specifies the maximum number of changelog entries allowed
in the associated backend. Each changelog backend has its own
ibm-slapdChangeLogMaxEntries attribute. If the attribute
is undefined or out of range (negative), it defaults to 0.
Min: 0 (unlimited) Max: 2,147,483,647 (32-bit, signed integer)'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2427
DBNAME( 'chgLogMaxEntries' 'chgLogMaxEntries' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2432
NAME 'ibm-slapdCLIErrors'
DESC 'File path or device on ibmslapd host machine to which DB2 CLI error
messages will be written. On Windows, forward slashes are allowed,
and a leading slash not preceded by a drive letter is
assumed to be rooted at the install directory
(i.e.: /tmp/cli.errors = D:\Program Files\IBM\ldap\tmp\cli.errors).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2432
DBNAME( 'slapdCLIErrors' 'slapdCLIErrors' )
ACCESS-CLASS normal
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2369
NAME 'ibm-slapdDB2CP'
DESC 'Specifies the Code Page of the directory database.
1208 is the code page for UTF-8 databases.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2369
DBNAME( 'slapdDB2CP' 'slapdDB2CP' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2431
NAME 'ibm-slapdDBAlias'
DESC 'The DB2 database alias.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2431
DBNAME( 'slapdDBAlias' 'slapdDBAlias' )
ACCESS-CLASS normal
LENGTH 8 )
attributetypes=( 1.3.18.0.2.4.2417
NAME 'ibm-slapdDbConnections'
DESC 'Specify the number of DB2 connections the server
will dedicate to the DB2 backend. The value must be
between 5 & 50 (inclusive). The ODBCCONS environment variable
overrides this value. If ibm-slapdDbConnections (or ODBCCONS)
is less than 5 or greater than 50, the server will use 5 or 50
respectively. Additional connections may be created for
replication and change log.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2417
DBNAME( 'DbConnections' 'DbConnections' )
ACCESS-CLASS critical
LENGTH 2 )
attributetypes=( 1.3.18.0.2.4.2418
NAME 'ibm-slapdDbInstance'
DESC 'The DB2 database instance for this backend.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2418
DBNAME( 'slapdDbInstance' 'slapdDbInstance' )
ACCESS-CLASS critical
LENGTH 8 )
attributetypes=( 1.3.18.0.2.4.2382
NAME 'ibm-slapdDbLocation'
DESC 'The file system path where the backend database is
located. On Unix this is usually the home directory of the
DB2INSTANCE owner (e.g.: /home/ldapdb2). On windows its just
a drive specifier (e.g.: D:)'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2382
DBNAME( 'slapdDbLocation' 'slapdDbLocation' )
ACCESS-CLASS critical
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2426
NAME 'ibm-slapdDbName'
DESC 'The DB2 database name for this backend.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2426
DBNAME( 'slapdDbName' 'slapdDbName' )
ACCESS-CLASS critical
LENGTH 8 )
attributetypes=( 1.3.18.0.2.4.2422
NAME 'ibm-slapdDbUserID'
DESC 'The user name with which to connect to the DB2 database
for this backend.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2422
DBNAME( 'slapdDbUserID' 'slapdDbUserID' )
ACCESS-CLASS critical
LENGTH 8 )
attributetypes=( 1.3.18.0.2.4.2423
NAME 'ibm-slapdDbUserPW'
DESC 'The user password with which to connect to the DB2 database
for this backend.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.5
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2423
DBNAME( 'slapdDbUserPW' 'slapdDbUserPW' )
ACCESS-CLASS critical )
attributetypes=( 1.3.18.0.2.4.2421
NAME 'ibm-slapdEnableEventNotification'
DESC 'If set to FALSE, the server will reject all extended
operation requests to register for event notification with
the extended result LDAP_UNWILLING_TO_PERFORM.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2421
DBNAME( 'enableEvntNotify' 'enableEvntNotify' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2372
NAME 'ibm-slapdEntryCacheSize'
DESC 'Maximum number of entries to keep in the entry cache'
EQUALITY 2.5.13.14
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2372
DBNAME( 'slapdRDBMCacheSiz' 'slapdRDBMCacheSiz' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2424
NAME 'ibm-slapdErrorLog'
DESC 'File path or device on the ibmslapd host machine to which error
messages will be written. On Windows, forward slashes are
allowed, and a leading slash not preceded by a drive letter
is assumed to be rooted at the install directory
(i.e.: /tmp/slapd.errors = D:\Program Files\IBM\ldap\tmp\slapd.errors).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2424
DBNAME( 'slapdErrorLog' 'slapdErrorLog' )
ACCESS-CLASS critical
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2371
NAME 'ibm-slapdFilterCacheBypassLimit'
DESC 'Search filters that match more than this number of entries
will not be added to the Search Filter cache. Because the list
of entry ids that matched the filter are included in this cache,
this setting helps to limit memory use. A value of 0 indicates
no limit.'
EQUALITY 2.5.13.14
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2371
DBNAME( 'slapdRDBMCacheByp' 'slapdRDBMCacheByp' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2370
NAME 'ibm-slapdFilterCacheSize'
DESC 'Specifies the maximum number of entries to keep in
the Search Filter Cache.'
EQUALITY 2.5.13.14
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2370
DBNAME( 'slapdFilterCacheS' 'slapdFilterCacheS' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2378
NAME 'ibm-slapdIdleTimeOut'
DESC 'Reserved for future use.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2378
DBNAME( 'SlapdIdleTimeOut' 'SlapdIdleTimeOut' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2364
NAME 'ibm-slapdIncludeSchema'
DESC 'File path on the ibmslapd host machine containing schema
definitions used by the LDCF backend. Standard values are:
/etc/V3.system.at /etc/V3.system.oc /etc/V3.ibm.at
/etc/V3.ibm.oc /etc/V3.user.at /etc/V3.user.oc
/etc/V3.ldapsyntaxes /etc/V3.matchingrules
/etc/V3.modifiedschema On Windows, forward slashes are allowed,
and a leading slash not preceded by a drive letter is assumed to
be rooted at the install directory
(i.e.: /etc/V3.system.at = D:\Program Files\IBM\ldap\etc\V3.system.at).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2364
DBNAME( 'slapdIncldeSchema' 'slapdIncldeSchema' )
ACCESS-CLASS critical
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2430
NAME 'ibm-slapdInvalidLine'
DESC 'This attribute will be prepended to the beginning of any
configuration attribute for which the value is invalid. This allows
invalid configuration settings to be identified with a simple search
for "ibm-slapdInvalidLine=*".'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2430
DBNAME( 'slapdInvalidLine' 'slapdInvalidLine' )
ACCESS-CLASS normal
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2365
NAME 'ibm-slapdIpAddress'
DESC 'Specifies IP addresses the server will listen on.
These can be IPv4 or IPv6 addresses. If the attribute is
not specified, the server uses all IP addresses assigned
to the host machine. This is supported on OS/400 only.'
EQUALITY 1.3.6.1.4.1.1466.109.114.1
SYNTAX 1.3.6.1.4.1.1466.115.121.1.26
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2365
DBNAME( 'slapdIpAddress' 'slapdIpAddress' )
ACCESS-CLASS system
LENGTH 32 )
attributetypes=( 1.3.18.0.2.4.2420
NAME 'ibm-slapdKrbAdminDN'
DESC 'Specifies the kerberos ID of the LDAP administrator
(e.g. ibm-kn=name@realm). Used when kerberos authentication
is used to authenticate the administrator when logged onto the
Web Admin interface. This is specified instead of adminDN and adminPW.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2420
DBNAME( 'slapdKrbAdminDN' 'slapdKrbAdminDN' )
ACCESS-CLASS critical
LENGTH 512 )
attributetypes=( 1.3.18.0.2.4.2394
NAME 'ibm-slapdKrbEnable'
DESC 'Must be one of { TRUE | FALSE }. Specifies whether the
server supports kerberos authentication.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2394
DBNAME( 'slapdKrbEnable' 'slapdKrbEnable' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2419
NAME 'ibm-slapdKrbIdentityMap'
DESC 'If set to TRUE, when a client is authenticated with
a kerberos ID, the server will search for a local user
with matching kerberos credentials, and add that user
DN to the connections bind credentials. This allows ACLs
based on LDAP user DNs to still be usable with kerberos
authentication.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7 S
INGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2419
DBNAME( 'KrbIdentityMap' 'KrbIdentityMap' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2416
NAME 'ibm-slapdKrbKeyTab'
DESC 'Specifies the LDAP servers keytab file. This file
contains the LDAP servers private key, as associated with
its kerberos account. This file should be protected (like the
servers SSL key database file). On Windows, forward slashes
are allowed, and a leading slash not preceded by a drive
letter (D:) is assumed to be rooted at the install directory
(i.e.: /tmp/slapd.errors = D:\Program Files\IBM\ldap\tmp\slapd.errors).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2416
DBNAME( 'slapdKrbKeyTab' 'slapdKrbKeyTab' )
ACCESS-CLASS critical
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2400
NAME 'ibm-slapdKrbRealm'
DESC 'Specifies the LDAP servers kerberos realm. Used to
publish the ldapservicename attribute in the root DSE. Note
that an LDAP server can serve as the repository of
account information for multiple KDCs (and realms), but the
LDAP server, as a kerberos server, can only be a member
of a single realm.'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2400
DBNAME( 'slapdKrbRealm' 'slapdKrbRealm' )
ACCESS-CLASS critical
LENGTH 256 )
attributetypes=( 1.3.18.0.2.4.2415
NAME 'ibm-slapdLdapCrlHost'
DESC 'Specify the hostname of the LDAP server that
contains the Certificate Revocation Lists (CRLs) for
validating client x.509v3 certificates. This parameter
is needed when ibm-slapdSslAuth=serverclientauth AND the
client certificates have been issued for CRL validation'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2415
DBNAME( 'LdapCrlHost' 'LdapCrlHost' )
ACCESS-CLASS critical
LENGTH 256 )
attributetypes=( 1.3.18.0.2.4.2407
NAME 'ibm-slapdLdapCrlPassword'
DESC 'Specify the password that server-side SSL will use
to bind to the LDAP server that contains the Certificate
Revocation Lists (CRLs) for validating client x.509v3
certificates. This parameter may be needed when
ibm-slapdSslAuth=serverclientauth AND the client certificates
have been issued for CRL validation. Note: If the LDAP
server holding the CRLs permits unauthenticated access to
the CRLs (i.e. anonymous access), then ibm-slapdLdapCrlPassword
is not required.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.5
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2407
DBNAME( 'CrlPassword' 'CrlPassword' )
ACCESS-CLASS critical )
attributetypes=( 1.3.18.0.2.4.2404 NAME 'ibm-slapdLdapCrlPort'
DESC 'Specify the LDAP ibm-slapdPort used by the LDAP server
that contains the Certificate Revocation Lists (CRLs) for validating
client x.509v3 certificates. This parameter is needed when
ibm-slapdSslAuth=serverclientauth AND the client certificates
have been issued for CRL validation. (IP ports are unsigned,
16-bit integers in the range 1 - 65535)'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2404
DBNAME( 'LdapCrlPort' 'LdapCrlPort' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2403
NAME 'ibm-slapdLdapCrlUser'
DESC 'Specify the bindDN that server-side SSL will use to bind
to the LDAP server that contains the Certificate Revocation Lists (CRLs)
for validating client x.509v3 certificates. This parameter may be needed
when ibm-slapdSslAuth=serverclientauth AND the client certificates have
been issued for CRL validation. Note: If the LDAP server holding the
CRLs permits unauthenticated access to the CRLs (i.e. anonymous
access), then ibm-slapdLdapCrlUser is not required.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.12
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2403
DBNAME( 'LdapCrlUser' 'LdapCrlUser' )
ACCESS-CLASS critical
LENGTH 1000 )
attributetypes=( 1.3.18.0.2.4.2409
NAME 'ibm-slapdMasterDN'
DESC 'Bind DN used by a replication supplier server. The value has to match
the replicaBindDN in the credentials object associated with the replication
agreement defined between the servers.
When kerberos is used to authenticate to the replica, ibm-slapdMasterDN
must specify the DN representation of the kerberos ID
(e.g. ibm-kn=freddy@realm1). When kerberos is used, MasterServerPW is ignored.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.12
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2409
DBNAME( 'MasterDN' 'MasterDN' )
ACCESS-CLASS critical
LENGTH 1000 )
attributetypes=( 1.3.18.0.2.4.2411
NAME 'ibm-slapdMasterPW'
DESC 'Bind password used by a replication supplier. The value has to
match the replicaBindPW in the credentials object associated with the replication
agreement defined between the servers. When kerberos is used, MasterServerPW
is ignored.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.5
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2411
DBNAME( 'MasterPW' 'MasterPW' )
ACCESS-CLASS critical )
attributetypes=( 1.3.18.0.2.4.2401
NAME 'ibm-slapdMasterReferral'
DESC 'URL of a master replica server (e.g.: ldaps://master.us.ibm.com:636)'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2401
DBNAME( 'MasterReferral' 'MasterReferral' )
ACCESS-CLASS critical
LENGTH 256 )
attributetypes=( 1.3.18.0.2.4.2412
NAME 'ibm-slapdMaxEventsPerConnection'
DESC 'Maximum number of event notifications which can be registered
per connection. Minimum = 0 (unlimited) Maximum = 2,147,483,647'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2412
DBNAME( 'EventsPerCon' 'EventsPerCon' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2405
NAME 'ibm-slapdMaxEventsTotal'
DESC 'Maximum total number of event notifications which can
be registered for all connections. Minimum = 0 (unlimited)
Maximum = 2,147,483,647'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2405
DBNAME( 'MaxEventsTotal' 'MaxEventsTotal' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2439
NAME 'ibm-slapdMaxNumOfTransactions'
DESC 'Maximum number of transactions active at one time.
0 = unlimited'
EQUALITY 2.5.13.29
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2439
DBNAME( 'MaxNumOfTrans' 'MaxNumOfTrans' )
ACCESS-CLASS critical
LENGTH 11
EQUALITY
ORDERING
SUBSTR
APPROX )
attributetypes=( 1.3.18.0.2.4.2385
NAME 'ibm-slapdMaxOpPerTransaction'
DESC 'Maximum number of operations per transaction.
0 = unlimited'
EQUALITY 2.5.13.29
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2385
DBNAME( 'MaxOpPerTrans' 'MaxOpPerTrans' )
ACCESS-CLASS critical
LENGTH 11
EQUALITY
ORDERING
APPROX )
attributetypes=( 1.3.18.0.2.4.2486
NAME 'ibm-slapdMaxPendingChangesDisplayed'
DESC 'Maximum number of pending replication updates to be
displayed for any given replication agreement on a supplier
server.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2486
DBNAME( 'slapdMaxPendingCh' 'slapdMaxPendingCh' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2386
NAME 'ibm-slapdMaxTimeLimitOfTransactions'
DESC 'The maximum timeout value of a pending transaction in
seconds. 0 = unlimited'
EQUALITY 2.5.13.29
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2386
DBNAME( 'MaxTimeOfTrans' 'MaxTimeOfTrans' )
ACCESS-CLASS critical
LENGTH 11
EQUALITY
ORDERING
APPROX )
attributetypes=( 1.3.18.0.2.4.2500
NAME 'ibm-slapdMigrationInfo'
DESC 'Information used to control migration of a component.'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2500
DBNAME( 'slapdMigrationInf' 'slapdMigrationInf' )
ACCESS-CLASS critical
LENGTH 2048 )
attributetypes=( 1.3.18.0.2.4.2376
NAME 'ibm-slapdPagedResAllowNonAdmin'
DESC 'Whether or not the server should allow non-Administrator
bind for paged results requests on a search request. If the
value read from the ibmslapd.conf file is TRUE, the server will
process any client request, including those submitted by a user
binding anonymously. If the value read from the ibmslapd.conf
file is FALSE, the server will process only those client requests
submitted by a user with Administrator authority. If a client
requests paged results with a criticality of TRUE or FALSE for a
search operation, does not have Administrator authority, and the
value read from the ibmslapd.conf file for this attribute is FALSE,
the server will return to the client with return code
insufficientAccessRights - no searching or paging will be performed. '
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2376
DBNAME( 'SlapdPagedNonAdmn' 'SlapdPagedNonAdmn' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2380
NAME 'ibm-slapdPagedResLmt'
DESC 'Maximum number of outstanding paged results search requests
allowed active simultaneously. Range = 0.... If a client requests
a paged results operation, and a maximum number of outstanding paged
results are currently active, then the server will return to the
client with return code of busy - no searching or paging
will be performed.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2380
DBNAME( 'SlapdPagedResLmt' 'SlapdPagedResLmt' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2379
NAME 'ibm-slapdPageSizeLmt'
DESC 'Maximum number of entries to return from search for an
individual page when paged results control is specified, regardless
of any pagesize that may have been specified on the client search
request. Range = 0.... If a client has passed a page size, then
the smaller value of the client value and the value read from
ibmslapd.conf will be used.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2379
DBNAME( 'SlapdPageSizeLmt' 'SlapdPageSizeLmt' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2406
NAME 'ibm-slapdPlugin'
DESC 'A plugin is a dynamically loaded library which extends the
capabilities of the server. An ibm-slapdPlugin attribute specifies
to the server how to load and initialize a plugin library.
The syntax is: keyword filename init_function [args...]
The syntax will be slightly different for each platform
due to library naming conventions.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2406
DBNAME( 'slapdPlugin' 'slapdPlugin' )
ACCESS-CLASS critical
LENGTH 2000 )
attributetypes=( 1.3.18.0.2.4.2408
NAME 'ibm-slapdPort'
DESC 'TCP/IP ibm-slapdPort used for non-SSL connections. Can not
have the same value as ibm-slapdSecurePort. (IP ports are unsigned,
16-bit integers in the range 1 - 65535)'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2408
DBNAME( 'slapdPort' 'slapdPort' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2402
NAME 'ibm-slapdPwEncryption'
DESC 'Must be one of { none | imask | crypt | sha }. Specify the
encoding mechanism for the user passwords before they are stored in
the directory. Defaults to none if unspecified. If the value is set
other than none, SASL cram-md5 bind will fail.'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2402
DBNAME( 'PwEncryption' 'PwEncryption' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2413
NAME 'ibm-slapdReadOnly'
DESC 'Must be one of { TRUE | FALSE }. Specifies whether
the backend can be written to. Defaults to FALSE if unspecified.
If set to TRUE, the server will return LDAP_UNWILLING_TO_PERFORM (0x35)
in response to any client request which would change data in the
readOnly database.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2413
DBNAME( 'ReadOnly' 'ReadOnly' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2487
NAME 'ibm-slapdReferral'
DESC 'Specify the referral LDAP URL to pass back when the
local suffixes do not match the request. Used for superior referral
(i.e. ibm-slapdSuffix is not within the servers naming context).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2487
DBNAME( 'Referral' 'Referral' )
ACCESS-CLASS critical LENGTH 32700 )
attributetypes=( 1.3.18.0.2.4.2434
NAME 'ibm-slapdReplDbConns'
DESC 'Maximum number of database connections for use by replication'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2434
DBNAME( 'slapdReplDbConns' 'slapdReplDbConns' )
ACCESS-CLASS normal
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2367
NAME 'ibm-slapdReplicaSubtree'
DESC 'A DN identifying the top of a replicated subtree.'
EQUALITY 2.5.13.1
SYNTAX 1.3.6.1.4.1.1466.115.121.1.12
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2367
DBNAME( 'slapdReplicaSubtr' 'slapdReplicaSubtr' )
ACCESS-CLASS normal
LENGTH 1000 )
attributetypes=( 1.3.18.0.2.4.2437
NAME 'ibm-slapdSchemaAdditions'
DESC 'File path on the ibmslapd host machine containing additional
schema definitions used by the LDCF backend. Standard values
are: /etc/V3.modifiedschema On Windows, forward slashes are
allowed, and a leading slash not preceded by a drive letter
is assumed to be rooted at the install directory
(i.e.: /etc/V3.system.at = D:\Program Files\IBM\ldap\etc\V3.system.at).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2437
DBNAME( 'slapdSchemaAdditi' 'slapdSchemaAdditi' )
ACCESS-CLASS normal
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2363
NAME 'ibm-slapdSchemaCheck'
DESC 'Must be one of { V2 | V3 | V3_lenient }.
Specifies schema checking mechanism for add/modify operation.
V2 = perform LDAP v2 checking.
V3 = perform LDAP v3 checking.
V3_lenient = not ALL parent object classes are required. Only the immediate
object class is needed when adding entries.'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2363
DBNAME( 'SchemaCheck' 'SchemaCheck' )
ACCESS-CLASS critical
LENGTH 10 )
attributetypes=( 1.3.18.0.2.4.2398
NAME 'ibm-slapdSecurePort'
DESC 'TCP/IP port used for SSL connections. Can not have the same
value as ibm-slapdPort. (IP ports are unsigned, 16-bit integers in
the range 1 - 65535)'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2398
DBNAME( 'SecurePort' 'SecurePort' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2399
NAME 'ibm-slapdSecurity'
DESC 'Must be one of { none | SSL | SSLOnly }. Specifies types of connections
accepted by the server.
none - server listens on non-ssl port only. ssl - server listens on
both ssl and non-ssl ports. sslonly - server listens on ssl port only.'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2399
DBNAME( 'Security' 'Security' )
ACCESS-CLASS critical
LENGTH 7 )
attributetypes=( 1.3.18.0.2.4.2433
NAME 'ibm-slapdServerId'
DESC 'Identifies the server for use in replication'
EQUALITY 1.3.6.1.4.1.1466.109.114.1
SYNTAX 1.3.6.1.4.1.1466.115.121.1.26
SINGLE-VALUE
USAGE userApplications )
IBMAttributetypes=( 1.3.18.0.2.4.2433
DBNAME( 'slapdServerId' 'slapdServerId' )
ACCESS-CLASS normal
LENGTH 240 )
attributetypes=( 1.3.18.0.2.4.2397
NAME 'ibm-slapdSetenv'
DESC 'Server executes putenv() for all values of ibm-slapdSetenv at startup
to modify its own runtime environment. Shell variables (%PATH% or \24LANG)
will not be expanded. The only current use for this attribute is to set
DB2CODEPAGE=1208, which is required if using UCS-2 (Unicode) databases.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2397
DBNAME( 'slapdSetenv' 'slapdSetenv' )
ACCESS-CLASS critical
LENGTH 2000 )
attributetypes=( 1.3.18.0.2.4.2396
NAME 'ibm-slapdSizeLimit'
DESC 'Maximum number of entries to return from search, regardless of any
sizelimit that may have been specified on the client search request.
Range = 0.... If a client has passed a limit, then the smaller value of
the client value and the value read from ibmslapd.conf will be used. If a
client has not passed a limit and has bound as admin DN, then the limit
will be considered unlimited. If the client has not passed a limit and
has not bound as admin DN, then the limit will be that which was read
from ibmslapd.conf file. 0 = unlimited.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2396
DBNAME( 'SizeLimit' 'SizeLimit' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2381 NAME 'ibm-slapdSortKeyLimit'
DESC 'Maximum number of sort conditions (keys) that can be specified on a
single search request. Range = 0.... If a client has passed a search request
with more sort keys than the limit allows, and the sorted search control
criticality is FALSE, then the server will honor the value read from
ibmslapd.conf and ignore any sort keys encountered after the limit has
been reached - searching and sorting will be performed. If a client has
passed a search request with more keys than the limit allows, and the
sorted search control criticality is TRUE, then the server will return to
the client with return code of adminLimitExceeded - no searching or sorting
will be performed.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2381
DBNAME( 'SlapdSortKeyLimit' 'SlapdSortKeyLimit' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2377
NAME 'ibm-slapdSortSrchAllowNonAdmin'
DESC 'Whether or not the server should allow non-Administrator bind for
sort on a search request. If the value read from the ibmslapd.conf file
is TRUE, the server will process any client request, including those
submitted by a user binding anonymously. If the value read from the
ibmslapd.conf file is FALSE, the server will process only those client
requests submitted by a user with Administrator authority. If a client
requests sort with a criticality of TRUE for a search operation, does not
have Administrator authority, and the value read from the ibmslapd.conf file
for this attribute is FALSE, the server will return to the client with return
code insufficientAccessRights - no searching or sorting will be performed.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2377
DBNAME( 'SlapdSortNonAdmin' 'SlapdSortNonAdmin' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2395
NAME 'ibm-slapdSslAuth'
DESC 'Must be one of { serverauth | serverclientauth }. Specify authentication
type for ssl connection. serverauth - supports server authentication at the
client. serverclientauth - supports both server and client authentication.'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2395
DBNAME( 'slapdSslAuth' 'slapdSslAuth' )
ACCESS-CLASS critical
LENGTH 16 )
attributetypes=( 1.3.18.0.2.4.2389
NAME 'ibm-slapdSslCertificate'
DESC 'Specify the label that identifies the servers Personal Certificate
in the key database file. This label is specified when the servers private
key and certificate are created with the ikmgui application. If
ibm-slapdSslCertificate is not defined, the default private key, as defined
in the key database file, is used by the LDAP server for SSL connections.'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2389
DBNAME( 'SslCertificate' 'SslCertificate' )
ACCESS-CLASS critical
LENGTH 128 )
attributetypes=( 1.3.18.0.2.4.2429
NAME 'ibm-slapdSslCipherSpec'
DESC 'SSL Cipher Spec Value must be set to DES-56, RC2-40-MD5, RC4-128-MD5,
RC4-128-SHA, RC4-40-MD5, TripleDES-168, or AES. It identifies the
allowable encryption/decryption methods for establishing a SSL connection
between LDAP clients and the server.'
EQUALITY 1.3.6.1.4.1.1466.109.114.1
SYNTAX 1.3.6.1.4.1.1466.115.121.1.26
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2429
DBNAME( 'slapdSslCipherSpe' 'slapdSslCipherSpe' )
ACCESS-CLASS normal
LENGTH 30 )
attributetypes=( 1.3.18.0.2.4.2362
NAME 'ibm-slapdSslCipherSpecs'
DESC 'This attribute is depricated in favor of ibm-slapdSslCipherSpec.
Specifies a decimal number which identifies the allowable
encryption/decryption methods for establishing a SSL connection
between LDAP client(s) and the server. This number represents the availability
of the encryption/decryption methods supported by the LDAP server.
The pre-defined Cipher values and their descriptions are:
SLAPD_SSL_TRIPLE_DES_SHA_US 0x0A Triple DES encryption with a 168-bit key
and a SHA-1 MAC
SLAPD_SSL_DES_SHA_US 0x09DES encryption with a 56-bit key and a SHA-1 MAC
SLAPD_SSL_RC4_SHA_US 0x05 RC4 encryption with a 128-bit key and a SHA-1 MAC
SLAPD_SSL_RC4_MD5_US 0x04 RC4 encryption with a 128-bit key and a MD5 MAC
SLAPD_SSL_RC4_MD5_EXPORT 0x03 RC4 encryption with a 40-bit key and a MD5 MAC
SLAPD_SSL_RC2_MD5_EXPORT 0x06 RC2 encryption with a 40-bit key and a MD5 MAC'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2362
DBNAME( 'SslCipherSpecs' 'SslCipherSpecs' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2375
NAME 'ibm-slapdSSLKeyDatabase'
DESC 'File path to the LDAP servers SSL key database file. This key database
file is used for handling SSL connections from LDAP clients, as well as for
creating secure SSL connections to replica LDAP servers. On Windows, forward
slashes are allowed, and a leading slash not preceeded by a drive
specifier (D:) is assumed to be rooted at the install directory
(i.e.: /etc/key.kdb = D:\Program Files\IBM\ldap\etc\key.kdb).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2375
DBNAME( 'slapdSSLKeyDataba' 'slapdSSLKeyDataba' )
ACCESS-CLASS critical
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2438 NAME 'ibm-slapdSSLKeyDatabasePW'
DESC 'Specify the password associated with the LDAP servers SSL key database file,
as specified on the ibm-slapdSslKeyDatabase parameter. If the LDAP servers key
database file has an associated password stash file, then the
ibm-slapdSslKeyDatabasePW parameter can be ommitted, or set to
ibm-slapdSslKeyDatabasePW = none. Note that the password stash file must
be located in the same directory as the key database file and it must have
the same file name as the key database file, but with an extension of .sth,
instead of .kdb'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.5
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2438
DBNAME( 'slapdSSLKeyDPW' 'slapdSSLKeyDPW' )
ACCESS-CLASS normal )
attributetypes=( 1.3.18.0.2.4.2392
NAME 'ibm-slapdSslKeyRingFile'
DESC 'file path to the LDAP servers SSL key database file. This key database
file is used for handling SSL connections from LDAP clients, as well as for
creating secure SSL connections to replica LDAP servers. On Windows, forward
slashes are allowed, and a leading slash not preceeded by a drive
specifier (D:) is assumed to be rooted at the install directory
(i.e.: /etc/key.kdb = D:\Program Files\IBM\ldap\etc\key.kdb).'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2392
DBNAME( 'SslKeyRingFile' 'SslKeyRingFile' )
ACCESS-CLASS critical
LENGTH 1024 )
attributetypes=( 1.3.18.0.2.4.2390
NAME 'ibm-slapdSslKeyRingFilePW'
DESC 'Specify the password associated with the LDAP servers SSL key database
file, as specified on the ibm-slapdSslKeyRingFile parameter. If the LDAP servers
key database file has an associated password stash file, then the
ibm-slapdSslKeyRingFilePW parameter can be ommitted, or set to
ibm-slapdSslKeyRingFilePW = none. Note that the password stash file must be
located in the same directory as the key database file and it must have the
same file name as the key database file, but with an extension of .sth,
instead of .kdb.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.5
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2390
DBNAME( 'SslKeyRingFilePW' 'SslKeyRingFilePW' )
ACCESS-CLASS critical )
attributetypes=( 1.3.18.0.2.4.2388
NAME 'ibm-slapdSuffix'
DESC 'Specifies a naming context to be stored in this backend.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.12
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2388
DBNAME( 'slapdSuffix' 'slapdSuffix' )
ACCESS-CLASS critical
LENGTH 1000 )
attributetypes=( 1.3.18.0.2.4.2480
NAME 'ibm-slapdSupportedWebAdmVersion'
DESC 'This attribute defines the earliest version of the web administration
console that supports configuration of this server.'
EQUALITY 2.5.13.2
ORDERING 2.5.13.3
SUBSTR 2.5.13.4
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2480
DBNAME( 'slapdSupWebAdmVer' 'slapdSupWebAdmVer' )
ACCESS-CLASS normal
LENGTH 256 )
attributetypes=( 1.3.18.0.2.4.2393
NAME 'ibm-slapdSysLogLevel'
DESC 'Must be one of { l | m | h }. Level at which debugging
and operation statistics are logged in ibmslapd.log file.
h - high (verbose), m - medium, l - low (terse).'
EQUALITY 2.5.13.2
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2393
DBNAME( 'SysLogLevel' 'SysLogLevel' )
ACCESS-CLASS critical
LENGTH 1 )
attributetypes=( 1.3.18.0.2.4.2391
NAME 'ibm-slapdTimeLimit'
DESC 'Maximum number of number of seconds to spend on search
request, regardless of any timelimit that may have been specified
on the client request. Range = 0.... If a client has passed a limit,
then the smaller value of the client value and the value read from
ibmslapd.conf will be used. If a client has not passed a limit and has
bound as admin DN, then the limit will be considered unlimited. If
the client has not passed a limit and has not bound as admin DN,
then the limit will be that which was read from
ibmslapd.conf file. 0 = unlimited.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.27
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2391
DBNAME( 'TimeLimit' 'TimeLimit' )
ACCESS-CLASS critical
LENGTH 11 )
attributetypes=( 1.3.18.0.2.4.2384
NAME 'ibm-slapdTransactionEnable'
DESC 'If FALSE, globally disables transaction support; the server
will reject all StartTransaction requests with the response
LDAP_UNWILLING_TO_PERFORM.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2384
DBNAME( 'TransactionEnable' 'TransactionEnable' )
ACCESS-CLASS critical
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2499
NAME 'ibm-slapdUseProcessIdPW'
DESC 'If set to true the server will use the user login id associated
with the ibmslapd process to connect to the database. If set to false
the server will use the ibm-slapdDbUserID and ibm-slapdDbUserPW
values to connect to the database.'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.7
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2499
DBNAME( 'useprocidpw' 'useprocidpw' )
ACCESS-CLASS normal
LENGTH 5 )
attributetypes=( 1.3.18.0.2.4.2436
NAME 'ibm-slapdVersion'
DESC 'IBM Slapd version Number'
EQUALITY 2.5.13.5
SYNTAX 1.3.6.1.4.1.1466.115.121.1.15
SINGLE-VALUE
USAGE directoryOperation )
IBMAttributetypes=( 1.3.18.0.2.4.2436
DBNAME( 'slapdVersion' 'slapdVersion' )
ACCESS-CLASS normal
LENGTH 1024 )
The following is a list of attributes that are changed dynamically. You do not have to restart the server for these changes to take effect.
This information was developed for products and services offered in the U.S.A. IBM might not offer the products, services, or features discussed in this document in other countries. Consult your local IBM representative for information on the products and services currently available in your area. Any reference to an IBM product, program, or service is not intended to state or imply that only that IBM product, program, or service may be used. Any functionally equivalent product, program, or service that does not infringe any IBM intellectual property right may be used instead. However, it is the user's responsibility to evaluate and verify the operation of any non-IBM product, program, or service.
IBM may have patents or pending patent applications covering subject matter in this document. The furnishing of this document does not give you any license to these patents. You can send license inquiries, in writing, to:
IBM Director of LicensingFor license inquiries regarding double-byte (DBCS) information, contact the IBM Intellectual Property Department in your country or send inquiries, in writing, to:
IBM World Trade Asia Corporation LicensingThe following paragraph does not apply to the United Kingdom or any other country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF NON-INFRINGEMENT, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you.
This information could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the information. IBM may make improvements and/or changes in the product(s) and/or the program(s) described in this information at any time without notice.
Any references in this information to non-IBM Web sites are provided for convenience only and do not in any manner serve as an endorsement of those Web sites. The materials at those Web sites are not part of the materials for this IBM product and use of those Web sites is at your own risk.
IBM may use or distribute any of the information you supply in any way it believes appropriate without incurring any obligation to you.
Licensees of this program who wish to have information about it for the purpose of enabling: (i) the exchange of information between independently created programs and other programs (including this one) and (ii) the mutual use of the information which has been exchanged, should contact:
IBM CorporationSuch information may be available, subject to appropriate terms and conditions, including in some cases, payment of a fee.
The licensed program described in this document and all licensed material available for it are provided by IBM under terms of the IBM Customer Agreement, IBM International Program License Agreement, or any equivalent agreement between us.
Any performance data contained herein was determined in a controlled environment. Therefore, the results obtained in other operating environments may vary significantly. Some measurements may have been made on development-level systems and there is no guarantee that these measurements will be the same on generally available systems. Furthermore, some measurement may have been estimated through extrapolation. Actual results may vary. Users of this document should verify the applicable data for their specific environment.
Information concerning non-IBM products was obtained from the suppliers of those products, their published announcements or other publicly available sources. IBM has not tested those products and cannot confirm the accuracy of performance, compatibility or any other claims related to non-IBM products. Questions on the capabilities of non-IBM products should be addressed to the suppliers of those products.
All statements regarding IBM's future direction or intent are subject to change or withdrawal without notice, and represent goals and objectives only.
All IBM prices shown are IBM's suggested retail prices, are current and are subject to change without notice. Dealer prices may vary.
The following terms are trademarks of International Business Machines
Corporation in the United States, or other countries, or both:
| AIX | DB2 | IBM | OS/400 | SecureWay(R) | World Registry | z/OS |
Microsoft(R), MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation
UNIX is a registered trademark of The Open Group.
Other company, product, and service names may be trademarks or service marks of others.
Use this section to locate definitions of some of the IBM Directory product terms
Aliases Objects are of 'objectclass=aliasObject'. The mandatory attribute in this class, 'aliasedObjectName', contains the full DN of another directory object (the one to which the alias refers).
On the C API, by default, aliases objects are not dereferenced during a search operation. The client may request dereferencing using a flag on the command line. Aliases may be dereferenced when locating the base entry of the search. If the object specified as the base is an alias object, the object will be derefenced before beginning the search.
For example, an object with dn "cn=personOfTheWeek, o=Corporation, c=US" which has the attribute aliasedObjectName: "cn=personA, o=Corporation,c=US". With 'deref finding' set, a search base of "cn=personOfTheWeek, o=Corporation, c=US" is dereferenced to "cn=personA, o=Corporation,c=US". This now becomes the base for the search.
Another possibility is to dereference aliases during searching. In this case, the dn used as the base is the one given by the client, but alias entries found during the search are dereferenced.
An example of this might be a search for "cn=*week*" with a base of o=Corporation, c=US". While the located Node is "cn=personOfTheWeek, o=Corporation, c=US" this object would be dereferenced and the entry "cn=personA, o=Corporation,c=US" is returned as the search result.
A dereference of 'all' might also be used. This means that alias entries are dereferenced both when locating the search base and when objects are found during the search operation.
cn=Ben Gray,ou=editing,o=New York Times,c=US cn=Lucille White,ou=editing,o=New York Times,c=US cn=Tom Brown,ou=reporting,o=New York Times,c=US
LDAP DNs begin with the most specific attribute (usually some sort of name), and continue with progressively broader attributes, often ending with a country attribute. The first component of the DN is referred to as the Relative Distinguished Name (RDN). It identifies an entry distinctly from any other entries that have the same parent.
The search expressions can be used in combination with other group attributes.
Normal groups have an object class of 'GroupOfNames', 'GroupOfUniqueNames' or a user defined group. Access control groups have an object class of 'AccessGroup'.
Each group object contains a multivalued attribute consisting of member DNs. Groups cannot contain group DNs.
See Indexing rules.
The LDIF tool ldif is a shell-accessible utility that converts arbitrary data values to LDIF. It reads input values from standard input and produces LDIF records.
caseExactIA5Match caseExactMatch caseExactOrderingMatch caseExactSubstringsMatch caseIgnoreIA5Match caseIgnoreMatch caseIgnoreOrderingMatch caseIgnoreSubstringsMatch distinguishedNameMatch distinguishedNameOrderingMatch generalizedTimeMatch generalizedTimeOrderingMatch integerFirstComponentMatch integerMatch objectIdentifierFirstComponentMatch objectIdentifierMatch octetStringMatch telephoneNumberMatch telephoneNumberSubstringsMatch uTCTimeMatch
The general format for a referral is: ldap[s]://hostname:port. Typically the format for a referral to a nonsecure server is: ldap://hostname:389 and to a secure SSL server is: ldaps://hostname:636. See Referrals for additional information.
IBM Attribute Type Description
Matching Rule Description
Name Form Description
Attribute Type Description
Object Class Description
DIT Structure Rule Description
DIT Content Rule Description
LDAP Syntax Description
OID
Matching Rule Use Description
Boolean - TRUE/FALSE
Binary - octet string
INTEGER - integral number
Generalized Time
IA5 String - case-sensitive string
Directory String - case-insensitive
string
UTC time
Telephone Number
DN - distinguished name